Welcome to “The Hunt,” a blog series focused on the critical role of threat hunting within operational technology (OT) environments. These environments are vital to our critical infrastructure, requiring not just defensive measures but proactive strategies to identify and mitigate cyber threats before they negatively impact operations. Throughout this series, we will explore the complexities of OT cybersecurity, dissect the characteristics of advanced threats, and share expert strategies for effective threat detection and neutralization.
Aimed at both seasoned security professionals and newcomers to the field, “The Hunt” offers valuable insights into safeguarding our indispensable systems and services against cyber threats.
What Is Threat Hunting?
According to the SANS Institute, “Threat Hunting is a proactive, data-driven methodology that applies an iterative search for specific events within enterprise data, going beyond standard detection capabilities.” At Dragos, the Dragos Platform goes beyond standard detection by finding threat behaviors driven by our adversary research and external threat hunting far beyond customer network environments across the entire kill chain. For this blog series’ purposes, we’ll focus on threat hunting within OT networks, which is critical against the advanced tools that adversaries use today.
In OT environments, this involves a detailed analysis within networks and systems controlling physical processes across various industries, such as electric, oil and gas, manufacturing, and the federal governments. It’s best-done utilizing OT network visibility and monitoring to provide the activity logging, threat detection, and telemetry that supplies a good hunt. Utilizing frameworks like the MITRE ATT&CK for ICS (Industrial Control Systems), threat hunters can apply a structured approach to identify tactics, techniques, and procedures (TTPs) used against OT systems to enhance the effectiveness of their hunt.
The goal of persistent threat hunting at Dragos is to protect critical systems from disruptions or damage by finding, neutralizing, and anticipating potential cyber threats before they cause negative impacts.
OT Is Not IT: Adapting Threat Hunting for ICS/OT Environments
Threat hunting practices in IT do not always mirror those within industrial environments. Industrial control systems (ICS) and OT environments introduce unique challenges and raise the stakes. Unlike IT threats, which typically risk data loss or financial impact, OT threats can directly affect the physical world. This critical distinction underscores the importance of securing OT systems as a matter of operational resilience, public safety, and global security. Tailoring threat hunting strategies to accommodate the specific needs of OT environments requires a deep understanding of industrial control systems, their devices and protocols, and the operational intricacies that distinguish them from traditional IT systems.
Adversaries targeting OT environments often employ sophisticated, discrete methods designed to blend into daily operations. Their deep understanding of industrial systems can make detection challenging without tailored visibility into the environment and specialized threat hunting skills. Recognizing and countering these types of threats requires the right technology, plus a nuanced approach that can only come from experienced professionals.
Proactive threat hunting in OT is essential for several reasons:
- Early Detection: Hunting helps quickly uncover potential network intrusion activity evading standard defenses, minimizing adversary dwell time, and mitigating the impact of a cyber-attack.
- Rapid Response: Swiftly addressing potential threats to equip incident responders minimizes the risk of operational downtime or safety incidents.
- Misconfiguration Identification: Expert threat hunters can uncover vulnerabilities and misconfigurations that automated systems might miss, helping to reduce the potential attack surface.
- Proactive Cyber Defense: Proactive threat hunting can find malicious behavior that can evade standard cyber defenses, showcasing the need for human insight to identify subtle signs of compromise that might be overlooked by automated systems.
How it Works?
Threat hunting in OT environments is becoming increasingly critical. Empowering organizations to proactively enhance their cyber defenses ensures the security and resilience of critical infrastructure. Integral to achieving this is leveraging advanced capabilities like the Dragos Platform, the OT-native network monitoring and visibility platform.
Dragos’s threat-hunting-as-a-service, OT Watch, adds an additional layer of protection on top of the Dragos Platform with proactive and persistent threat hunting within customer environments.
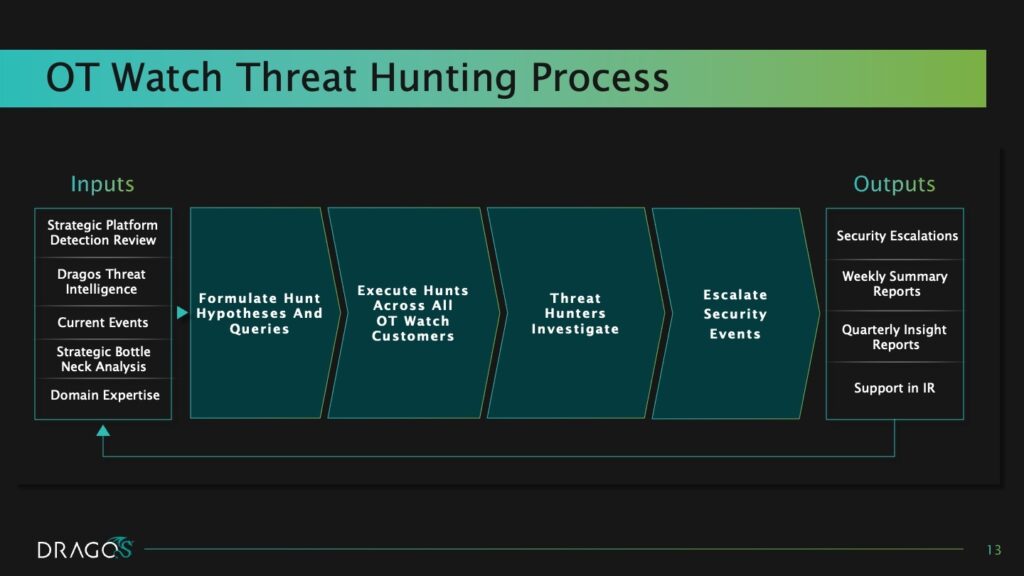
Dragos OT Watch threat hunters develop hunting hypotheses from key inputs including:
- Detections from the customer’s Dragos Platform instance.
- Dragos’s proprietary adversary threat intelligence built from tracking adversaries, deconstructing malware, analyzing vulnerabilities, and engineering threat detections, all with a focus on industrial operations.
- Expertise in understanding how adversaries attempt to blend into OT network activity in ways that evade automated detection.
- Once hypotheses are formed, hunters deploy queries to investigate across the entire OT Watch customer fleet.
- When the hunt yields results, hunters escalate findings to affected Dragos Platform customers.
In Conclusion
Dragos OT Watch is the ideal companion to the Dragos Platform, which provides comprehensive OT network visibility, vulnerability management and threat detection needed to monitor and protect industrial control systems (ICS). ICS network visibility and monitoring is a critical control in building a solid cyber defense against potential industrial cyber threats, as noted in the SANS Institute’s five critical controls for world-class OT cybersecurity. Download our free guide to learn more about these five critical controls.
Stay tuned for the next blog in our series. We’ll offer additional insights and guidance on the complex task of threat hunting in OT environments.
Request a Platform Demo
Ready to put your insights into action?
Take the next steps and contact our team today.
