This is our monthly blog detailing best practices for operational technology (OT) cybersecurity for under-resourced organizations by Dragos OT-CERT (Operational Technology – Cyber Emergency Readiness Team), which provides free resources to help small and medium businesses (SMBs) create or enhance their OT cybersecurity program. The Category and Practice from the “OT-CERT OT Cybersecurity Fundamentals Self-Assessment Survey” is noted for each best practice. Hopefully, you filled out the survey and identified your gaps – these best practices can be implemented to begin to address those gaps. If not, there’s no time like the present – join OT-CERT and get started today.
Larger Organizations Take Note
If you have been increasing your security posture and reduced risk of a significant cyber attack in your enterprise, including your OT environment, that’s excellent news! However, does your risk assessment include the possibility of a cyber attack on one of your critical suppliers, and the impact that would have on your company’s operations? Could you still produce your product or provide services to your customers? Read on to ensure that you are quantifying the likelihood and impact of that risk correctly in light of the current threat environment. And strengthen your supply chain security risk posture by promoting OT-CERT to your suppliers.
Legal Disclaimer
OT-CERT resources are intended to provide guidance to help under-resourced organizations, those lacking sufficient financial resources or technical expertise, to establish minimum baseline OT cybersecurity protections and do not necessarily meet the usual best practice standards for a mature OT cybersecurity program. Dragos, Inc. does not provide any warranty or guarantee that following the guidance provided by OT-CERT alone will safeguard an organization from all OT cybersecurity threats. Whenever possible organizations should seek additional enhancements to the recommendations provided by OT-CERT resources based on an organization’s own cybersecurity risk profile.
Best Practices for Transferring Files to an OT Environment
During assessments, Dragos consultants spend a good deal of time discussing with customers how files are transferred between different levels of trust (corporate zones, DMZ zones, OT zones). Often, we hear that there is no company-approved policy for file transfers, but it’s common practice to use USB drives to move files. However, many customers fail to consider the history of the drive, such as who owns it and the data on it, when the last time it was scanned for viruses, or if the owner of the drive uses it for personal information as well.
USBs present many risks, including risk of information loss / exposure, but a significant concern in the OT environment is potential that it contains malware that could disrupt operations. This risk is especially high in a smaller organization that cannot afford USB inventorying software or an antivirus (A/V) scanning kiosk. Stuxnet is the prime example of why companies need a written and enforced data transfer policy.
In this month’s blog, we discuss a common method of transferring files that is simple, effective, and provides several defense-in-depth advantages that aren’t afforded by transferring files via USB. As always, OT-CERT recommends that you apply cybersecurity controls using a risk-based approach, where possible, and of course as necessary to follow regulatory requirements, organizational polices, and/or insurance requirements.
| Categories | Best Practice |
| Configuration Security Cyber Risk Management Cybersecurity Incident Response | NOTE: The following configuration is the ideal configuration. Some of the protections listed below might be modified to fit budgetary or workload requirements based on your organization’s risk. For this configuration, you should have at least three file transfer servers: one for corporate/IT/enterprise/business, one for the demilitarized zone (DMZ), and one for the OT zone(s). These servers need to be patched, easy to administer, and run an anti-malware tool. Ideally, an organization would also have 2 firewalls, between corporate and the DMZ and between the DMZ and OT, as well as an IDP/IPS (Intrusion Detection System / Intrusion Prevention System) for traffic between zones. Finally, logging and monitoring solutions are needed on various devices throughout the process. Why three servers? We don’t want a low-trust zone communicating directly to a high-trust zone. OT-CERT highly recommends that this requirement not be reduced to two or less servers. To save on licensing, you could consider a Linux operating system. Can we use servers that are already being used for other purposes? In an ideal situation, and mandated in some cases, each function should have a dedicated server per trust zone, i.e. a dedicated WSUS server, an antivirus server, a file transfer server in each of the IT, DMZ, and OT trust zones. Dedicated assets per function helps enable defenders to reduce the attack surface for each asset and can simplify incident response actions. However, we understand the cost, complexity, and additional maintenance that comes with additional assets may not be practical for some organizations. As always, OT-CERT recommends that while you are sure to meet any regulatory or organizational requirements, you should also take a risk-based approach to applying cybersecurity controls. A single server in each network trust zone that is cybersecurity hardened, monitored, and defended can serve multiple roles for some organizations, if their risk profile and other requirements allow it. It is important to note however, that OT-CERT recommends that a single asset or server is never configured in a way to bridge different trust zones. If you have a server that serves multiple roles, you should always have one in the DMZ and one in ICS/OT environment and never dual home an asset across those zones. Why an anti-malware tool? If you are transferring a file into a higher trust zone, you need to ensure that the files moving through are not malicious. Since these files are being transferred and not yet being used to keep operations running, heuristics can be utilized to scan the files. OT-CERT recommends two solutions, one could be the default Windows Defender that comes standard on Windows operating systems. Using both A/V and EDR solutions limits evasion by providing different detection mechanisms, and a backup capability in case one of the solutions goes offline for any reason. OT-CERT cautions that an EDR solution would require an always-on connection to the Internet, which will leave the environment vulnerable. For this reason, it is recommended that only the corporate and DMZ servers utilize an EDR solution. NOTE: Extreme caution is recommended when enabling heuristics on ICS/OT assets that are used for the monitoring and/or control of the industrial process in a production environment due to the possibility of the EDR blocking a vital file. Why IDS/IPS? Like A/V or EDR, the more protection you can provide, the better. This is not a necessary component. Why a monitoring solution? It might be possible for an adversary to disable monitoring on one device or two without being detected, but it would be hard to disable monitoring on seven or more assets without someone noticing. There would be eight different assets that could identify malicious software. If configured correctly, all devices would indicate successful or attempted connections on the secure channel. And finally, either the servers or domain controllers would log authentication attempts. What assets to monitor: All three servers –Local user login success/failure –Anti-malware alerts –Operating system default logs All firewalls –Local user login success/failure –Excessive firewall denies –Modification of firewall rules –Default logs from asset Anti-malware solution –Malware alerts –Failed client agents –Malware definitions out of date on clients –Local user login success/failure –Operating system default logs IDS/IPS solutions –Local user login success/failure –Malware alerts –Malware definitions out of date –Default logs from asset Domain controllers –Domain user login success/failure –Off hours user login success/failure –Anti-malware alerts –Operating system default logs Note: Additional logging information can be found in the OT-CERT Host-based logging resource Why authentication and access control? All the security features discussed to this point are technical, but one of the biggest security risks to a network is the user. It’s impossible to protect against all users, but we can make it difficult for users to do something accidently that negatively impacts operations. In addition, if a user’s corporate account is compromised the adversary will not be able to use it on the OT network. In the configuration described above, a user will have to authenticate into three different domains or Linux assets, which means three different passwords, three different login policies, and three different file/folder access restrictions. In addition, utilizing a domain, Group Policies and Active Directory provides outstanding granular security features such as login hours, computer-based firewall rules, and centralized administration. When a user pushes or pulls a file, they will log into one machine to start the process with the domain user on that machine’s domain. When logging into a machine in another domain to transfer the file, the user will utilize their user account from the second domain. Machines in the DMZ and OT environment should only be accessible for RDP access for pulling/pushing files by VPN connection into that environment with Multi-Factor Authentication (MFA). This configuration adds another layer of security due to the authentication required for VPN access. What are the most important key features in this configuration? — An authorized user is in charge throughout the whole process. — An authorized user is initiating the transfer. — An authorized user is using their specific authentication across three domains. — An authorized user is aware of what files are being transferred. Pushing to Corporate: The most important aspect of transferring files between any environment is that one is always controlling the file as it moves between the environments. In this configuration – shown in the figure below – the zone of higher trust is initiating all communications. OT to DMZ then DMZ to Corp. At no point is the lower zone initiating the communications. A one-way firewall rule from the higher zone to the lower zone will ensure that a lower zone cannot initiate the transfer. 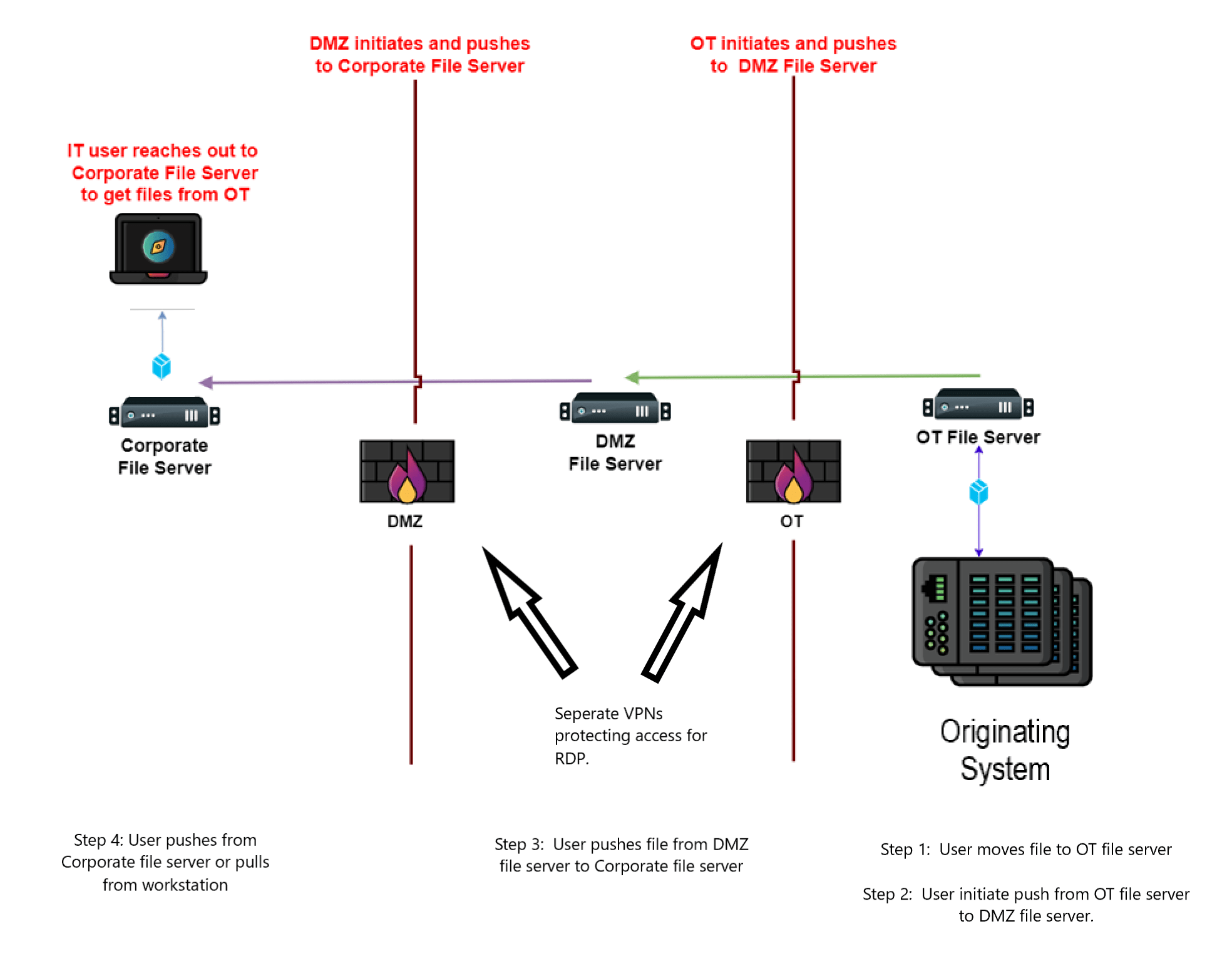 Pulling from Corporate: In this configuration – shown in the figure below – the zone of higher trust is initiating all communications. DMZ pulls from Corp then OT pulls from DMZ. As with pushing to corporate, at no point is the lower zone initiating the communications. A one-way firewall rule from the higher zone to the lower zone will ensure that again a lower zone cannot initiate the transfer. 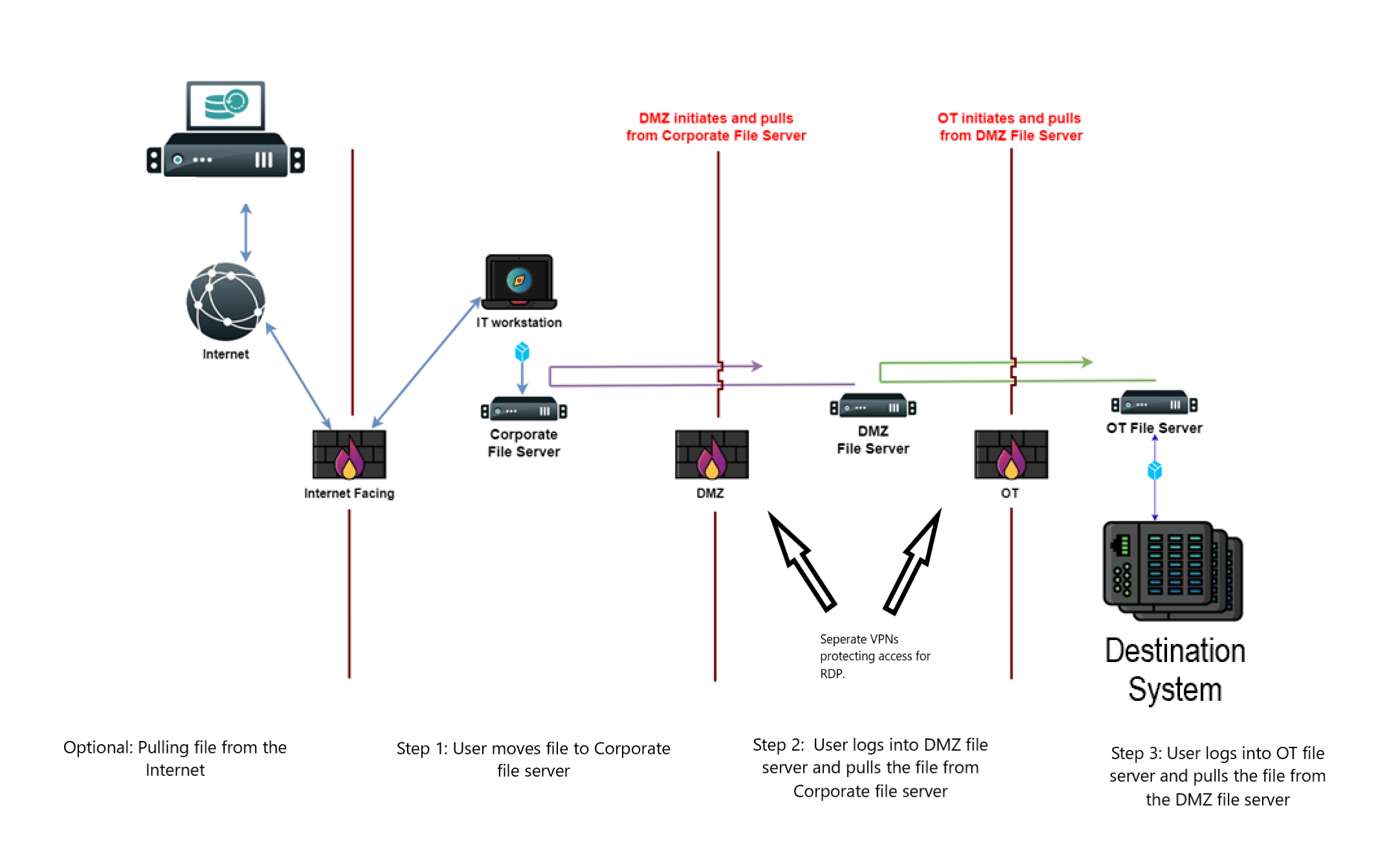 |
Stay Up to Date with SMB Cybersecurity Resources: Join Dragos OT-CERT!
Dragos OT-CERT offers FREE resources to help SMBs build their own manufacturing / OT / industrial control systems (ICS) cybersecurity program without hiring any cybersecurity experts. OT-CERT membership is free and globally available to OT asset owners and operators. Resources are oriented toward small and medium businesses and resource-challenged organizations with OT environments that lack in-house security expertise. Members have access to a growing library of resources such as reports, webinars, training, best practices blogs, assessments, toolkits, tabletop exercises, and more.
Currently available resources include:
- OT Cybersecurity Fundamentals Self-Assessment Survey
- OT Asset Management Toolkit
- Self-Service OT Ransomware Tabletop Exercise Toolkit
- Collection Management Framework for Incident Response
- OT Cybersecurity Incident Response Toolkit
- OT Data Backups Guidance
- Host-Based Logging and Centralized Logging Toolkits
- Secure Remote Access Toolkit
- Access to an introductory ICS/OT cybersecurity module in Dragos Academy
If you haven’t joined Dragos OT-CERT don’t delay! Membership is open to organizations that own or operate a manufacturing / ICS / OT environment. Please join and spread the word to your community and supply chain so we can all work together to raise the security posture of the entire ecosystem – we are only as strong as our weakest link.
We look forward to working with you to safeguard civilization!
Join OT-CERT today!
Ready to put your insights into action?
Take the next steps and contact our team today.
