Experienced cybersecurity professionals will tell you that you can’t secure the systems you don’t know about, which is why asset visibility is so crucial no matter what kind of technology infrastructure you’re defending.
Asset visibility in industrial control system (ICS) environments provides industrial asset owners and operators and security staff with the knowledge and insight necessary to build a mature operational technology (OT) cybersecurity program. When organizations can get accurate and timely views into the assets running on their industrial networks, the benefits are cascading.
This is the third blog in a series that we’re publishing to explore these benefits. The first couple of posts touched on how an OT asset visibility program can offer trustworthy asset verification and a solid view into what ‘normal’ looks like in an industrial operations environment. And, these benefits are just the tip of the iceberg.
When done right, asset visibility doesn’t just provide an inventory list of assets in use within an environment. It also visualizes the relationships and communications between them.
Knowing the Risks of Your ‘Low-Risk’ Assets
Outside of the most critical OT assets, the biggest risks sometimes hide in the spaces between OT systems rather than in the assets themselves. It’s the unknown and unseen connections between devices that can expose industrial infrastructure to the most damaging risk potential.
While industrial organizations almost never intentionally allow highly critical OT assets to be internet-accessible, they are sometimes less vigilant about external connectivity to seemingly insignificant hardware or assets. The trouble is that these externally facing ‘lower-risk’ assets may serve as pivot points to higher value targets.
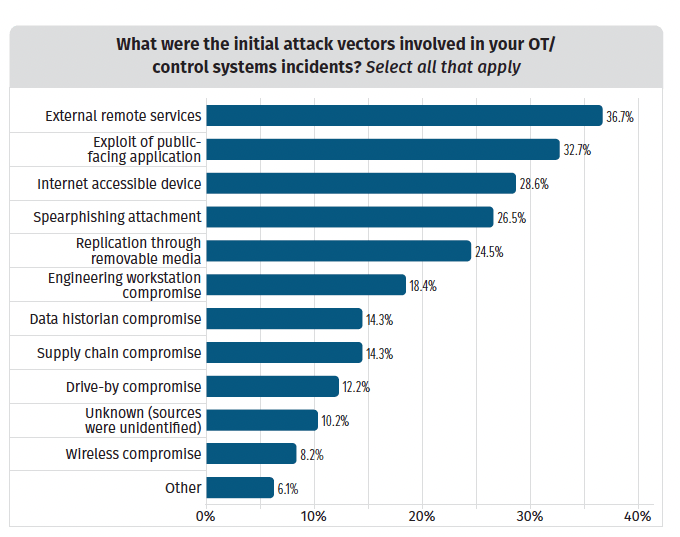
Sometimes the communication pathways between OT assets allow for indirect connections. It may take an attacker several lateral steps to touch a high-value target from a remote connection, and without some visualization those communication pathways often remain unseen.
How Asset Mapping Improves OT Network Security
Asset visibility provides a map into the communication pathways that are inherent within an OT system. For example, mature asset visibility capabilities make it easier to monitor an organization’s OEM and third-party management communication channels to ensure they’re adhering to their scope of contract and not introducing unnecessary risk to the ICS ecosystem. This includes keeping a lookout for communication paths that touch other systems, and ensuring vendors are only doing work during approved change control windows.
Asset mapping illustrates how many hops away assets are from one another to offer security analysts and operators an intuitive look into how well assets are segmented from one another. This is crucial considering how much of OT cybersecurity depends upon isolation of systems, network segmentation, and network monitoring to effectively manage risk.
According to a recent Dragos Year in Review report, some 88% of our professional services engagements involved significant issues and weaknesses in network segmentation. This often stems from a lack of visibility into the relationships that assets have with one another. Recent figures from the Ponemon Institute show many organizations are misaligned on their OT cybersecurity priorities.
When looking at the most commonly cited security practices in industrial environments, four out of the top 10 (seen in green, below) involved asset segmentation or network monitoring. Asset discovery and management didn’t make the cut for top 10 practices — cited only by 29% of organizations as a practice they engage in (seen in red, below).
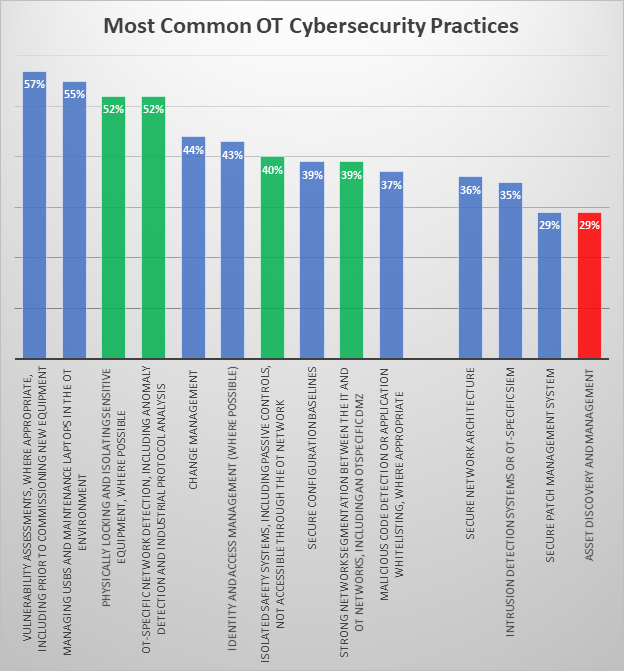
The problem is that it is difficult to validate that assets are truly segmented from one another – and to track how they communicate – without first mapping asset relationships. This visual validation is one of the numerous benefits that an OT asset visibility program supported by automated collection can bring to an industrial organization.
Learn More About Asset Visibility for Industrial Environments
There are other benefits of asset visibility, and we’ll tackle them all in this series. In our next blog post, we’ll dive into how asset visibility can improve efficacy of threat detection methods in OT networks.
For more on the value asset visibility brings to improving your organization’s security posture, download the Dragos whitepaper, “10 Ways Asset Visibility Builds the Foundation for OT Cybersecurity” or see our related infographic.
Ready to put your insights into action?
Take the next steps and contact our team today.