At Dragos, we continually enhance the industrial device data, threat analytics, and response playbooks in our cybersecurity solution so that our customers can confidently understand and manage both what, and who, are in their OT environment. These updates, in the form of Knowledge Packs, are the codification of the expertise of our OT practitioners – who are themselves control system engineers, incident responders, Red Teamers, threat hunters, intelligence analysts, cyber risk advisors, and vulnerability researchers. This month we’re excited to share some important updates related to the Dragos Platform’s capabilities and the ability to put even more of that expertise at our customers’ fingertips.
Since our earliest days, Dragos has been recognized for its strength related to ICS/OT threat intelligence, and from Day 1 this industry experience has been codified into the foundational components of both our products and services. Not only did this include threat detection – providing our customers with powerful threat hunting capability and expert guidance in the form of prescriptive playbooks that security analysts could use during investigation and response to threats in defending their environments, it also informed how we approach asset visibility as a primary feature of the Dragos Platform. Although it’s important to have an accurate inventory of connected devices on your network, being able to see those device communications in a manner that visually indicates critical details and potential adversary activity adds a dimension that cyber defenders now expect.
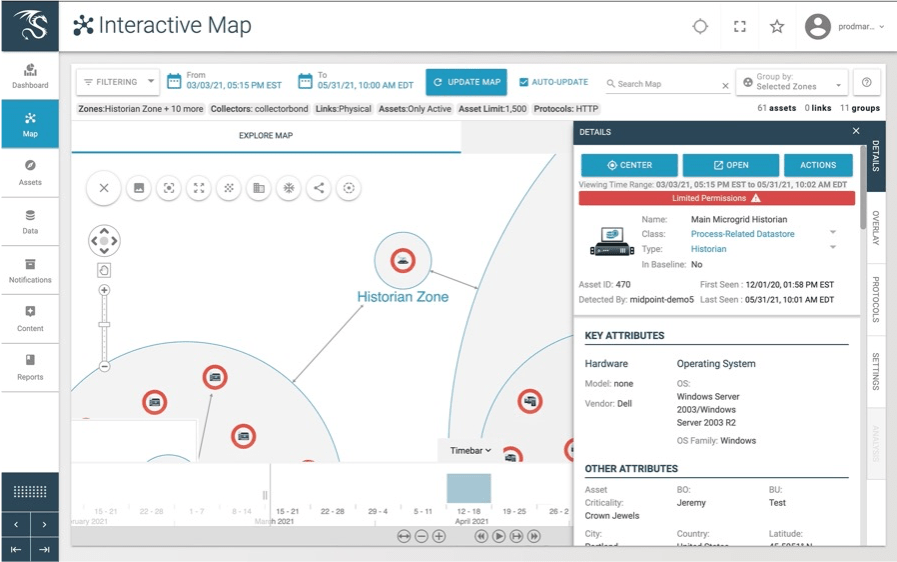
More recently, there has been an increase in the number and type of certain attacks that make public headlines. Quite often asset owners are operating in the dark when it comes to knowing which of their systems are vulnerable, but more importantly – which of the vulnerabilities need prioritized attention. With this in mind, the teams at Dragos have been working hard to bring a new capability to our customers – integrated OT vulnerability management!
This new release provides what we believe is the only corrected, enriched, and prioritized OT guidance that allows customers to manage the full lifecycle of specific vulnerabilities in their environment, showing historical disposition – through continuous, automated collection and analysis. Decide at a glance which vulnerabilities to assign valuable resources to with simple “Now, Next, Never” recommendations. Arm your teams with tools to prepare for and respond to audits or comply with industry regulations like NERC CIP.
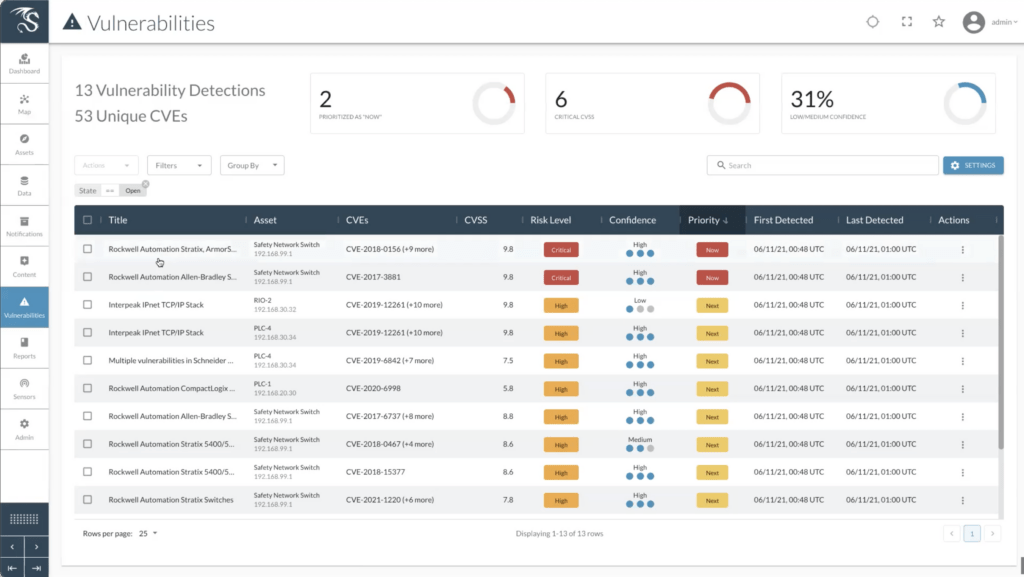
For a more detailed review of how powerful and unique this new feature is, check out our vulnerability management web page, grab a copy of the related whitepaper, and consider joining the announcement webinar on July 22nd at 1:00 pm EDT. We are excited to have a panel of security leaders from Berkshire Hathaway Energy, Boardwalk Pipelines, and INVISTA join us to share their firsthand perspective on the challenges facing industrial companies to protect their environments, and our own Chris Carlson, VP of Product will provide a walk through of the latest Dragos Platform updates.
And while we are confident about the detection capabilities of the Dragos Platform, results from the recent MITRE Engenuity ATT&CK® Evaluations for Industrial Control Systems (ICS) provide strong independent evidence of just how much value our customers can expect. We’ve published those results, prepared a whitepaper retrospective with insights and technical background, and invite you to register for the upcoming webinar on July 29th at 1:00 pm EDT where experts Ben Miller – VP of Professional Services and R&D, and Austin Scott – Principal ICS Security Penetration Tester, will take the audience through an informative overview of the evaluation.
For more information about how Dragos can help address your ICS/OT cybersecurity challenges, talk to one of our experts or request a demo.
Ready to put your insights into action?
Take the next steps and contact our team today.