Publicly and semi-publicly available data, referred to as open source intelligence (OSINT), can enable an adversary to develop targeting, identify access and ingress to a target, and understand how a target may respond to disruptive attacks on infrastructure. Adversaries who target Industrial Control Systems (ICS) for disruptive purposes seek open source information to plan and execute attacks that are different from adversaries targeting traditional enterprise resources. For example, Dragos observed adversaries conducting ICS-targeting activities that sought data about energy infrastructure and physical processes necessary to recover from a compromise. With this data, an adversary could target operational functions that are pertinent to recoverability to further the consequences of an attack.
Adversaries target industrial entities for a variety of reasons. Attacks on ICS entities that serve critical functions within society can be used to further political, economic, or national security goals. Depending on an adversary’s objective, attacks can be used for messaging purposes or retaliation. The potential impact may extend to citizens of a target’s community. Understanding critical infrastructure can put an adversary at a tactical advantage in times of conflict to establish a foothold as a contingency option when conflict occurs.
Targeting ICS can also provide monetary value to an adversary. ICS entities increasingly experience ransomware attacks that, in many cases, disrupt operations. For some companies, disrupting operations can have significant daily financial impacts, costing thousands and sometimes millions of dollars in downtime. In these cases, an operator may be more willing to pay a ransom to unlock computers and limit downtime, especially if proper backups are not maintained. For example, in July 2020, wearables manufacturer and Global Positioning System (GPS) service provider Garmin experienced a ransomware attack and opted to pay an undisclosed ransom to get its operations back online.
ICS environments may also be more insecure than traditional enterprise systems, especially for entities with immature cybersecurity postures. This can be due to legacy operating systems in use across various environments and inadequate segmentation. It is not uncommon to observe outdated Windows operating systems, such as Windows XP or Windows 7, within ICS due to the interoperability of some ICS devices and limitations on patch management. ICS systems are fundamentally complex, and security mechanisms like patching are conducted based on weighing the risk of compromise against the outcome of a potential cyberattack. Practicing defense-in-depth, including conducting OSINT risk assessments to strengthen external security postures and limiting the ability for adversaries to operationalize public information, can prevent initial access and movement within an operational environment.
By identifying and prioritizing data that could be used in OSINT collection, defenders can establish methods to reduce the availability of potentially high-risk company and user data and limit the information an adversary can use in a potential attack.
OSINT covers a wide variety of applications. Fundamentally, OSINT refers to the collection of publicly and semi-publicly available information that is used to inform multiple functions including intelligence gathering and reporting, business and policy analysis, and adversary attack development. For the purposes of this blog, we will focus on OSINT from a cyber threat intelligence perspective, with applications for ICS asset owners, ICS operators, and adversaries.
Dragos advises leveraging consequence-driven security assessments to identify adversary objectives and how to combat them. The Dragos Crown Jewel Analysis model of consequence-driven ICS cybersecurity scoping helps defenders visualize how an adversary would access the system to achieve a specific consequence. By identifying assets within the system and the functional outputs and dependencies, the level of exposure, and interaction between each network layer, organizations can visualize how an adversary may achieve a specific consequence by targeting different elements within the system.
How to collect OSINT data
It is important that OSINT assessments leverage experience and data across multiple teams. Security operators and network technicians from Information Technology (IT), incident responders and forensic specialists, security operators and engineers from ICS environments, and physical security specialists should be consulted while conducting the assessment. These individuals can provide insight into the value of information from an adversary perspective and how OSINT can enable potential attack scenarios. Additionally, business units including human resources and legal should also be consulted to identify publicly available information and the requirements or policy functions the information serves.
A detailed map of the network should be developed and maintained to visually describe where information is hosted, stored, and maintained via system diagrams, flow charts, or network maps. The map should also detail context of the information hosted. For example, when evaluating a web portal that hosts contractor information and third-party network access, the content of the information hosted should be as detailed as the technical specifications of the actual hosting server. The quality and quantity of useful data should be noted and assessed if additional intelligence can be generated from it in aggregate.
Source identification is also an important step in the collection process. Defenders can use the resources described above to find relevant, publicly available information. However, sources will vary for individual companies. Asset owners and operators should also consider information exposed by third-party entities that could be used in reconnaissance operations. For example, a vendor may publish case studies or press releases describing how customers implement specific products or services within their operations environment, which could provide adversary insight into what technologies are used in a target environment.
What to do with it
Once data is collected, users should determine how an adversary may operationalize data to achieve objectives outlined in potential attack scenarios. Data should be assigned severity scores on the risk that data poses to the organization, based on the matrix in Figure 1. For example, information that could facilitate initial access and is easily accessible to the adversary should be assigned a higher score compared to information that does not enable an adversary to fulfill an attack objective and is difficult to obtain.
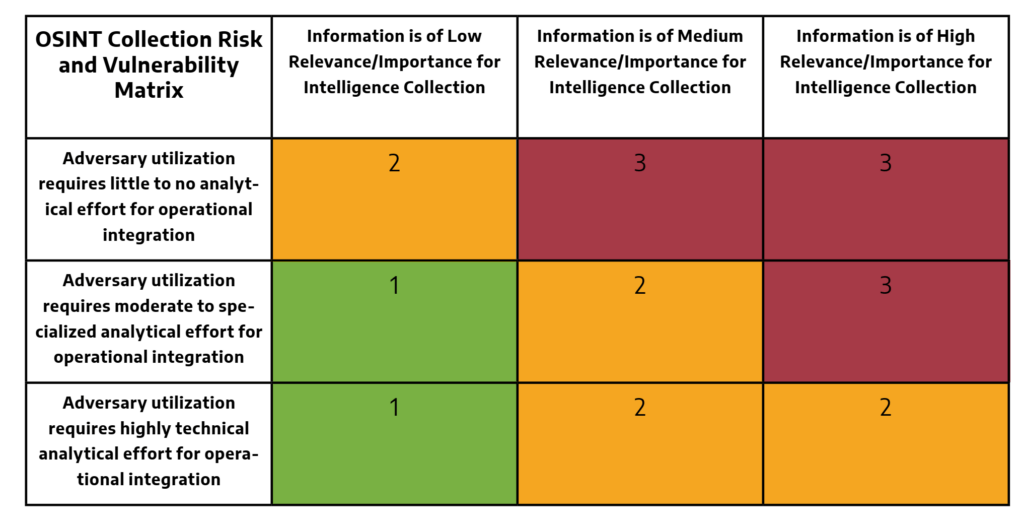
Once defense and mitigation priorities are established, users should identify corrective actions to prevent or lower the risk of adversaries exploiting vulnerabilities or operationalizing information identified in the previous stages of the assessment. These can include issuing patches to vulnerable hardware and applications, removing sensitive data from public websites or databases, implementing MFA to access documentation on cloud storage systems, and changing default passwords on devices within the ICS.
Users should conduct this section of the assessment in two parts: one for hardware and physical systems and the other for software and user policies. Each assessment should include a description of the vulnerability or issue identified, how the company can correct it, and the resources required to do so. The assessment should include any potential obstacles that prevent the company from implementing the recommended fixes.
Based on the information gathered and the assessed risk to the organization, users should implement remediation plans that focus on the most critical to least critical information for adversary operationalization. Plans should be documented and include realistic timelines required to address issues and identify the entity responsible for addressing, removing, or correcting information and vulnerabilities.
Once an assessment is completed, the results should be shared across teams. This includes entities like human resources, who may need to alter job descriptions based on feedback, and public policy teams, who regularly share publicly accessible data with regulators, municipal, state, and federal agencies.
Best practices for industrial OSINT
Conducting regular OSINT collection risk assessments as part of quarterly or bi-annually scheduled cybersecurity reviews can improve an organization’s defense against adversary operationalization of publicly available information and exploitation of known vulnerabilities. By following the framework introduced above, defenders can better identify potential risks to an organization, understand the risk of publicly exposed data, and create mitigation strategies that effectively reduce risk. If you’d like to read the full whitepaper, complete with examples and a Priorities of Defense and Mitigation (PODAM) worksheet, follow the link below.

Ready to put your insights into action?
Take the next steps and contact our team today.