Build ICS/OT Skills in IT Cybersecurity Teams
Put ICS/OT threats in context—detect, triage, and respond to events leveraging the processes already in place for your IT threats.
Develop ICS/OT Cyber Skills to Protect Operations
OT and information technology (IT) may share similar technologies running on similar operating systems, network connections, and digital architectures, but industrial working environments are very different than IT. Industrial infrastructure operates specialized machinery with longer lifecycles than IT equipment, and are heavily engineered to fulfill the core functions of the business – producing electricity, manufacturing products, transporting products. The key focus is on continuous operations.
Business continuity requirements are orders of magnitude more stringent, plus the additional elements of physical safety considerations and regulatory obligations. Driving effective convergence of OT/IT by integrating OT-smarts into IT security infrastructure and processes requires extremely deep domain expertise from operators who oversee those processes.
 Most vulnerability disclosures are written with IT in mind and don’t properly characterize the risks to ICS/OT environments. Recommendations to patch are common, which is impractical in continuously running operations. Vulnerability management requires alternatives to patching and accurate risk information to be effectives in industrial environments.
Most vulnerability disclosures are written with IT in mind and don’t properly characterize the risks to ICS/OT environments. Recommendations to patch are common, which is impractical in continuously running operations. Vulnerability management requires alternatives to patching and accurate risk information to be effectives in industrial environments.
 Isolating a laptop, cutting a connection to a server – those are common first responses to an IT incident. But shutting down industrial operations too quickly is unsafe, and doing so at all has downstream consequences on the people who rely on them. The toolkit for responding to ICS/OT incidents must include a specialized plan, tools, and expertise.
Isolating a laptop, cutting a connection to a server – those are common first responses to an IT incident. But shutting down industrial operations too quickly is unsafe, and doing so at all has downstream consequences on the people who rely on them. The toolkit for responding to ICS/OT incidents must include a specialized plan, tools, and expertise.
ICS/OT Incident Response
 ICS/OT environments once operated in isolation with inherent trust between devices. Today, network communications are specialized to the equipment and operate at the edge of capacity. Malformed queries, excess traffic, or bad command syntax cause systems to freeze or shut down. IT solutions won’t speak the right language or meet the availability requirements of high-stakes ICS/OT environments.
ICS/OT environments once operated in isolation with inherent trust between devices. Today, network communications are specialized to the equipment and operate at the edge of capacity. Malformed queries, excess traffic, or bad command syntax cause systems to freeze or shut down. IT solutions won’t speak the right language or meet the availability requirements of high-stakes ICS/OT environments.
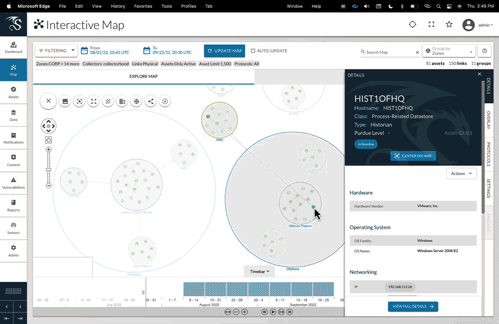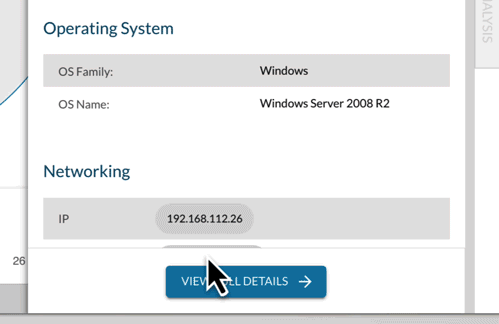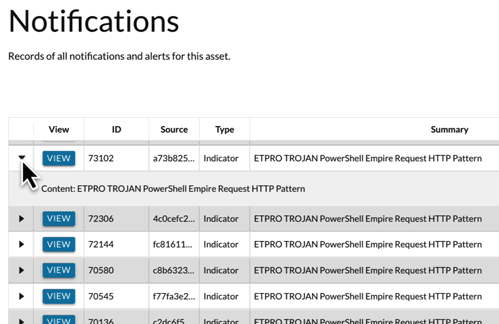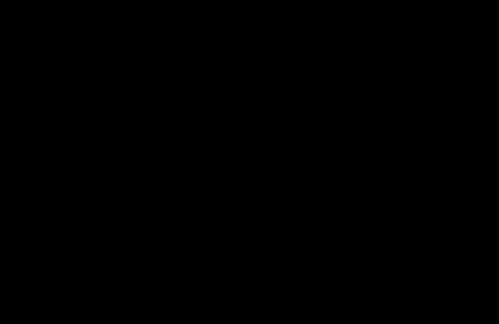
Asset Visibility
 Techniques used to compromise IT networks won’t necessarily work in ICS/OT networks. Adversaries targeting electric grids, oil and gas pipelines, and manufacturing plants behave much differently and demonstrate sophisticated capabilities, like the PIPEDREAM malware attack framework. Knowing what adversaries to watch out for and how they behave in ICS/OT environments is the secret to spotting and stopping threats before they have an impact.
Techniques used to compromise IT networks won’t necessarily work in ICS/OT networks. Adversaries targeting electric grids, oil and gas pipelines, and manufacturing plants behave much differently and demonstrate sophisticated capabilities, like the PIPEDREAM malware attack framework. Knowing what adversaries to watch out for and how they behave in ICS/OT environments is the secret to spotting and stopping threats before they have an impact.
Threat Groups
 Dragos is represented by the largest and most experienced team of ICS/OT security practitioners – that includes threat hunters, researchers, and incident responders – to deliver the Dragos Platform, build OT security programs, and gather the intelligence on ICS/OT-specific threat groups, TTPs, and vulnerabilities.
Dragos is represented by the largest and most experienced team of ICS/OT security practitioners – that includes threat hunters, researchers, and incident responders – to deliver the Dragos Platform, build OT security programs, and gather the intelligence on ICS/OT-specific threat groups, TTPs, and vulnerabilities.
The Dragos Platform provides visibility of ICS/OT threats across your entire security organization.
- Asset discovery, inventory, and profiles to understand and track the ICS/OT attack surface
- The most effective behavior-based threat detection to identify real threats as validated by MITRE ATT&CK for ICS
- Risk-weighted vulnerability scoring with prioritization and risk mitigation practical for ICS/OT systems
- Expert response playbooks tailored to threat scenarios for rapid event investigation
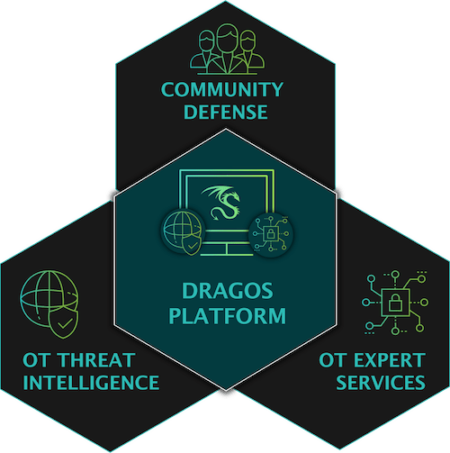
Industrial cybersecurity experts to help with incident response, evaluate architecture, and advance your OT security program.
- Expert responders to refine incident response plans, test those plans, and respond on those worst days when you need expert assistance to investigate and resolve incidents
- Cyber industrial consultants to perform penetration tests, assess architecture and vulnerabilities, and to baseline and help you create a plan to mature your program
Dragos WorldView Threat Intelligence delivers situational awareness into adversary activity and vulnerabilities that impact industrial sectors.
- Adversary research details the capabilities used to execute attacks in ICS/OT environments
,and strategic intelligence reports cover regional and industry sector risks - Indicators of compromise (IOC) feeds to enhance SOC operations and investigations
- Lab-tested malware and vulnerability analysis provides insight into the OT impact and guidance on how to mitigate and respond
Five Critical Controls for ICS/OT Cybersecurity
Your ICS/OT Cybersecurity Requirements
It doesn’t make sense to copy and paste enterprise cybersecurity strategies that don’t account for what’s important to ICS/OT asset owners and defenders.
The SANS Institute has developed five critical controls for ICS/OT cybersecurity to cover the basic requirements for all industrial organizations to use for alignment across IT and ICS/OT security teams.

Driving Convergence of OT with IT Security Infrastructure
OT-specific expertise can help drive convergence of systems and processes that streamlines operation and security. From SIEMs to firewalls and endpoint technology, integration of the two worlds is key to driving effective protection and operational efficiency.

Threat Intelligence Platform (TIP)
WorldView reports data on industrial adversaries, campaigns, IOCs & TTPs available via portal, email, API, & STIX.

Endpoint Security
Dragos OT device profiles, Dragos OT detections integrate into EDR to block malicious activity

Service Management
Integrates Dragos asset inventory & vulnerabilities to gain complete asset view across IT/OT estate.

SIEM/SOAR
Dragos integrates OT alerts, forensic data, & IOCs to simplify SOC triage & streamline investigations.

Firewall
Dragos OT device inventory for firewall policy, Dragos threat detection notifies firewall to isolate devices. Monitoring helps validate firewall policies.

TAP/Packet Broker/Traffic Aggregator
Send data to Dragos to simplify deployment & hardware requirements. EDR information enhances
Lessons Learned from the Front Lines

Ready to Advance Your Cybersecurity Compliance?
Wherever you are in your cybersecurity journey we’re here to help you take the next step in auditing and adhering to industry compliance requirements.