As organizations continue to undergo digital transformation, the convergence of IT and operational technology (OT) networks has become increasingly prevalent. However, this shift comes with its own set of challenges, including heightened cybersecurity risks. Remote access, shared credentials, and unchecked communication can pose significant threats to critical industrial control systems (ICS) and OT assets that lack proper network segmentation. Recent studies indicate that only 21 percent of industrial organizations have achieved OT cybersecurity maturity, with the IT-OT cybersecurity gap being a major impediment to progress.
In this blog, we will explore the challenges associated with bridging the IT-OT cybersecurity divide, the importance of improving OT cybersecurity, and how enhanced Security Operations Center (SOC) capabilities can help organizations bolster their cybersecurity posture.
The IT-OT Cybersecurity Gap
Several factors contribute to the IT-OT cybersecurity gap:
- Cultural Differences: A significant disparity often exists between OT engineers, security professionals, and IT staff in terms of their understanding of and approach to cybersecurity.
- Technical Differences: Traditional IT cybersecurity best practices may not be directly applicable to OT environments, which require unique considerations such as patch management and compatibility with industrial automation equipment vendors.
- Lack of Ownership: Ambiguity surrounds who should take the lead in managing industrial cyber risk, implementing necessary controls, and supporting cybersecurity initiatives.
To bridge the IT-OT cybersecurity gap and improve the maturity of OT cybersecurity programs, organizations must consider strengthening Security Operations Center (SOC) capabilities. Building specialized industrial SOC competencies and toolsets and integrating them into a broader enterprise SOC program can create a defensible architecture and accelerate readiness for OT cybersecurity risks.
Hear our experts discuss how Dragos and Splunk approach risk management and how to overcome the OT-IT divide.
Watch the on-demand webinar now.
Watch NowThe Challenges of Bringing OT Security into the SOC
The time required to detect, investigate, and remediate cybersecurity incidents in ICS and OT environments is alarmingly high, averaging around 316 days and costing organizations over $2.9 million per incident. This delay is unacceptable, especially considering the potential risks to financial and personal safety.
Organizations have faced difficulties in integrating OT into their enterprise SOC operations due to:
- Lack of Visibility: Blind spots across data silos and the OT network hinder comprehensive threat detection.
- Expanding Attack Surface: Evolving threats and hybrid networks pose increased risks.
- Tooling Complexity: Managing diverse and complex cybersecurity tools.
- Resource Constraints: A shortage of OT-skilled cybersecurity professionals.
- SecOps Inefficiency: SOC operators may suffer from alert fatigue and the burden of repetitive tasks.
Why OT Cybersecurity Is Different
The fundamental challenge in improving OT cybersecurity lies in the fact that OT systems are inherently different from IT systems. They use distinct network protocols, configurations, and face unique adversaries. Moreover, the risk landscape for OT assets differs significantly from that of IT. While IT primarily concerns data and intellectual property, OT focuses on safety system control, electrical grid stability, and plant operations.
The Solution: Dragos and Splunk Integration
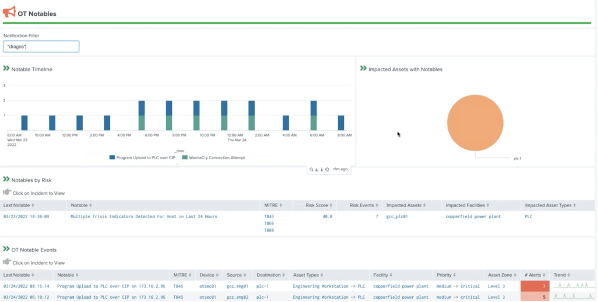
To address these challenges and bridge the IT-OT cybersecurity gap. Dragos and Splunk have developed a powerful integration. This integration combines Splunk Enterprise Security with the Dragos OT Security Add-on, which collects and aggregates data from multiple sources, including the Dragos Platform, allowing users to easily index, search and correlate events across enterprise and OT networks making it an effective tool for empowering security teams and offering SOC teams a seamless way to create a comprehensive view of their IT and OT cybersecurity posture.
Key benefits of this integration include:
- Enhanced OT Visibility: Complete asset discovery, threat detection, vulnerability management, and effective incident response for improved OT cybersecurity posture.
- Reduced Alert Fatigue: The Dragos Platform helps pinpoint malicious behavior, providing context-rich alerts and reducing false positives for more effective threat detection.
- Improved Collaboration: By leveraging technology from Splunk and Dragos, organizations can ensure maximum visibility across both IT and OT networks, leading to better threat detection, response, and mitigation.
Download our free whitepaper on planning for the future of the industrial SOC and how to implement overarching IT-OT security initiatives.

Ready to put your insights into action?
Take the next steps and contact our team today.
