Welcome to the first in a series of short blog posts on Asset Visibility we’ve put together for the industrial asset owner and operator community, we hope you find it informative and thought-provoking. Some of you will be familiar with these concepts, but for those who are new to industrial cybersecurity or want to supplement their knowledge, this blog series will provide a perspective that will help equip you to better confront the challenges you already face in protecting and defending your environments. In some places, we’ll include visual elements to illustrate key points or demonstrate how the Dragos Platform provides capabilities around asset inventory, asset visibility, threat detection, and more.
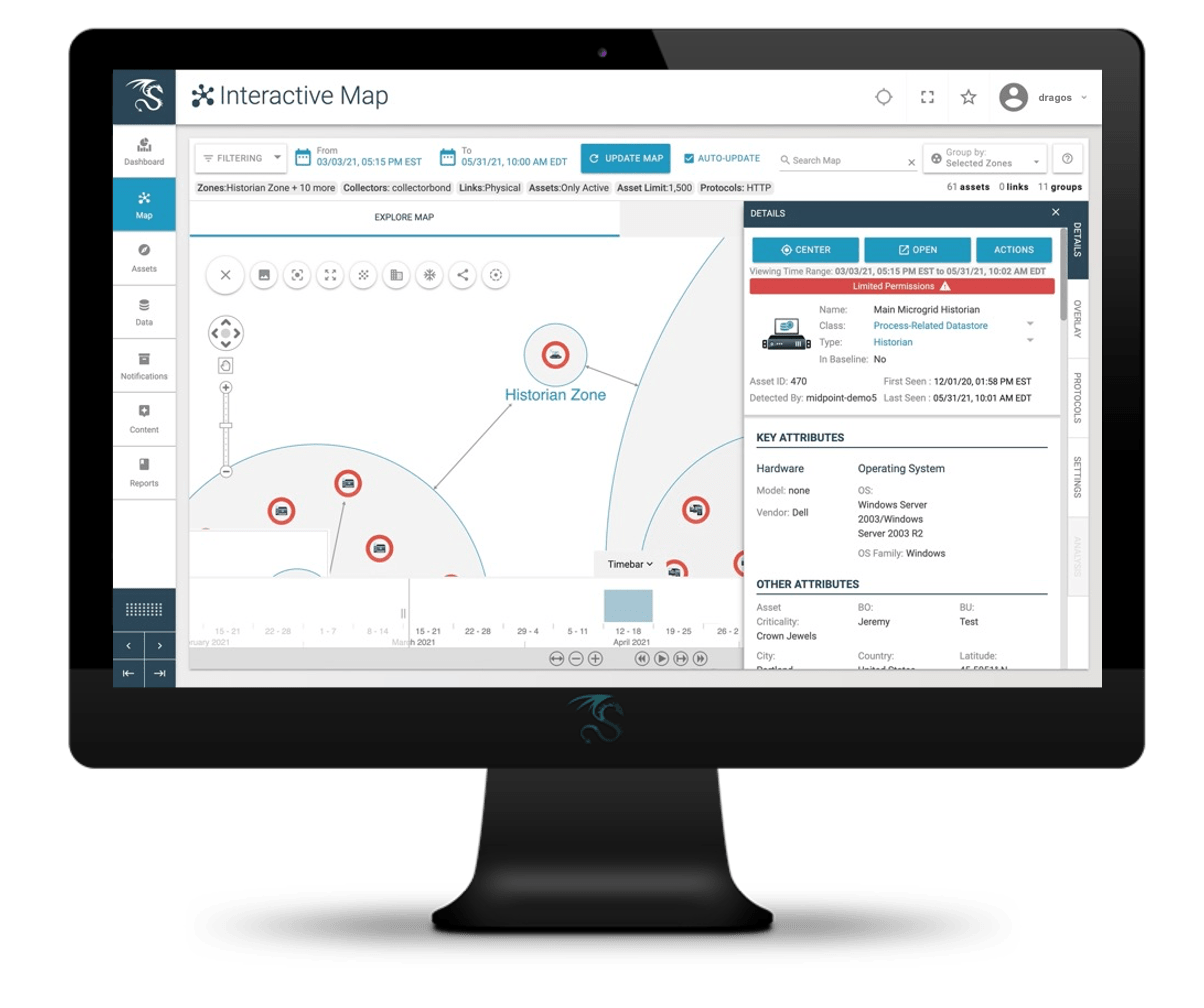
Knowing the real state of your environment – which assets are where and how they’re operating on the network – establishes a baseline of what “normal” looks like. You wouldn’t expect to see a historian pop up on L1, nor would you want to see a patch management server suddenly start beaconing out to an Internet location. This provides a reality check for how processes and workflows really execute in the operational environment. It also adds valuable context and higher fidelity information to accelerate a range of security activities from monitoring and threat detection to change management or incident response.
Establishing this baseline isn’t necessarily an exercise in chasing the brass ring of anomaly detection. Relying singularly on anomaly detection can introduce a host of problems and alert fatigue, as anomalies are not always synonymous with threats. However, tracking the norm and noting deviations from it can provide another dimension of data and a historical record for security analysts to lean on during investigations and remediation.
When [operators] are that busy, there are things, especially documentation, that go by the wayside, and having the asset verification where we can see things coming and going as they’re being added to the network has been very useful for them and for us.”
Cybersecurity Architect, US-based utility company
Operators require tools that make their jobs more efficient, and the easier it is to establish baselines, the quicker they can spot deviations. This can take the form of alerts or notifications, but also in more graphical formats where colors represent operational health. For example, at shift start having the ability to view a simple dashboard that highlights any problematic PLCs in red while displaying stable operator consoles in green, makes it easier to focus on areas requiring attention. The aggressive trend towards connected digital operations is accelerating the need to have centralized views across OT environments.
For the next post in this series, we’ll discuss asset verification, and the role it plays in the larger Asset Visibility context. At any time, you can download a copy of the entire whitepaper “10 Ways Asset Visibility Builds the Foundation for OT Cybersecurity”, or check out the related infographic.
Ready to put your insights into action?
Take the next steps and contact our team today.