CHERNOVITE
Since 2021
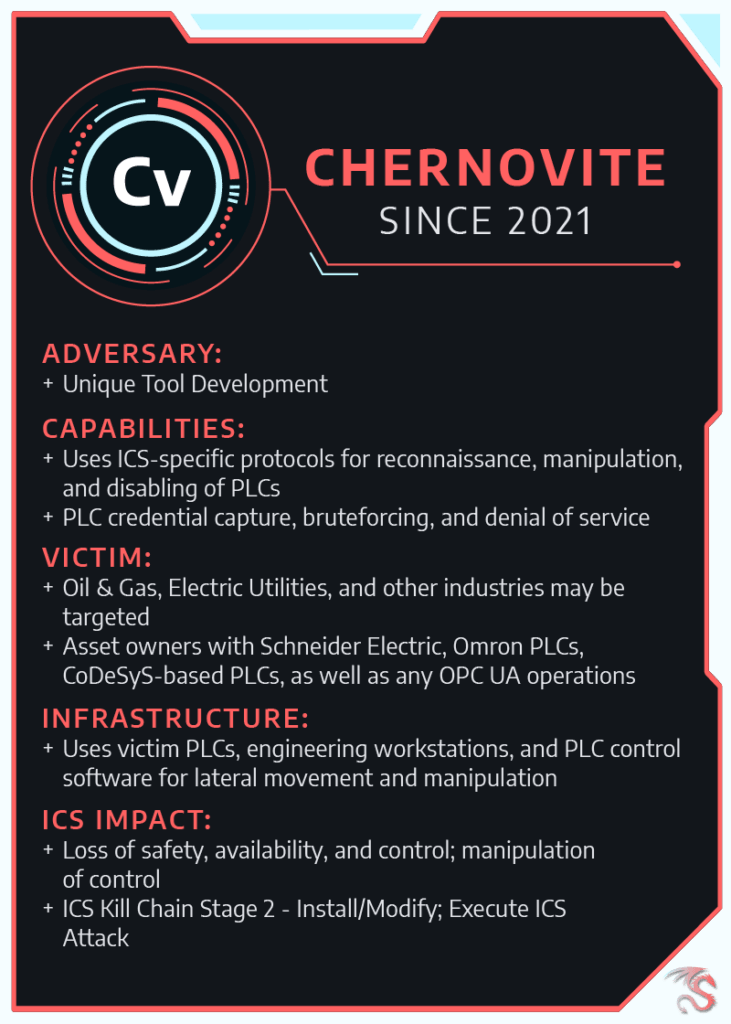
CHERNOVITE has the capability to disrupt, degrade, and potentially destroy industrial environments and physical processes in industrial environments.
Through normal business, independent research, and collaboration with various partners in early 2022, Dragos identified and analyzed the capabilities of a new ICS-tailored malware PIPEDREAM. PIPEDREAM is the seventh known ICS-specific malware following STUXNET, HAVEX, BLACKENERGY2, CRASHOVERRIDE, and TRISIS.
CHERNOVITE has developed a highly capable offensive ICS malware framework. PIPEDREAM provides operators with the ability to scan for new devices, brute force passwords, sever connections, and crash the target device. To accomplish this, PIPEDREAM uses several different protocols including FINS, Modbus, and Schneider Electric’s implementation of CoDeSys.
Components of PIPEDREAM represent the ability to track the evolution of a new ICS capability based on known techniques from prior attacks. CRASHOVERRIDE and the associated Activity Group, ELECTRUM, exploited the OPC-DA protocol to manipulate breakers and switch gear. CHERNOVITE, on the other hand, uses the newer but comparable OPC-UA protocol.
At the highest level, the PLC-related components of PIPEDREAM provide the adversary with an interface for manipulating targeted devices. It also contains tools for intrusion operations against Windows devices. PIPEDREAM relies on several ubiquitous technologies to facilitate intrusion and exploitation.
Dragos assesses that PIPEDREAM has not yet been deployed in the wild. This is a rare case of accessing and analyzing malicious capabilities developed by adversaries before their deployment and gives defenders a unique opportunity to prepare in advance. The Dragos team assesses with high confidence this capability was developed by a state actor with the intention to leverage it in future operations. PIPEDEDREAM malware is targeted to equipment in liquefied natural gas (LNG) and electric power environments, but it is reasonable to assume that CHERNOVITE could easily adapt the capabilities of PIPEDREAM to compromise and disrupt a broader set of targets.
Dragos threat intelligence leverages the Dragos Platform, our threat operations center, and other sources to provide comprehensive insight into threats affecting industrial control security and safety worldwide. Dragos does not corroborate nor conduct political attribution to threat activity. Dragos instead focuses on threat behaviors and appropriate detection and response. Read more about Dragos’s approach to categorizing threat activity and attribution.
Dragos does not publicly describe ICS activity group technical details except in extraordinary circumstances in order to limit tradecraft proliferation. However, full details on CHERNOVITE and other group tools, techniques, procedures, and infrastructure are available to network defenders via Dragos WorldView.