Expert OT Cybersecurity Services to Safeguard Your Operations
Dragos OT Cyber Services: Assess, Plan & Respond
Dragos works to assess your defenses, proactively define and test incident response plans, and help create a prioritized program for improvement. Our OT incident responders are ready to help if you suffer a critical incident. With a Dragos Rapid Response Retainer you can reduce delays and expedite remediation efforts.
Explore our full range of professional services
Urgent Incident Response Services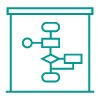



Dragos Rapid Response Retainer
Expert responders to create a more efficient, effective response to speed resolution.
What’s Included with Incident Response:
- Rapid Response Retainers: Reduce costs and speed response by preclearing contracts and helping to refine Incident Response Plans.
- Expert Responders: Work with experts in crisis management, in-depth analysis, and investigations.
- Workshops: Build and refine effective Incident Response Plans.
- Tabletop Exercises: Test plans and identify areas to improve .
Tabletop Exercises
Gain a better understanding of your team’s OT incident response capabilities against a realistic cyber-attack with a tabletop exercise. Designed to demonstrate how a realistic attack might occur in your OT environment, tabletop exercises help you assess your cybersecurity posture using scenarios tailored to your organizational risks or customized to meet your needs.
What’s included in Tabletop Exercises:
- Test and strengthen your current incident response plan
- Reduce the impact of an industrial cyber event
- Improve cross-functional communication and team relationships
- Get knowledge transfer from an experienced team
Assessments: Discover Your Strengths and Weaknesses
Understanding your most critical OT systems and the potential consequences of a cyber incident or attack on those systems is essential for prioritizing your protection, detection, and response efforts.
What’s included with Assessments:
- OT Cybersecurity Assessment (OTCA): Through network analysis, documentation reviews and staff interviews, Dragos provides tactical and strategic recommendations to enhance OT security. Document assets and networks, understand current vulnerabilities and compromises, and evaluate defensible architecture. We offer four options, including a TSA-aligned CADR evaluation.
- Network Vulnerability Assessment: Dragos identifies potential security weaknesses through systematic information gathering and configuration review.
- Network Penetration Testing: Dragos actively attempts to exploit these vulnerabilities to validate security controls. This with the network vulnerability assessment helps organizations discover security gaps, prove the effectiveness of existing defenses, and receive actionable recommendations to strengthen their OT security posture against potential attacks.

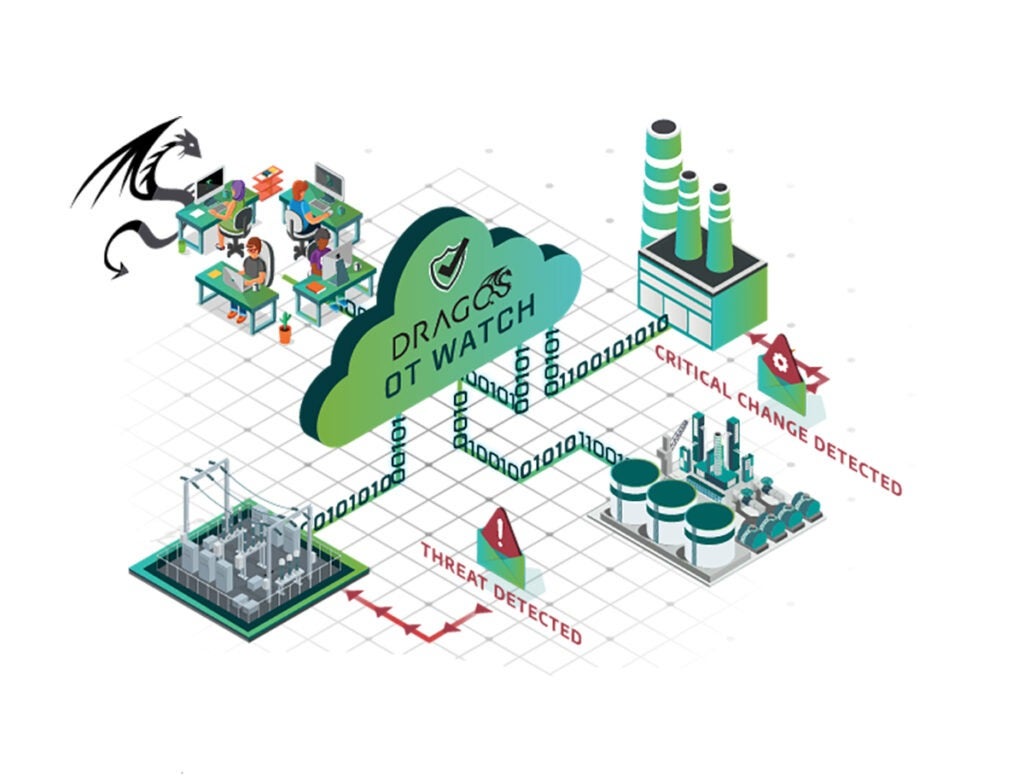
Threat Hunting: Find Elusive Threats with OT Watch
Dragos OT Watch is a service exclusively for Dragos Platform customers. We provide a dedicated team of expert OT hunters who identify advanced tools and adversaries hidden in your environment.
What’s Included with Dragos OT Watch:
- Persistent Threat Hunts: Formulate new hunt hypotheses and analytics based on the latest threat intelligence
- Critical Escalations: Access details and context of results that require follow up by your security operations
- Insight Reports: Receive document hunt results on a monthly basis
The 2025 OT Cybersecurity Report is Now Available
What Our Customers Say
Get Started
Whether you’re starting your quest or strengthening your current program, Dragos is here for you every step of the way. Take the first step to protect your OT environment with a free demo.