The annual Dragos Industrial Security Conference (DISC) happens every year on November 5. At this conference, Dragos shares some of our team’s best research across a full day of ICS-focused cybersecurity sessions. For the first time this year, we offered a DISC Capture the Flag (CTF) that spanned two days prior to the event, from 12 pm ET on November 2 through 12 pm ET on November 4.
We certainly have experience creating CTF challenges for numerous other events, which have been both fun to build and well received by participants around the world. So, we asked ourselves, why wouldn’t we develop our own CTF for DISC?
What is Capture the Flag (CTF)?
A Capture the Flag event is a great way for cybersecurity practitioners to learn, practice, and develop new skills and knowledge in tackling specific security challenges they may encounter on the job. These skills and knowledge not only apply to red-teamers acting as adversaries in simulated events to test detection and response capabilities but blue-teamers playing as the defenders protecting critical assets.
The CTF security challenges are often designed to make participants think outside the box to help develop a deeper understanding of accessible/non-accessible ports, network protocols, and network communications and often leverage user or system misconfigurations.
How We Built the DISC CTF
For the DISC CTF, we developed challenges that expose participants to industrial control systems (ICS) security situations that often are not found in traditional CTF events.
The challenges we developed ranged from programmable logic controller (PLC) issues in the form of Docker containers, to analyzing industrial protocol-based network packet captures, to discovering flags hidden within memory dumps gathered from engineering workstations in our own Dragos brewery range located at our Maryland headquarters. The activities were taken from our threat hunting playbooks and influenced by Dragos professional services’ engagements.
Each challenge was created to provide a unique learning experience with the hope that CTF participants gained a new skill or took lessons learned back to their organizations.
Several items we considered in creating each challenge included but was not limited to:
- Ensure that participants of any experience level are able to participate, have fun, and learn something new – whether they are currently working in the ICS space or not.
- Cover a wide spread of operating systems due to the variety often seen in ICS environments – such as Windows 7, Windows 10, etc.
- Educate security blue teams on the common environmental misconfigurations that cyber threat groups could leverage to further a foothold in an attack chain.
To make the PLC challenges available to DISC CTF participants in a safe and scalable manner, we created them to use OpenPLC. OpenPLC is a soft PLC that runs PLC programs without the typical hardware requirements.
OpenPLC includes a web management interface, a Modbus server, and a PLC program unique to the challenge being solved. These items were delivered in the form of Docker, which is an open platform for developing, shipping, and running applications. Participants were able to download the Docker images and run them in their own environment, ensuring the safety of their systems.
How We Supported DISC CTF Participants
As part of the DISC CTF, we needed to identify a method to easily provide support to participants, if requested. CTFs are a great learning opportunity and we want to do whatever we can to help encourage participation in these activities – no matter the experience level or understanding of the ICS space.
To support participants during the event we used Discord, a VoIP instant messaging platform. The Discord server created for the event was shared with all the participants as a way to ask for support or hints along their journey in solving the CTF challenges.
So as not to reveal solutions or hints to other participants that did not request them, Dragos used direct messaging to communicate with the individual teams.
DISC 2021 CTF by the Numbers
For our inaugural DISC 2021 CTF, we had close to 300 players register for the event, representing 191 teams located in 28 different countries around the world.
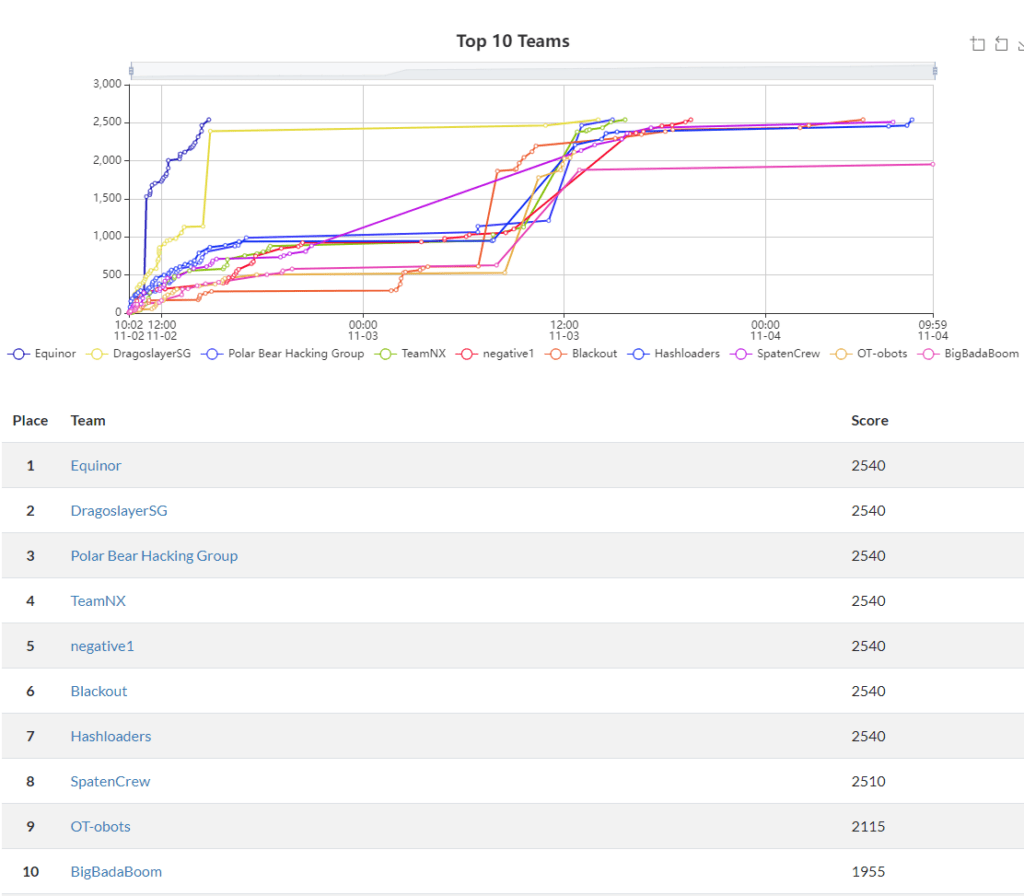
- A total of 7 teams successfully completed all the challenges earning their spots on the Top 10 Teams leaderboard. The total number of points achievable after solving all the challenges was 2540.
- We received 106 support requests via the Discord support server during the CTF event.
- The challenge that had the least number of solves was in the Binary Analysis category.
- The challenges that had the highest number of solves were in the PCAP Analysis category, with the Phishing category close behind it.
Want to Play in the Next DISC CTF?
We hope that all participants gained valuable insights and knowledge playing in the DISC 2021 CTF event and look forward to challenging your industrial cybersecurity skills again next year. Sign up now for DISC 2022 to be the first to know about the next Dragos CTF and other ways to grow your ability to safeguard your operational technology environment.

Ready to put your insights into action?
Take the next steps and contact our team today.

