The phrase, “living off the land,” is among the most prevalent and misunderstood terms used to describe adversary activity. Living off the land describes the use of typically pre-existing, legitimate capabilities present on a victim host and network for malicious purposes. Most cyber professionals associate this phrase with information technology (IT), including Windows workstations and software. The methods of living off the land work on the operational technology (OT) side too, albeit with differing toolsets. These methods include abuse of native functionality and features in control networks, such as operations of human machine interfaces (HMIs) or OT-specific automation control protocols.
Why ICS/OT Cybersecurity Should be Concerned with Living off the Land
- ICS-targeting adversaries use living off the land techniques, especially for conducting ICS disruptive events.
- Traditional IT security protection mechanisms do not work to defend against this activity.
- Insight into this type of activity can enable better, behavior-based threat detection.
Each stage of a living off the land attack uses tools that already exist in the target environment or are common enough not to cause alarm. There are other tactics adversaries can use, but the pattern remains largely the same: gain credentials, pivot around the network, and execute the desired effect.
An adversary may start by emailing a target a link to a credential capture site to steal their login details. Credentials can also be found in a “dump” on the Internet to access the network remotely through brute force activity or password spraying. From there, attackers probe the target’s network and applications for soft spots they can log into or exploit, like email, VPN, or customer facing applications. Once a foothold is established, attackers begin to escalate privileges and pivot throughout the network, looking for privileged accounts such as administrative users. Using PowerShell or tools like SysInternals [1] help attackers reach their ultimate goal while blending into normal administrative traffic. Attackers can transition from the IT environment to the OT environment via stolen credentials or improperly configured networks. Adversaries then must utilize knowledge of ICS environments to conduct reconnaissance to potentially affect operational devices.
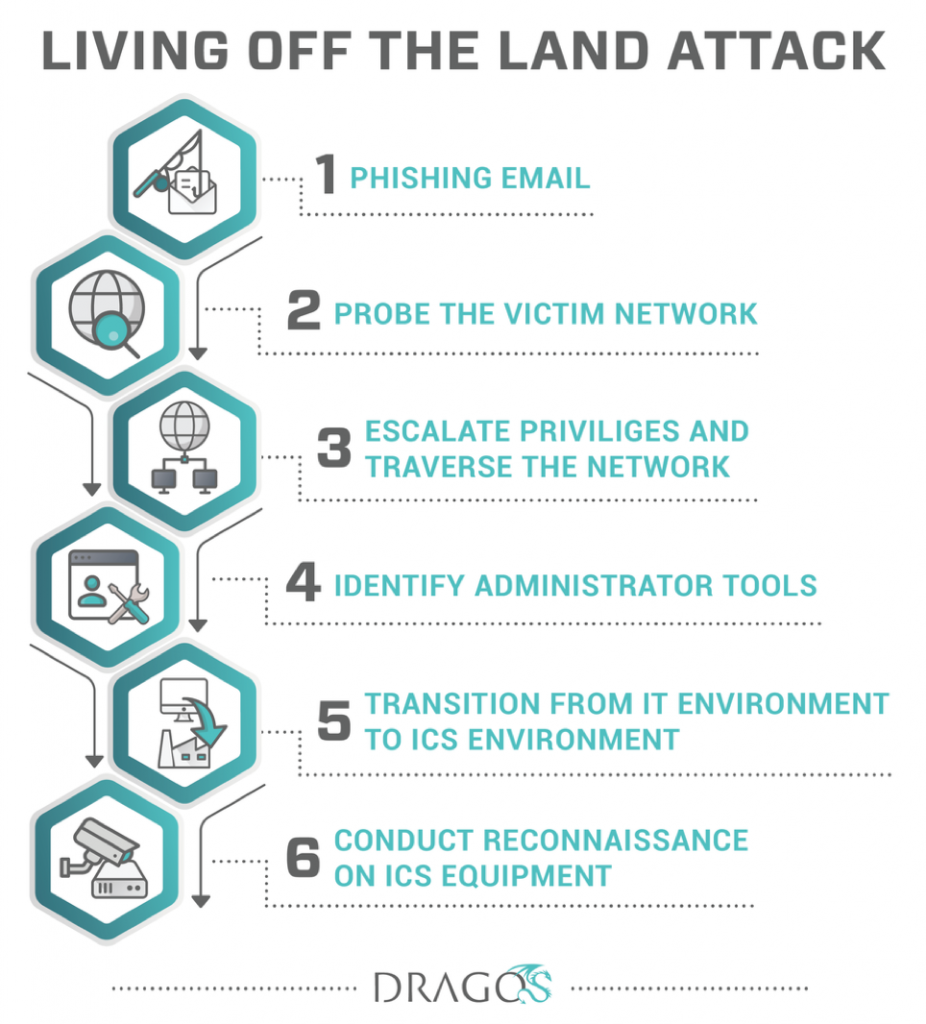
Figure 1: Living of the Land Attack
Dragos tracks multiple activity groups that successfully use living off the land tactics to target OT networks. ELECTRUM [2] pivoted from IT to OT networks via harvested credentials, then exploited functionality in Microsoft’s SQL Server to enable the CRASHOVERRIDE attack on a substation in Ukraine. ELECTRUM leveraged its knowledge of the victim’s environment and specific protocols used in European power generation, transmission and distribution (IEC 101 and 104) to control circuit breakers and switch gear in that attack. [3] The activity groups DYMALLOY [4] and ALLANITE [5] use captured credentials to pivot inside of electric sector OT networks to access and profile systems within the operational environment as part of long-term reconnaissance operations. XENOTIME [6] used PSexec, [7] part of SysInternals, for remote execution and pivoting with privileged credentials that were dumped or captured.
Security teams use multiple techniques to combat living off the land, but there is no one size fits all approach for defense. Some well-known defenses are email filtering, user training, system hardening, firewall tuning, and robust network segmentation. However, those methods will not provide useful information when a breach occurs.
The following methods will assist in either defeating attackers or can act as a canary to alert to an event:
- Monitoring Administrator and Service Accounts: Accounts with administrative privileges (domain admin, local admin, delegated admin) are commonly targeted in living off the land incidents and should be monitored carefully. The LockerGoga [8] ransomware attack that caused significant operational disruptions to the Norsk Hydro aluminum manufacturing company was deployed via the company’s Microsoft Active Directory instance utilizing Group Policy. Organizations should enforce multifactor authentication, limit administrative privileges to only necessary users, and restrict communication between endpoints and groups. This is known as “least privilege” [9] and is a tenant of identity management. Defenders should audit access across IT and OT, including separation of identities and duties between environments. OT environments should not have trusts [10] with IT at the domain or forest level. Segmenting accounts helps neutralize pivoting and living off the land tactics.
- PowerShell: PowerShell is the scripting language upon which modern Microsoft Windows operations are built. It allows for the administration of many functions in the Microsoft platform, which makes for an obvious target. Attackers know it will be on any version of Windows 7 or later. Defenders have multiple options at their disposal to alert on attackers. Companies should upgrade PowerShell to at least Version 5, which has verbose logging enabled that includes command line arguments. PowerShell should also be secured against attacks that downgrade PowerShell to older versions. Multiple tools, such as TrustedSec’s Unicorn, [11] can abuse PowerShell to return a command shell to attackers and enable an adversary to inject shellcode into memory. PowerShell versions can be set via Group Policy in Active Directory, [12] preventing an attacker downgrading to a less secure version. Logging and monitoring PowerShell should be done in the IT and OT networks. [13]
- Honey Credentials: Honey credentials can alert for detecting possible breaches. They allow defenders to place unused credentials on their machines that should never be accessed. If the credentials are used, it should signal someone has dumped the credentials from a machine on the network. There are many “honey” tools used to detect compromise on a system. A short list includes honey credentials, honey tokens, honey hashes, and honey users. These honey identifiers can be placed throughout a network, alerting defenders when the associated hash or password is passed by an attacker. They can also be used proactively against phishing attempts if the honey credentials are submitted into phishing sites to see what follow-on attacks occur. This can be especially useful when coupled with identifying high value targets (HVTs) such as executives, plant engineers and lawyers. There are several toolkits, like the CredDefense Toolkit [14] from Black Hills Information Security, and various write-ups on using these techniques, such as an example on honey hashes, [15] that can be used for further research. Using honey credentials or hashes in the OT environment can be useful for exposing a breach that passed the IT/OT barrier.
- Known Compromised Credentials: Similar to honey credentials, defenders can also use previously compromised account credentials in detection. If an account is compromised in a previous incident, defenders can leave it active and monitor its use to see if an attacker returns to use it. Scouring paste or breach sites[16] are a great way to find corporate credentials that have been leaked accidentally or maliciously.
- Windows Management Instrumentation (WMI): Adversaries, including the ICS-targeting activity groups Dragos tracks such as XENOTIME and CHRYSENE, [17] repeatedly use Windows Management Instrumentation (WMI) to pivot around networks and gather data. However, WMI is rarely logged sufficiently. Aggregating these logs and looking for specific event types can provide a powerful means to detect lateral movement and reconnaissance activity. Matthew Graeber has an informative write-up [18] on abusing and defending against malicious WMI. He provides specific events to look for and tools that can help in incident response.
- Server Message Block (SMB): Adversaries frequently use the Server Message Block (SMB) protocol as means of pivoting. The protocol is mainly used for file sharing within a Windows enterprise network and is abused regularly because of how the protocol transmits a Windows authentication hash when connecting to another device. The Shadow Brokers dump of 2017 leaked multiple tools, including the ETERNAL series, [19] that took advantage of insecurities in SMB Version 1. Attackers behind WannaCry, NotPetya, and BadRabbit ransomware used these exploits following the leak. Dragos has tracked multiple activity groups using SMB for credential harvesting including DYMALLOY, ALLANITE, and RASPITE. [20] Due to the popularity of SMB usage among various adversaries, monitoring SMB is critical to possibly detecting compromise. The paper Detecting Malicious SMB Activity Using Bro by Richie Cyrus describes that since networks contain and rely on legacy systems and equipment more than IT, it is unlikely that SMB can be removed or fully upgraded (currently v3). Defenders will need to “settle” for visibility and blocking at chokepoints. [21]
- ICS Protocols: Attackers can use legitimate ICS protocols maliciously to control field equipment, but there are ways to find suspicious activity. Baselining normal communications within the environment and monitoring for abnormal use of ICS protocols can detect malicious behavior. However, a deviation is not sufficient to know something malicious occurred, only that it should be investigated.
- Monitor for systems that should not normally access OT assets for communication. Detecting a workstation on the network that never previously communicated with a programmable logic controller (PLC) directly and begins to do so could be malicious.
- Identify unusual behavior on systems that normally access ICS assets. This could be something like an HMI executing engineering tasks, or an engineering workstation doing activity normally reserved for HMIs, like issuing commands to a PLC.
- Identify systems that normally access ICS assets in an authenticated manner but are doing so in an unusual way. This may include HMIs that generally read data from a PLC and are now issuing write commands.
- Look for differences in communication between established nodes. A typical interaction may be out of sequence or the steps may be reduced because attackers do not follow the normal protocol states. For example, CRASHOVERRIDE violated IEC-104 protocol states, only performing the commands required. [22] This is apparent if there are custom snort rules in place.
- Threat Behaviors: As ICS-targeting attackers increasingly move to living off the land techniques, utilizing threat behavior detection can identify adversaries within a network even if the behavior seems legitimate.[23] This method also allows defenders to focus on behavior patterns matching a known-malicious series of events and activity irrespective of the technical elements and indicators (often these are codified into “threat behavior analytics,” a threat detection method included in the Dragos Platform). For example, defenders may be alerted to a PLC remotely operated from an HMI that has been unusually accessed over a VPN. This could be detected as “SCADA Hijack” behavior.
Living off the land is a popular way for attackers to subversively operate in an environment because they are less likely to be detected by traditional anti-virus. Because every environment is different, generally an adversary needs to heavily invest in interactive operations to take advantage of living off the land techniques, as capabilities need to be stitched together for specific operating environments. Defenders should note that any monitoring tools must be tuned to the environment, otherwise security teams run the risk of alert fatigue due to false positives in security alarms. Targeting specific scripting languages (PowerShell, VBA) and monitoring solutions (WMI, host logs) will produce the biggest payoff. Special scrutiny should be placed inside of the OT environment, as most traditional security tools do not account for ICS protocols or the lack of patching that goes on within operations environments. As a defender, do what works for each specific environment and work towards more robust detections.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances to limit tradecraft proliferation. However, full details on activity group tools, techniques, procedures, and infrastructure are available to network defenders via Dragos WorldView.
[1] Windows Sysinternals – Microsoft
[3] Anatomy of an Attack – Dragos
[7] PsExec v2.2 – Microsoft
[8] Spyware Stealer Locker Wiper: LockerGoga Revisited – Dragos
[9] Least Privilege – U.S.-CERT
[10] Managing Active Directory Trusts in Windows Server 2016 – TechGenix
[11] TrustedSec Unicorn – GitHub
[12] The PowerShell Boogeyman: How to Defend Against Malicious PowerShell Attacks – Rapid7
[13] Practical PowerShell Security: Enable Auditing and Logging with DSC – Microsoft
[14] The CredDefense Toolkit – Black Hills
[15] Insider Threat Security Blog – Stealthbits
[18] Abusing Windows Management Instrumentation… – BlackHat
[19] The Leaked NSA Spy Tool That Hacked the World – Wired
[20] https://www.dragos.com/resource/raspite/
[21] Detecting Malicious SMB Activity Using Bro – SANS
[22] Dan Gunter & Daniel Michaud-Soucy – Stateful Protocol Hunting– YouTube
[23] The Four Types of Threat Detection – Dragos
Ready to put your insights into action?
Take the next steps and contact our team today.
