Dragos Platform Scores High on Visibility and Analytics
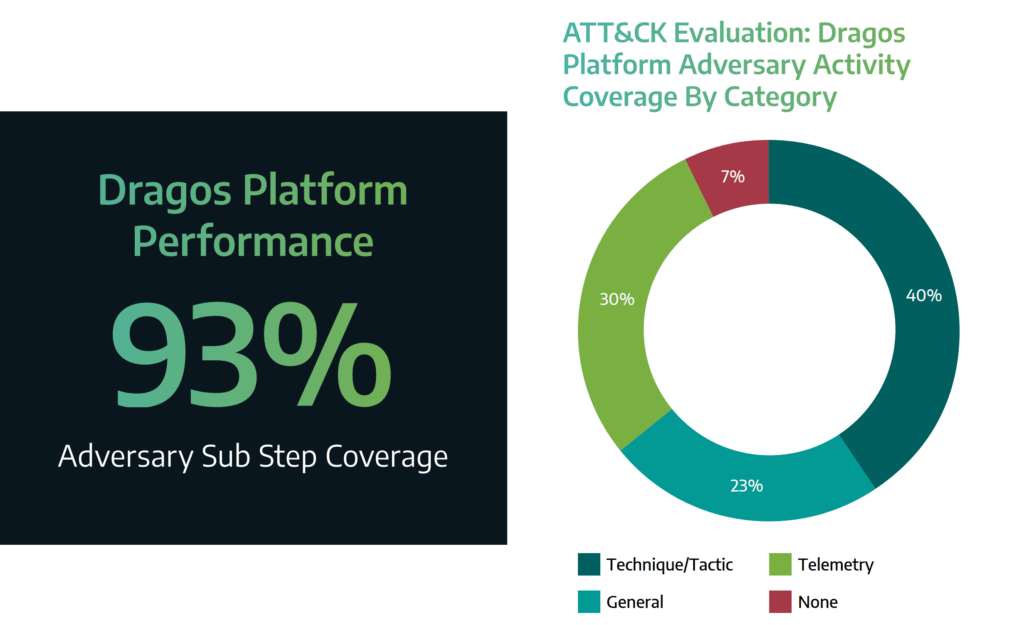
The 2021 MITRE Engenuity ATT&CK® Evaluations for Industrial Control Systems (ICS) have been officially released! You can view the official results of the ATT&CK Evaluations on the MITRE Triton ICS Evaluation 2021 webpage. We’re excited to announce that in this first-ever evaluation by the MITRE Engenuity team, the Dragos Platform scored high in the Visibility (93%) category and highest amongst participants in the Analytics (63%) category – which are measures used to assess our ability to detect adversary activity.
Visibility, the MITRE term for combined raw telemetry logs and analytic detections, is the foundation of the pyramid that offers the broadest understanding of threat activity. But, without enough proper context of the raw telemetry logs, an analyst may struggle to understand the meaning behind the attack. As you move up the pyramid, the analyst needs more context to properly know how to respond or restore operations. MITRE ATT&CK creates this context via techniques. The Dragos Platform had 63% analytics coverage, which is the proportion of sub-steps that contained a detection that provides additional context in the form of MITRE ATT&CK techniques. This context gives analysts a significant advantage by providing ICS and threat-relevant information that allows them to move faster, be more efficient, and make well-informed decisions. These results validate the effectiveness of Dragos’s intel-driven approach.
If you’d like to get a better understanding of how MITRE calculates this data point, we invite you to download our whitepaper, “2021 MITRE Engenuity ATT&CK® for ICS Evaluation: A Retrospective of the Emulated Attack“.
Some Background on The ATT&CK Framework and First Evaluation
This is the MITRE Engenuity team’s first evaluation of the ICS threat detection market. One of the challenges we face in ICS cybersecurity is the lack of detection and collection capability within most ICS environments. MITRE Engenuity ATT&CK Evaluations are intended to help vendors and end-users better understand a product’s capabilities in relation to MITRE’s publicly accessible ATT&CK for ICS framework, which is a curated knowledge base of adversary tactics, techniques, and procedures based on known threats to industrial control systems. ATT&CK for ICS provides a common language to describe the tactics and techniques that cyber adversaries use when attacking the systems that operate some of the nation’s most critical infrastructures, including energy transmission and distribution plants, oil refineries, wastewater treatment facilities, and more. As a true community-led effort, more than 100 participants from 39 organizations reviewed, provided comments, or contributed to the ATT&CK for ICS framework which was first launched in early 2020.
For the ATT&CK Evals, MITRE Engenuity used the MITRE ATT&CK for ICS knowledge base to emulate the tactics, techniques, and procedures (TTPs) associated with the TRISIS/TRITON malware. The malware was the first-ever tailored to attack safety systems including those found within oil and gas and electrical facilities in the Middle East, Europe, and North America. You can view these TTPs on an interactive matrix on our own MITRE ATT&CK for ICS webpage.
The Dragos Platform in Action
The Dragos Platform is a network-based cybersecurity software technology that identifies ICS assets and their communications to provide an inventory and topology, identify and manage vulnerabilities, detect malicious activity, and provides guidance to investigate incidents. In relation to the MITRE ATT&CK evals, our focus is on measuring the high-value composite analytics that map to the MITRE ATT&CK for ICS framework and the specific context of the critical ICS assets the actions are taken against.
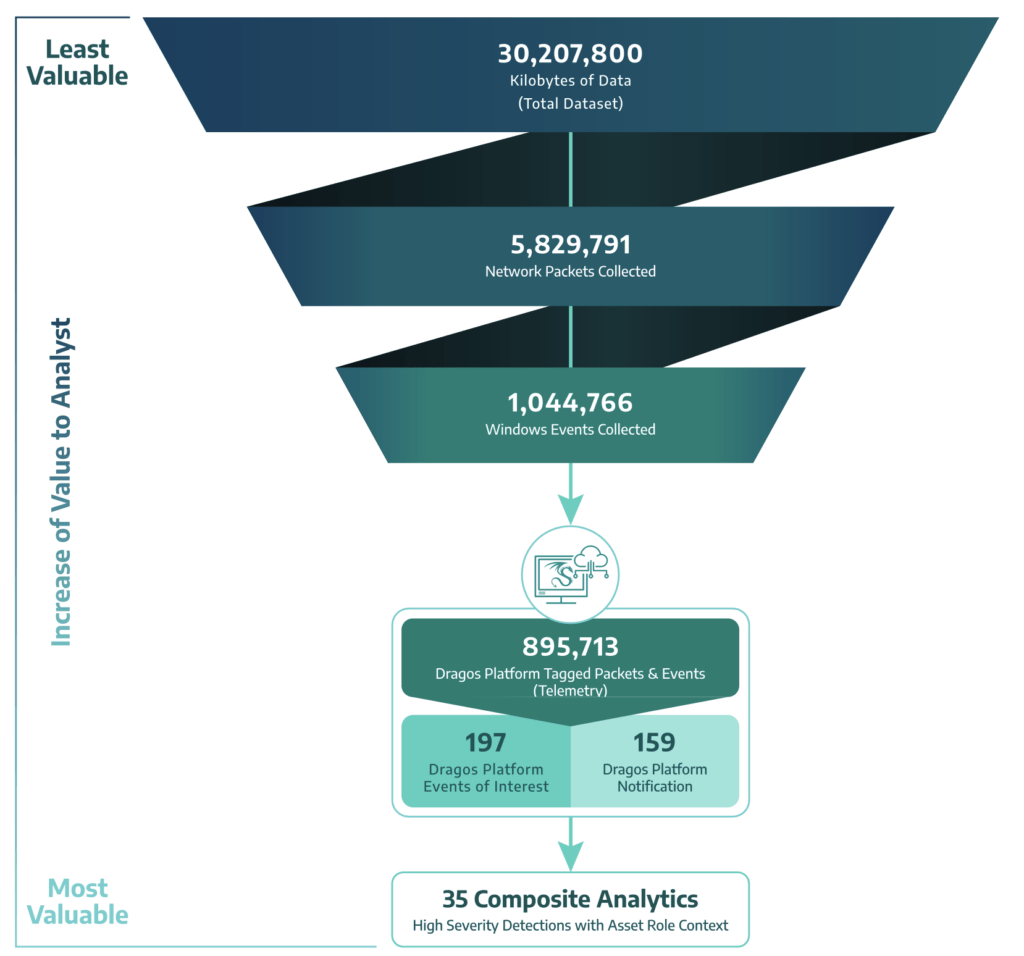
The following graphic depicts how the Dragos Platform worked through the MITRE Evaluation dataset to provide valuable events and notifications.
Looking to the Future of ICS Threat Detection
One of the challenges we face in ICS cybersecurity is the lack of detection and collection capability within most ICS environments. The MITRE ATT&CK evaluation represents a complete data set for an end-to-end attack on an ICS system, and testing cybersecurity technology platforms against it improves the community’s understanding of how to detect ICS-tailored threats. We welcome any opportunity to help build the community knowledge base and are confident that participating in these assessments drives our industry forward. The evaluation has provided numerous learning opportunities to identify key focus areas for improvement for ICS security.

To view how the ATT&CK Evaluations techniques and behaviors mapped to current profiles of known Activity Groups targeting ICS environments, view our interactive ATT&CK for ICS matrix at: www.dragos.com/mitre-attack-for-ics/.
Ready to put your insights into action?
Take the next steps and contact our team today.

