The Most Effective OT Cybersecurity Platform
Achieve unparalleled visibility into your OT assets, threats and vulnerabilities with the Dragos Platform. Enriched with industry leading threat-intelligence, the Platform was built by defenders for defenders, our platform delivers actionable insights to tackle any emerging challenge.
A Cybersecurity Platform Built for OT Environments
Our OT-native cybersecurity technology supports uptime and productivity in industrial environments. The Dragos Platform was built to monitor networks and detect threats without disruption, addresses vulnerabilities without shutdowns, and respond to adversaries confidently.
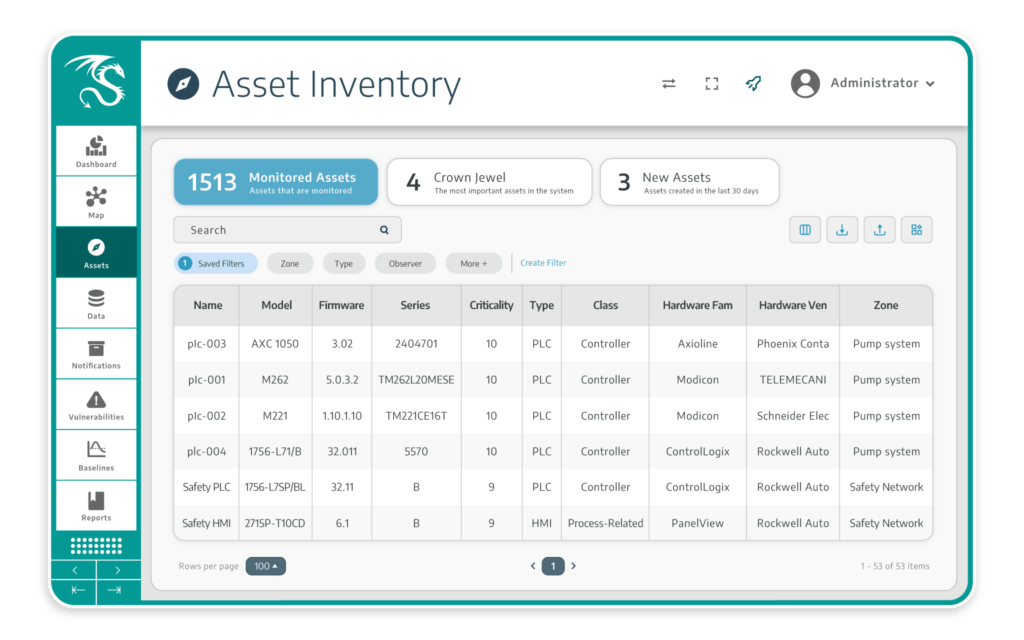
Asset Visibility
Automatically discover and profile all assets in OT environments – OT system, IT, and IoT devices – to build detailed inventories and track changes efficiently. Our passive-first approach lays a foundation for a robust OT cybersecurity program aligned with operational requirements.
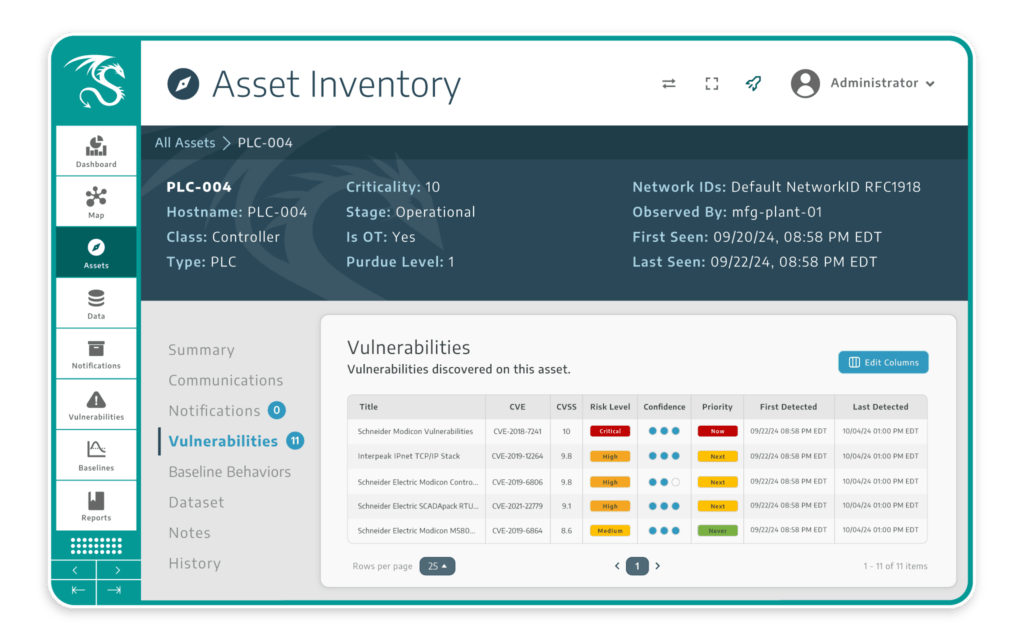
Risk-Based Vulnerability Management
The Dragos Platform is the only OT cybersecurity solution to deliver OT-corrected and enriched vulnerability analysis with “now, next, never” guidance that lets you manage the full lifecycle of vulnerabilities in your environment.
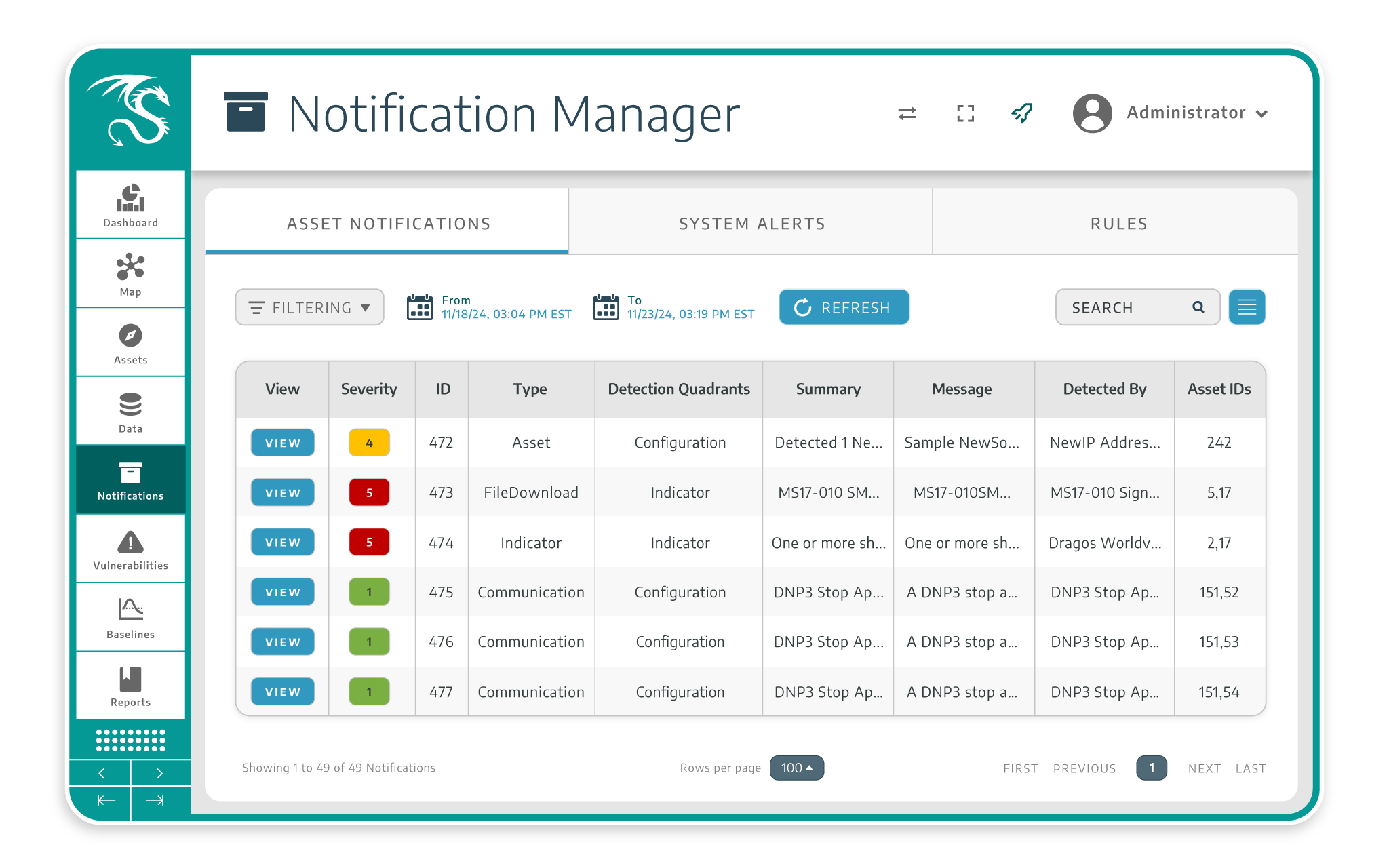
Intelligence-Driven Threat Detection
While other tools stop at anomalies and common IOCs, Dragos elevates detection with proprietary threat intelligence integrated into the Dragos Platform. Customers benefit from regularly updated modeling, configuration, and threat behaviors and IOCs based on real world activity from OT focused threat groups.
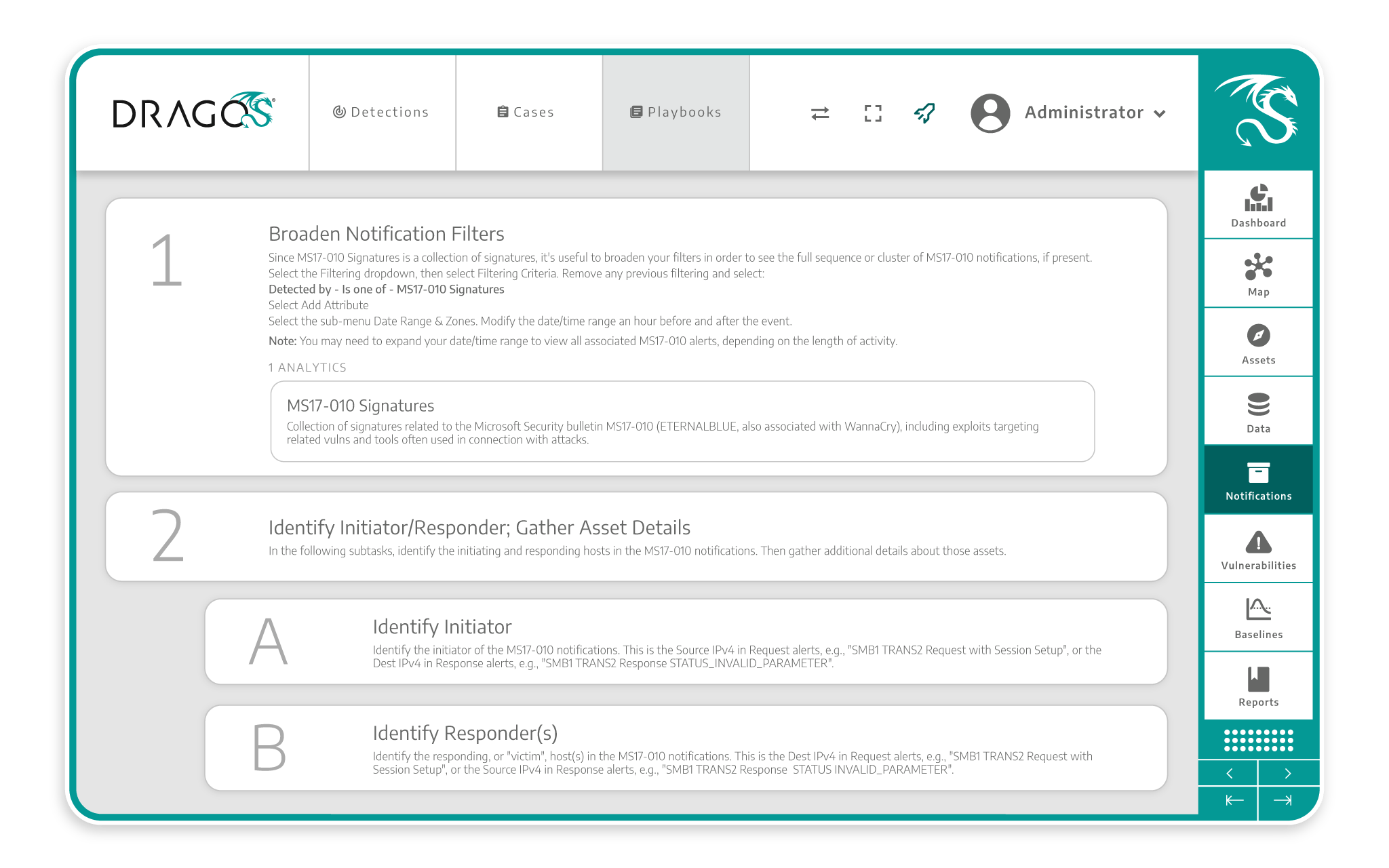
Response Playbooks
Simply launch investigations based on alerts and utilize expert-authored playbooks that guide your security team through every step. These playbooks are designed to reduce response times and enhance workflow efficiency, streamlining your security operations.
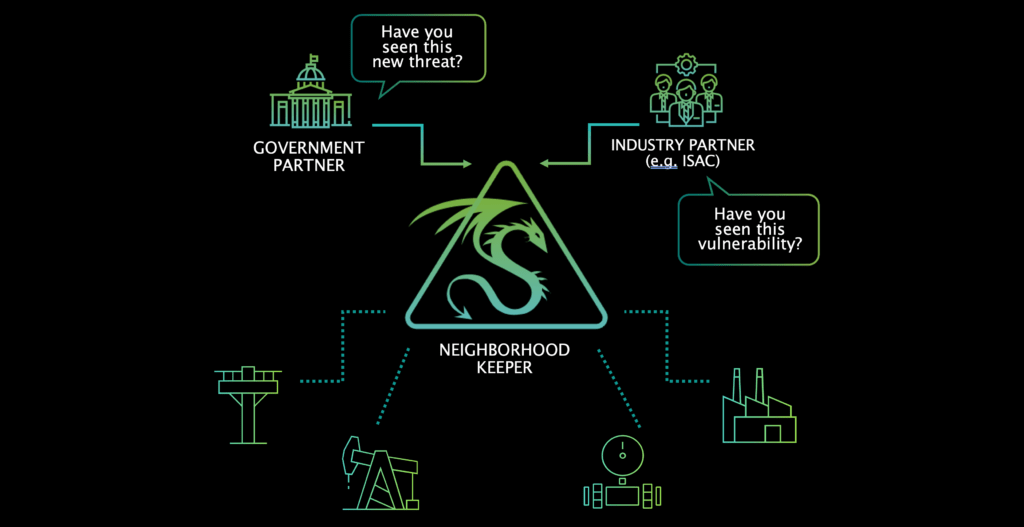
Neighborhood Keeper
Fortify your defense through shared intelligence of real-world threats and vulnerabilities that impact assets across the broader industrial community for a stronger collective defense.
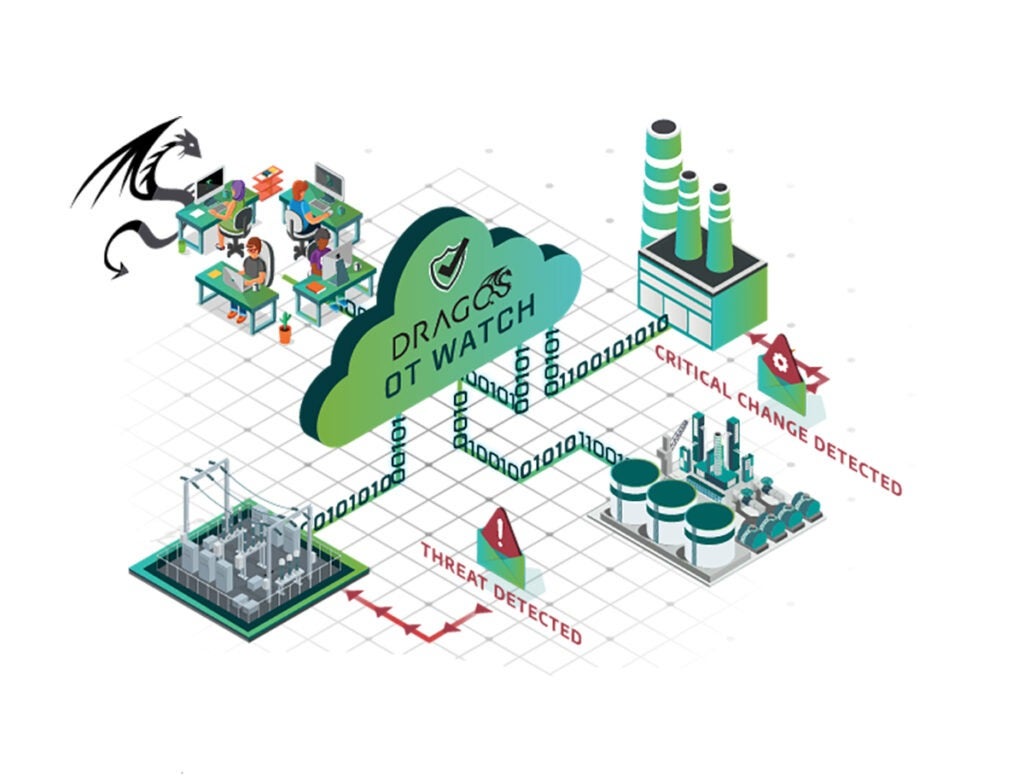
OT Watch
Dragos OT Watch delivers the industries only threat-hunting-as-a-service, to actively hunt adversaries within a customer’s environment and provides critical escalations to add another layer of human protection.
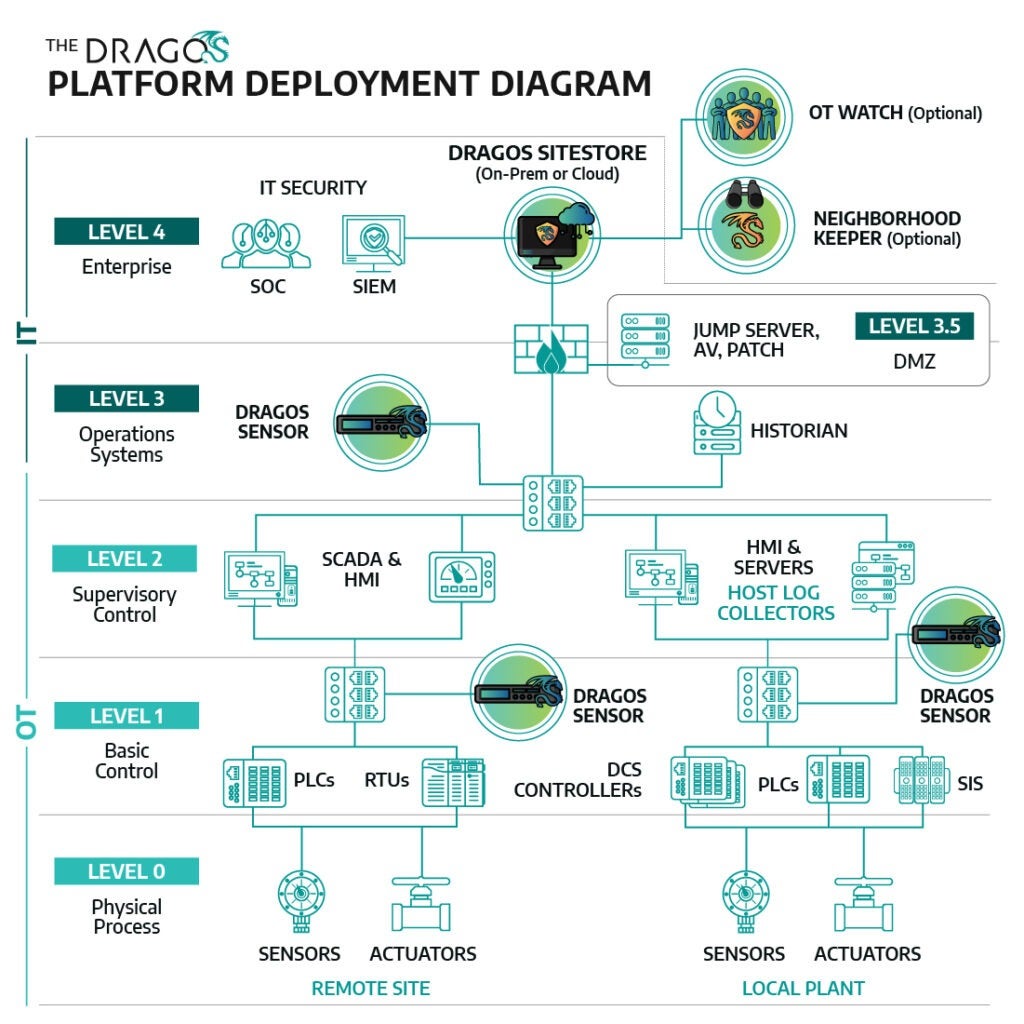
Flexible deployment
Dragos supports flexible deployment options—virtual, on-premises, or cloud-based – for your unique environments. The platform provides centralized management and reporting capabilities across multi-site and mulit-organizations for enhanced security.
Built By Defenders, For Defenders
Visibility gaps are still a top cybersecurity assessment finding.
What Our Customers Say
Featured Technology Partners
See the Dragos Platform in Action
Take the next step to protect your ICS environment now with a free demo


