Advanced Threat Hunting for Industrial Environments
Advanced Threat Hunting with OT Watch
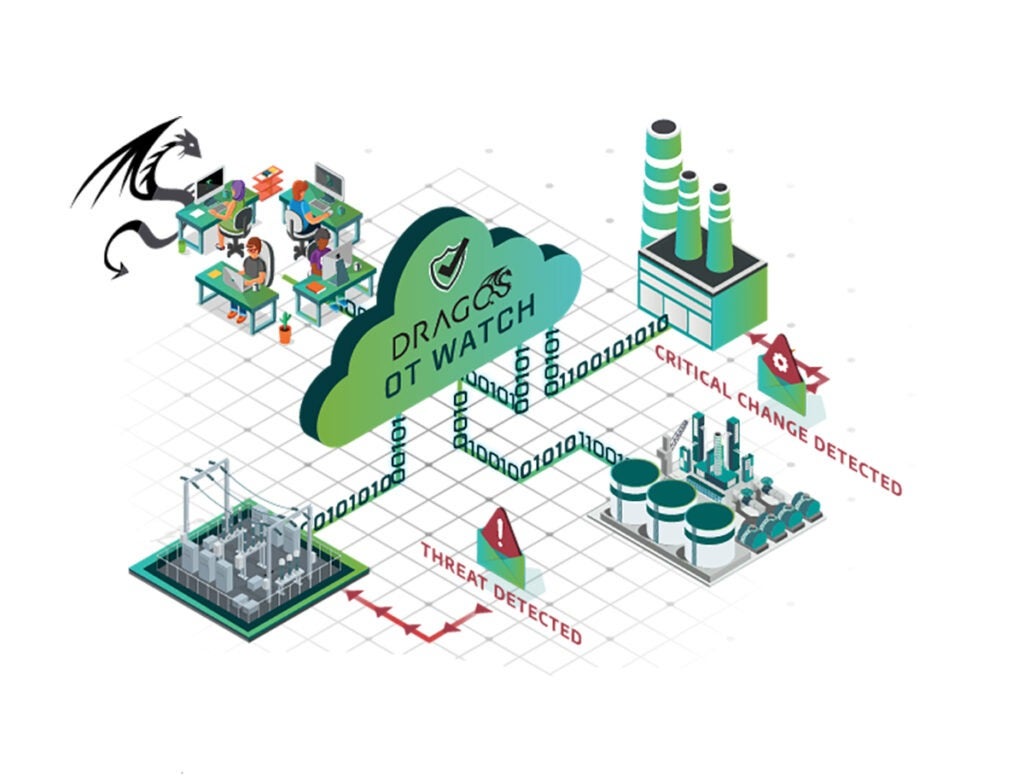
Dragos OT Watch provides advanced industrial threat hunting for Dragos Platform customers delivered by industry leading industrial control systems (ICS) security practitioners. Our team’s hands-on experience in responding to significant OT threats and cyber incidents equips you with the skills to protect your OT environments proactively. OT Watch identifies adversaries operating within customer networks and offers actionable guidance to enhance both industrial operations and OT cybersecurity.
Why Threat Hunt in Operational Technology Environments?
Threat hunting in OT environments addresses risks to physical industrial control systems and operations, that come with distinct challenges requiring a different approach than threat hunting in IT environments. OT threats can have immediate real-world consequences, making specialized knowledge of industrial systems critical.
How Does Dragos OT Watch Work?
 OT Watch generates hunting leads from a combination of active detections from the Dragos Platform, proprietary threat intelligence, and global security trends to identify potential threats in industrial networks. Our experts are additionally focusing on critical areas within the customer environment to hunt where adversaries focus.
OT Watch generates hunting leads from a combination of active detections from the Dragos Platform, proprietary threat intelligence, and global security trends to identify potential threats in industrial networks. Our experts are additionally focusing on critical areas within the customer environment to hunt where adversaries focus.
 Hunting leads are distributed across our client network, enabling targeted and exploratory hunts. Findings lead to in-depth investigations and the development of new detection methods.
Hunting leads are distributed across our client network, enabling targeted and exploratory hunts. Findings lead to in-depth investigations and the development of new detection methods.
 Critical findings prompt immediate escalation, empowering customers to act quickly and effectively against security threats.
Critical findings prompt immediate escalation, empowering customers to act quickly and effectively against security threats.
Benefits of Dragos OT Watch
Contact Us





Adversaries using LOTL techniques don’t always stand out.
Expert-Driven Threat Hunts
Dragos OT Watch’s unmatched ICS expertise elevates your OT security. Led by premier ICS security experts, our team’s vast experience in combating significant OT threats empowers proactive protection. Utilizing the Dragos Platform, we specialize in identifying network adversaries, offering actionable guidance to enhance your industrial operations and cybersecurity
The Dragos OT Watch team, enabled by Dragos Platform technology, provides a level of visibility into our assets and threats that we did not have the expertise nor the bandwidth to do on our own.
See the Dragos Platform in Action
Take the next step to protect your ICS environment now with a free demo