ARE YOU READY?!
Last month, MITRE Engenuity announced the initial participants for the inaugural ATT&CK Evaluations for ICS. Industrial Control System (ICS) cybersecurity technology vendors will test threat behavior detection against an emulation of the XENOTIME activity group across MITRE ICS-ATT&CK in an independent test by MITRE Engenuity.
For those not yet familiar with it, MITRE’s ICS-ATT&CK is an ICS cybersecurity knowledgebase classifying malicious cyber threat behaviors across 11 tactics and 96 techniques in networks supporting industrial processes. It can be used to better characterize and describe adversary behavior in networks that have been compromised so that defenders and incident responders can more effectively do their jobs.
“Dragos has entered the chat”

Dragos is excited to participate and showcase the capabilities of the Dragos Platform. The Dragos Platform provides comprehensive visibility of ICS/OT assets and the threats organizations face, with best-practice guidance to respond before a significant compromise.
MITRE’s evaluations will provide the ICS community with insight into adversary capabilities, the importance of understanding adversary behaviors and methodologies, and the value of ICS-specific threat detection and response platforms designed to identify and prevent cyberattacks within operations environments.
As ICS-targeting adversaries become increasingly sophisticated and adopt behaviors specific to ICS environments, defenders must be armed with tools and resources for identifying and combating this activity. Environmental context, which will be a focal point of the MITRE ATT&CK evaluation, is key to detecting adversaries operating within the operations network. For example, the difference between lateral movement in a Demilitarized Zone (DMZ) or lateral movement from an engineering workstation to a safety instrumented system can make all the difference in detection and response.
XENOTIME is an ideal adversary for MITRE to use for this evaluation. XENOTIME was responsible for the TRISIS malware that targeted safety equipment and disrupted operations at an oil and gas facility in Saudi Arabia in 2017. It is one of two activity groups Dragos currently tracks that have the ability to create and deploy ICS-specific malware within operations environments. Dragos considers this activity group to be the most dangerous and capable group currently tracked by the Dragos Intelligence Team.
MITRE’s evaluators will emulate XENOTIME behaviors across an entire real-world attack chain, including the adversary’s initial access, an engineering workstation, and the loss of safety caused by the TRISIS malware.
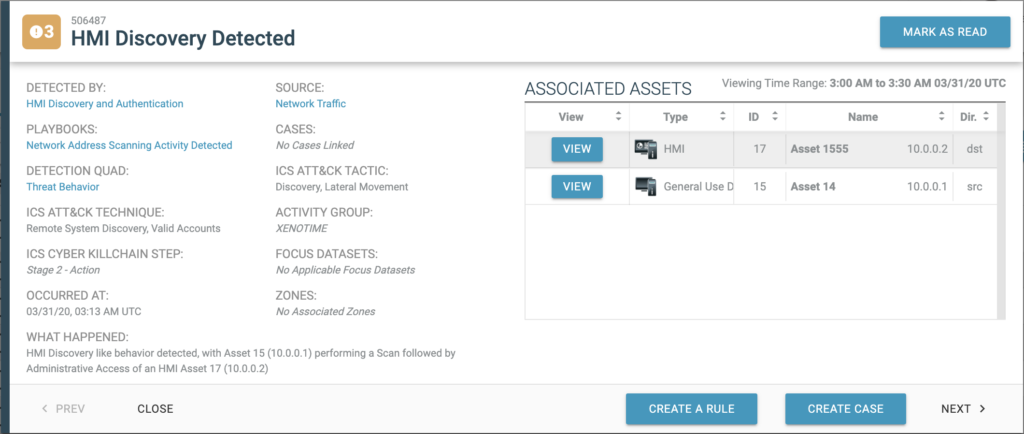
Dragos has pioneered ICS-focused threat behavior detection as part of the Dragos Platform. Adversary hunters on the Dragos Threat Intelligence team identify and track adversary tactics, techniques, and procedures and create analytics and automated detection processes (as shown above in the screenshot) based on the intelligence gathered. These threat behavior detections incorporated into the Dragos Platform codify malicious adversary tradecraft, like various techniques and methodology, regardless of specific indicators such as command and control infrastructure or malware type.
MITRE’s ICS security evaluation underscores the importance of leveraging threat intelligence and threat behavior analytics as part of a comprehensive threat detection and response platform. The emulated XENOTIME attack scenario will use a sophisticated adversary to allow asset owners and operators to see the value of using intelligence-backed security solutions in threat detection, security decision making, and defensive cyber operations.

Ready to put your insights into action?
Take the next steps and contact our team today.