In the first half of 2021, Dragos conducted more industrial cyber incident response (IR) cases than in all of 2020. A common struggle in all these cases was the ability to properly obtain the correct data. Sometimes, the struggle is a disruptive retrieval, such as individual log extraction instead of automated logging. Often though, significant time is spent identifying the data sources that can prove or disprove the investigative hypothesis. These data sources are incomplete or missing entirely because most Operational Technology (OT) and/or Industrial Control System (ICS) asset owners do not invest significant resources into OT/ICS monitoring, detection, and response capabilities. We believe this is the case because the cybersecurity standards they relied upon as the source of truth rely too heavily on prevention.
For the last two decades, industry standards specific to cybersecurity have been focused on prevention: such as protecting the perimeter, applying preventative security countermeasures, and managing internal segmentation. They included aspects of active defense, such as detection, response, and recovery, but without equal emphasis or examples. In this blog, we highlight how this prevention bias inhibits an organization’s ability to effectively respond to a cyber event and how the community can shift to active defense for an overall better cybersecurity posture.
Preventative Vs. Active Response Capabilities
The National Institute of Standards and Technology (NIST) has long established the core functions of a successful cybersecurity program to be: Identify, Protect, Detect, Respond, and Recover in the Cybersecurity Framework. Each function is responsible for an area of cybersecurity that supports an organization’s overall ability to manage cybersecurity risks.
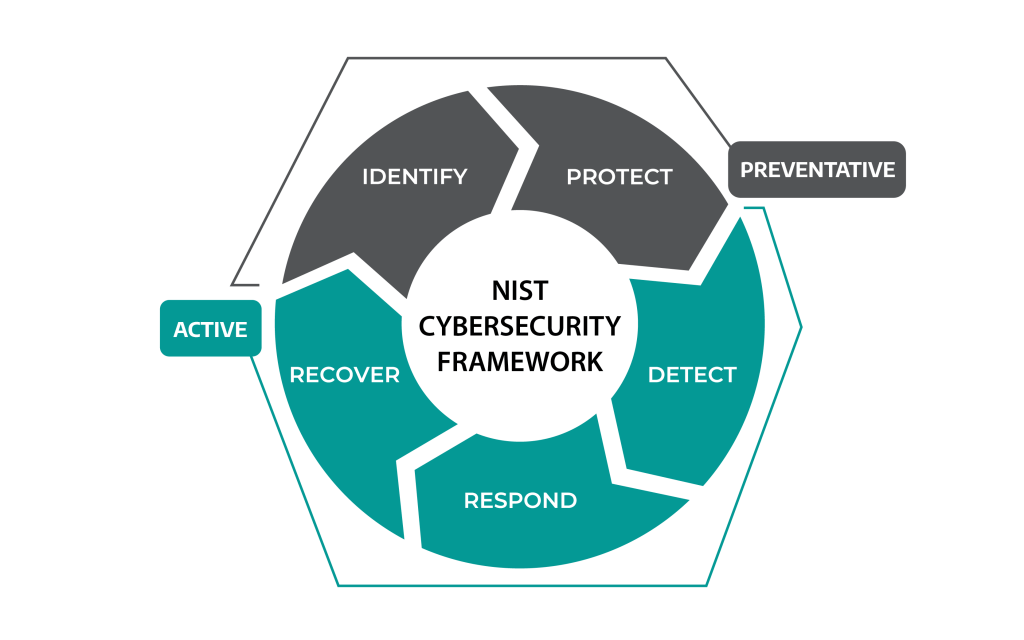
We analyzed dozens of standards and developed a comprehensive mapping of the controls across them as well as the core functions they support. Our mapping identified a disparity, in all the standards, between the number of controls/requirements and how they are distributed between the core functions.
We considered controls/requirements that aligned with the Identify and Protect functions as PREVENTATIVE and those supporting Detect, Respond, and Recover as ACTIVE.
Standards, Regulations, and Best Practices Codify Prevention Bias
Dragos analyzed numerous cybersecurity standards, regulations, and guidelines, including those considered information technology (IT) and OT. Standards were chosen based on whether Dragos observed them being utilized in the following verticals: electric, chemical, manufacturing, pharmaceutical, metals & mining, oil & gas, transportation, water, building automation, and nuclear.
The analysis determined that every standard had a bias to preventative functions, rather than active functions in cybersecurity response. This bias in the standards offers a plausible explanation to the key findings in our 2020 Year in Review that show the OT/ICS industry is not adequately prepared to execute core functions like detection or response.
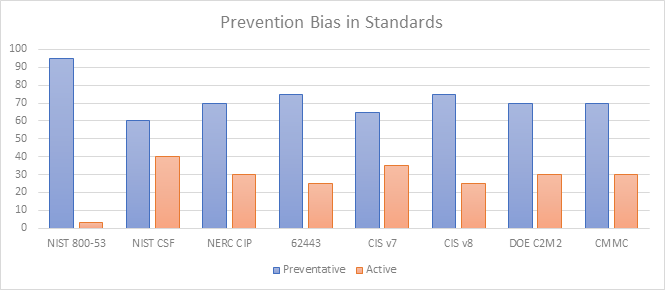
The NIST CSF establishes the five core functions as equally important, so it seems reasonable to expect the controls/requirements to be distributed roughly 20% per core function. However, our analysis shows that within the CSF, the Identify and Protect functions make up 60% of the controls, and the remaining 40% are split between Detect, Respond, and Recover, as seen in Figure 2 above.
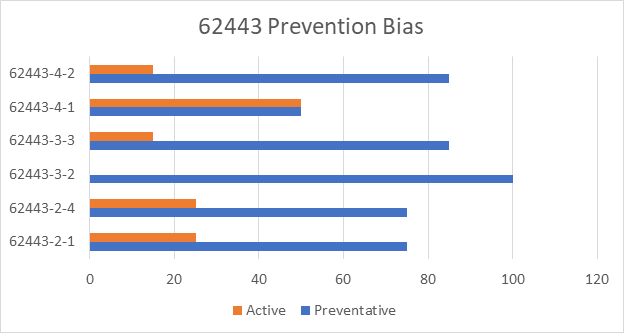
The imbalance is most extreme in NIST 800-53, with 95% of the controls/requirements being preventative (Identify and Protect), 2% active (Detect, Respond, and Recover), and 3% both. While NIST 800-53 itself, is not an OT/ICS standard, it is the basis for some OT/ICS standards and regulations, including NIST 800-82 and NEI 08-09. The OT/ICS standards within the ISA/IEC 62443 series also have this imbalance. The series, as a whole, is 75% focused on prevention, leaving only 25% for detection, response, and recovery. Figure 2 shows our analysis of the individual standards within the ISA/IEC 62443 series.
Preventative Countermeasures Are Not 100% Effective
A harsh truth is that prevention is ideal, but not guaranteed. Preventative countermeasures atrophy over time.
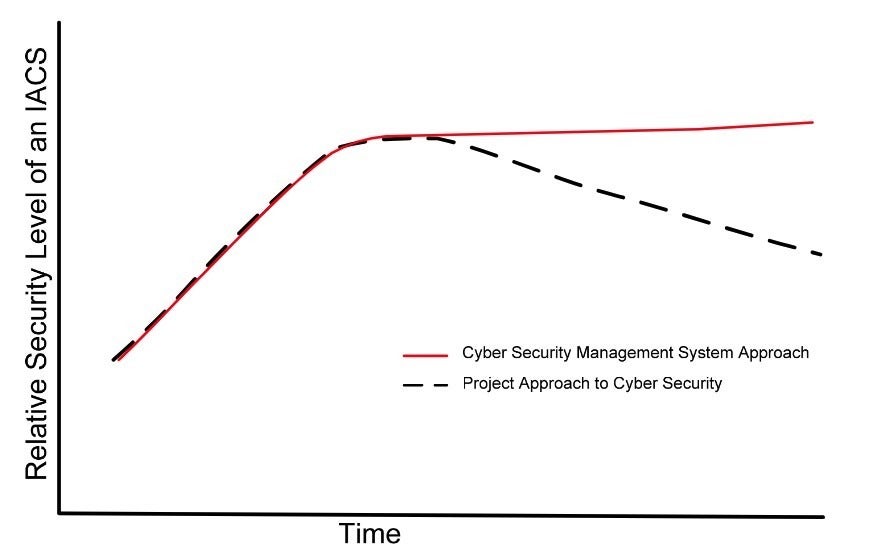
Figure 4, shown below, is from ISA 62443-1-1. The figure shows the relative security level of an Industrial Automation and Control System (IACS) over time. It was created to refute the fallacy that cybersecurity has a start and end date, and to show that countermeasures become significantly less effective over time due to the discovery of new vulnerabilities and/or the development of new adversarial tactics, techniques, and procedures (TTPs). The dashed line represents the effectiveness of security controls when implemented without some mechanism of continuous evaluation. Conversely, the solid red line represents security controls that are periodically evaluated to ensure they remain effective.
Early Detection Leads to Quicker Recoveries and Minimizes Financial Impacts
In many of our rapid response cases, we found that the asset owner had limited or no detection capabilities in the OT network segments. The asset owners were unaware of the failure of their preventative controls until there was an operational impact. Prevention is important, but it is detection that ultimately helps identify security incidents.
In most of our past assessments, we identified a misconfiguration in the network segmentation or a bypass of the flow enforcement mechanism. For example, in a recent architecture review of an oil and gas facility, Dragos discovered a ‘Permit Any Any’ firewall rule that completely negated the segmentation efforts the asset owner had implemented. The rule itself was meant to be temporary and included the word ‘temp’ in its name, but there was evidence that it had been in place for some time. While the protection provided by the firewall may have been effective when it was first installed, over time rules like this crept in and severely diminished the firewall’s effectiveness.
Prevention is only one piece of the cybersecurity puzzle. Other pieces, like detection capabilities, can act as constant validation that other countermeasures are functioning as expected and provide an early warning system when they are not. Nevertheless, all countermeasures, preventative and active, must undergo periodic effectiveness evaluations to remain worthwhile. Unfortunately, no industry organization is exempt from cybersecurity threats, and no industry organization deserves or chooses to become a target. However, having established and well-thought plans of action that can be executed immediately following the detection of a cybersecurity incident is crucial in limiting an incident’s impact to operations and the cost to your organization.
Recommendations for Restoring Balance in Your Cybersecurity Approach
The need for active and resilient OT cybersecurity programs is greater than ever with the continued rise of ICS/OT threat groups, ICS/OT cyber incidents, and the surge of ransomware. Industrial organizations created their cybersecurity programs with a prevention bias when they implemented any one of the standards shown in Figure 2. This bias led to the underdevelopment of their cyber-attack detection, response, and recovery capabilities as documented in our last four Year in Review reports.
Dragos has some recommendations to help OT asset owners overcome the prevention bias and move past this understandable, yet undesirable, situation:
#1: Have a continuous improvement mindset.
Cybersecurity is not something that can be completed. It is an iterative process that must be constantly nurtured. We should think of each core capability not as just another layer of defense, but as force multipliers that strengthen each other. To PROTECT our assets, we must IDENTIFY them. When, not if, our protections fail, we must DETECT those failures, RESPOND to the consequences, and RECOVER normal operations. As organizations examine each core capability within their cybersecurity program, planners should outline approaches and improvements that would enhance security posture beyond the limitations of standards. By iteratively reviewing existing cybersecurity-related documents, opportunities to clarify expectations and procedural changes among stakeholders will also be presented.
#2: Increase visibility into OT/ICS assets.
While many aspects of visibility would fall into the IDENTIFY category, visibility enables detection and is the most critical step on the path to cyber readiness and managing cyber risk. Knowing the real state of assets within your environment and how they are operating on the network establishes a baseline of what ‘normal’ looks like. This visibility of your network provides a sight-picture for how processes and workflows are really executed. Understanding ‘normal’ for your OT environment provides valuable context and contributes higher fidelity information used to accelerate situational awareness and change detection.
#3: OT asset owners should actively test their OT/ICS IR capabilities by regularly conducting Tabletop Exercises (TTX).
Detection is only useful if it enables response action. Rehearsing IR plans during routine exercises is ideal for uncovering procedural gaps and issues with roles, responsibilities, accountabilities, and authorities necessary for the plan to be effective. Crafting realistic OT scenarios is crucial for identifying insufficient data sources or poor data quality needed by defenders during an incident needed to make critical IR decisions. These decisions are unnecessarily complex if there is confusion on where the data lives, how it is accessed, how long that data is retained, and its usefulness.

Ready to put your insights into action?
Take the next steps and contact our team today.
