Expert-Driven OT Network Visibility & Monitoring
Dragos Platform with OT Experts at the Helm
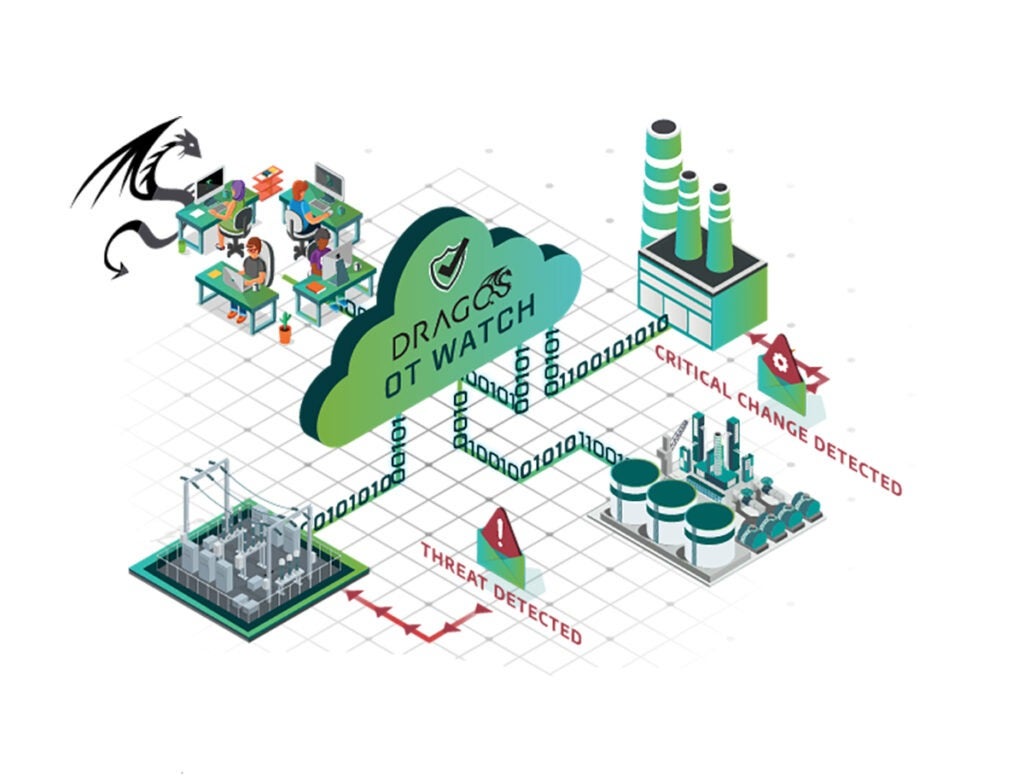
Dragos OT Watch delivers more than just tools – it delivers outcomes. Our experts operate the Dragos Platform on your behalf, helping you enhance visibility, identify threats, and strengthen your security posture. With analysts and threat hunters embedded in your environment, you get the benefits of deep operational technology (OT) expertise, tailored guidance, and continuous tuning, without adding to your team’s workload.
Bridging the Gap Between Alerts & Action
In OT environments, alerts alone aren’t enough. You need context, relevance, and the ability to act fast. Traditional IT-centric models often fall short in industrial control systems (ICS), where uptime, safety, and reliability are non-negotiable. Dragos OT Watch is built to close that gap: combining deep protocol visibility, expert-led threat hunting, and continuous improvement of your monitoring strategy to make OT cybersecurity more effective and manageable.
Extend Your Security Team with OT Experts
 By aligning OT asset visibility and network monitoring with threat intelligence and security expertise, OT Watch helps you prioritize the risks that matter most. Our analysts don’t just manage alerts – they help you understand what to do, and how to prioritize response, all grounded in the Dragos Platform.
By aligning OT asset visibility and network monitoring with threat intelligence and security expertise, OT Watch helps you prioritize the risks that matter most. Our analysts don’t just manage alerts – they help you understand what to do, and how to prioritize response, all grounded in the Dragos Platform.
 Whether you’re starting from scratch or refining a mature program, OT Watch helps you accelerate progress with direct interaction from Dragos OT experts. You’ll get guidance tailored to your environment – correcting misconfigurations, uncovering unauthorized devices, and driving improvements based on real-world threat activity. No need to reinvent your strategy, just sharpen it with expert support.
Whether you’re starting from scratch or refining a mature program, OT Watch helps you accelerate progress with direct interaction from Dragos OT experts. You’ll get guidance tailored to your environment – correcting misconfigurations, uncovering unauthorized devices, and driving improvements based on real-world threat activity. No need to reinvent your strategy, just sharpen it with expert support.
 Security teams are stretched thin. OT Watch acts as a force multiplier by offloading monitoring, detection, and investigation tasks, while proactively identifying areas for continued improvement. Close visibility gaps, strengthen daily operations, and stay ahead of threats, all without scaling your team overnight.
Security teams are stretched thin. OT Watch acts as a force multiplier by offloading monitoring, detection, and investigation tasks, while proactively identifying areas for continued improvement. Close visibility gaps, strengthen daily operations, and stay ahead of threats, all without scaling your team overnight.
Benefits of Dragos OT Watch
Contact Us





Adversaries using LOTL techniques don’t always stand out.
Two Options to Fit Your OT Security Needs
OT Watch provides proactive threat hunting, critical threat escalations, response playbooks, and detailed reporting to enhance OT security and informed decision-making.
The OT Watch team uses the Dragos Platform and emerging threat intelligence to execute hunts across customer environments in real-time. OT Watch works with or without a dedicated SOC, integrating with existing teams, processes, or third-party providers to enhance and accelerate your cybersecurity maturity without adding internal burden.
OT Watch Complete includes everything in OT Watch and extends beyond threat hunting to leverage the full use cases of the Dragos Platform by acting as your Dragos Platform operators.
The Dragos OT Watch team, enabled by Dragos Platform technology, provides a level of visibility into our assets and threats that we did not have the expertise nor the bandwidth to do on our own.
See the Dragos Platform in Action
Take the next step to protect your ICS environment now with a free demo