Welcome back to “The Hunt,” our blog series offering in-depth insights and strategies for defending against sophisticated cyber risks threatening OT environments. This blog focuses on VOLTZITE, a threat group targeting industrial control systems (ICS) environments across critical infrastructure that Dragos’s OT Cyber Threat Intelligence has tracked since early 2023. The analysis and reporting were published at various stages in Dragos WorldView. Volt Typhoon, which overlaps with VOLTZITE, made headlines after the Cybersecurity and Infrastructure Security Agency (CISA) released advisories in May 2023 and February 2024 alerting critical infrastructure of the increased threat.
At Dragos, the OT Watch team actively hunts for threats like VOLTZITE utilizing the Dragos Platform. This blog details our proactive approach to uncover VOLTZITE activities across customer networks, emphasizing the essential role of human expertise tied to OT cybersecurity technology via threat hunting.
Tracking VOLTZITE Threat Group Activity
Since the beginning of 2023, the Dragos OT Cyber Threat Intelligence team has been closely monitoring the activities of the VOLTZITE threat group and the significant potential to impact critical infrastructure systems. This threat group is known for their “living off the land” (LOTL) techniques, making them especially difficult to detect.
Get the Complete VOLTZITE Threat Analysis
Download our OT Cybersecurity Year in Review to get a more detailed analysis of VOLTZITE threat group activity.
Download the ReportHunting VOLTZITE with Dragos OT Watch
Sophisticated threat groups like VOLTZITE are increasingly utilizing LOTL techniques and obfuscating their traversal through a network. Therefore, it is imperative that hunting strategies also mature with adversarial tradecraft and focus on the TTPs of adversary activity. Focusing threat hunting efforts on VOLTZITE TTPs not only enhances detection efforts against the detection of VOLTZITE, but the detection of other threat group activity as well, as there are overlaps between adversary tradecraft, especially when it comes to use of LOTL techniques. In addition to behavioral-based hunting leads, relevant and timely indicators of compromise (IOCs) can also serve a vital role in a robust threat detection strategy.
In late 2023, leveraging the Dragos Platform, OT Watch investigated activities within a customer’s network that mirrored those typically seen in VOLTZITE attacks. The investigation employed threat hunt analytics to pinpoint tactics, techniques, and procedures (TTPs) linked to this notorious group.
OT Watch threat hunters began with NetFlow analysis which revealed established HTTPS connections to a known active VOLTZITE command and control server. All traffic took place over TLS v1.2 port 443. This communication was bidirectional and resulted in 3.89 MB exchanged between the hosts. The initiator of the established connection and follow-on bidirectional network communication was the malicious C2 node.
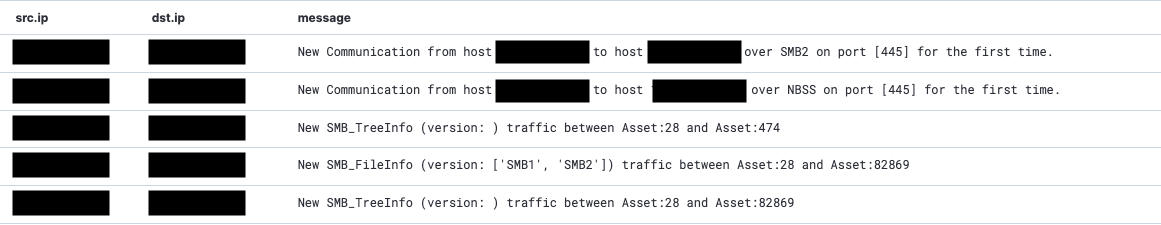
The hunt quickly revealed that VOLTZITE had exfiltrated GIS server data from the IT network, and attempts at SMB traversal were detected. Given the proximity of activities to critical OT systems, OT Watch promptly escalated the matter to the customer for an immediate response. These findings also highlighted an opportunity for the customer to address broader architectural security concerns at the OT-IT boundary.
While there was no evidence of adversary access to assets within the OT environment, activity adjacent to the OT network and IR analysis found evidence of adversary discovery actions that included focus on SCADA-related information. This was seen in the Dragos Platform as SMB traversal as the activity group pivoted within the environment looking for what is hypothesized to be not only information about the environment but also further means for persistence.
Expanding OT Watch Threat Detection Efforts
Taking the success of the threat hunt and the detailed understanding on the tactics of this threat group provided by the Dragos OT Cyber Intelligence team, OT Watch extends lessons learned from threat hunting findings back into the Dragos ecosystems for benefit across our customer base.
- OT Watch extended the hunt across all relevant OT Watch customers.
- The Dragos Intelligence team enhanced the effort by analyzing Neighborhood Keeper data for indications of VOLTZITE behaviors and then notifying impacted parties anonymously.
- Dragos threat detections engineers developed high-fidelity detections back into the Platform deployed via Dragos Knowledge Packs for continuous monitoring.
The overall response to the VOLTZITE threat highlights the importance of coordinated efforts and the advantage of ICS/OT capabilities unique to Dragos. This engagement not only addressed a complex threat but also strengthened the protective measures across critical infrastructure customers.
For additional coverage, OT Watch also runs exploratory and experimental hunts for VOLTZITE behaviors. These hunts are based on Dragos Intel-fed queries that aren’t yet suitable for platform detections because of their potentially high false positive rate but are still helpful for our team of expert threat hunters to analyze as these may lead to the discovery of stealthy TTPs utilized by adversaries like VOLTZITE. A few examples are:
- Hunting for local directories with .zip files named with a single letter or digit. This a TTP used by VOLTZITE for exfiltration staging observed as recently at this past Fall.
- Hunting for use of the ‘netsh portproxy’ command. This is a known Command and Control TTP used by the threat group.
- Hunting for NTDS.dit files in local temp directories or other directories that this database file would not normally be found. This is a known credential theft and persistence TTP of VOLTZITE.
Proactive Threat Detection & Threat Hunting with Dragos
Facing threats like VOLTZITE reveals the urgent need for vigilant, advanced threat detection and proactive threat hunting—hallmarks of Dragos’s approach. Partnering with us means benefiting from:
- Premier OT cyber threat intelligence and OT security expertise.
- The Dragos Platform’s unmatched threat detection and response capabilities.
- A community-driven defense enabled by Neighborhood Keeper, strengthening security across the board.
If you are interested in learning more about protecting against VOLTZITE with the Dragos Platform and OT Watch, please contact us.
Request a Platform Demo
Ready to put your insights into action?
Take the next steps and contact our team today.

