Dragos first disclosed four new threat activity groups targeting ICS/OT last month in the ICS Cybersecurity 2020 Year in Review report. In this blog post, we will provide more information on one of the new groups: VANADINITE. The fundamental assessment of threats tracked by Dragos is that they are explicitly attempting to gain access to ICS networks and operations or are successful in achieving access, not simply trying to gain access to an industrial organization. To learn more about ICS threat activity groups and how they’re created, we invite you to read our blog post “Uncovering ICS Threat Activity Groups.”
Activity Group: a set of intrusion events related with varying degrees of confidence by similarities in their features or processes used to answer analytic questions and develop broad mitigation strategies that achieve effects beyond the immediate threat.
VANADINITE Activity Group Overview
The new VANADINITE activity group targets electric utilities, oil and gas, manufacturing, telecommunications, and transportation. VANADINITE’s extensive targeting across multiple industrial verticals makes this entity a threat to ICS organizations and entities supporting operational functions.
VANADINITE targets a geographically broad region including North America, Europe, and with evidence of activity in Asia and Australia. Observable VANADINITE activity includes ICS Kill Chain Stage 1 initial access to networks belonging to companies that have Operational Technology (OT) environments. It is possible its intrusion activity, including developing footholds in target environments, could enable lateral movement to OT networks or supporting infrastructure. This could allow for possible disruptive or destructive impacts.
Dragos assesses that the majority of VANADINITE operations are limited to accessing victim infrastructure and conducting information-gathering activities. However, the ColdLock ransomware which Dragos attributes with low confidence to VANADINITE has caused significant IT disruption at oil and gas companies that indirectly impacted gas station operations and related operations throughout Taiwan.
VANADINITE conducted extensive intrusion campaigns largely focused on industrial entities in 2019. The group exploited vulnerabilities in external-facing network and security devices to gain access to victim networks. Indictments published by the United States (U.S.) Department of Justice associate activities linked to VANADINITE with operators working on behalf of the People’s Republic of China (PRC). VANADINITE has some overlap with a group called Winnti in public by multiple security companies, governments, and researchers. However, Winnti activity is expansive and poorly defined in open-source reporting. VANADINITE has considerable overlap with the group Microsoft calls LEAD, a subset of Winnti activity.
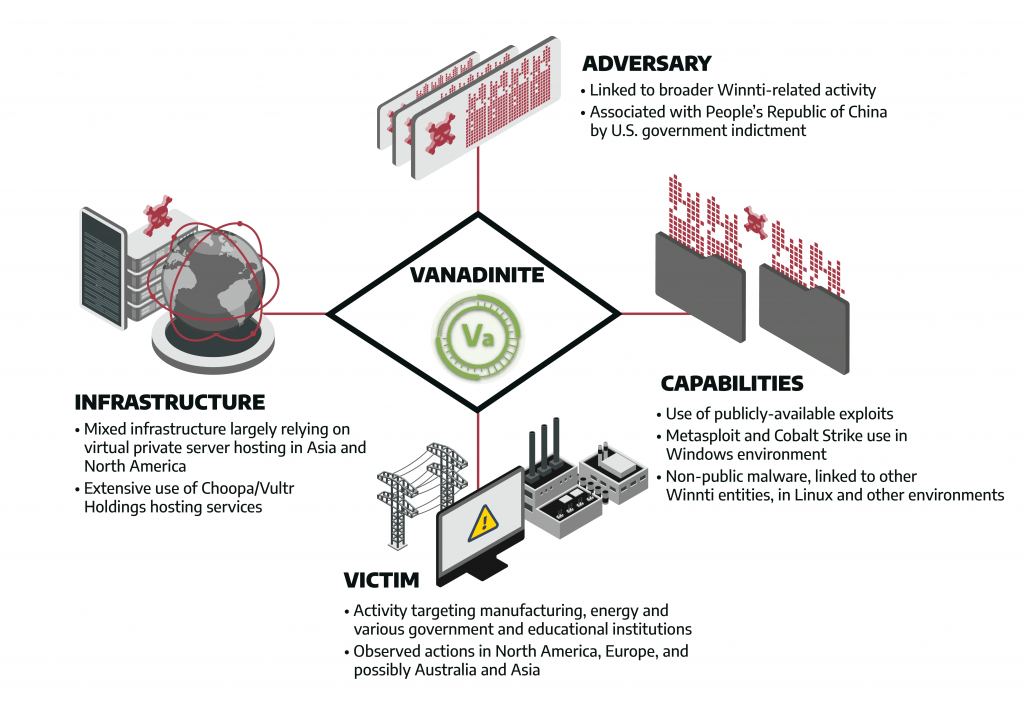
VANADINITE relies on adversary-owned and operated infrastructure using the Choopa/Vultr Holdings hosting services and compromised Virtual Private Server (VPS) hosting in Asia and North America. Overall geographic infrastructure locations focus on East Asia and North America. VANADINITE exploits external-facing network devices and relies on publicly disclosed vulnerabilities with available exploits including CVE-2020-8193, a vulnerability in Citrix ADC, Gateway, and SD-WAN WANOP devices.
Dragos assesses with high confidence that VANADINITE will continue to leverage this technique of exploiting recently disclosed vulnerabilities for initial access because of the success obtained using this method previously. Asset owners and operators should treat vulnerabilities in external-facing network appliances as a serious issue, because multiple ICS-targeting adversaries use this technique.
Based on the group’s methodology for initial access operations, Dragos assesses with high confidence VANADINITE will rely on access to compromised equipment to gather valid credentials to obtain lateral movement within a compromised environment. These credentials can be used for remote logon and process execution to move throughout the victim network. In an ICS environment, such access could enable reconnaissance activities and establish a foothold for future ICS-disruptive events.
Although VANADINITE operations included non-industrial verticals, the group appears focused on industrial targets and possible entities linked to industrial networks or operators such as telecommunication providers and transportation companies that may facilitate indirect access to victim networks. Compromising such entities may enable supply-chain compromise, leveraging trusted relationships between companies and their vendors, service providers, or technology services to bypass security protection mechanisms for initial access.
VANADINITE gains initial access across multiple organizations through rapid, opportunistic use of publicly disclosed vulnerabilities in external-facing applications and network appliances. VANADINITE is not linked to any specific industrial disruption, destruction, or control system intrusions; however, Dragos assesses with moderate confidence the group conducts long-term target and access development to enable future operations.
Detecting and Mitigating VANADINITE Network Exploitation
VANADINITE operations consist of network exploitation of vulnerable systems. There are multiple strategies for detecting or mitigating these attacks.
Host
- Ensure remotely and externally accessible services are patched as soon as possible, especially those operating within the OT environment or on the Demilitarized Zone (DMZ). Prioritize devices targeted by this group, including Citrix and Cisco networking appliances and Virtual Private Network (VPN) assets. Multiple adversaries have migrated toward exploitation of publicly disclosed vulnerabilities as an initial access mechanism. These operations take place shortly after vulnerability or exploit proof of concept disclosure, meaning asset owners must prioritize patching and apply fixes quickly.
- Implement Multi-Factor Authentication (MFA) for network and host logons in as many applications as possible, focusing on external-facing network infrastructure and dual-homed industrial assets. Credential capture and reuse is one avenue for follow-on lateral movement from initial compromise.
Network
- Monitor for scanning and exploit activity against external-facing services using DigitalOcean and Vultr Holdings/Choopa infrastructure. Implement allow-lists for known good IP addresses associated with required business activity. Identify patterns such as favored Autonomous System Numbers (ASNs) for this activity not related to legitimate, business-critical communication.
- Ensure proper network segmentation between enterprise and Operational Technology (OT) networks and related assets to minimize exposure of follow-on devices and hosts from VANADINITE, even if an external-facing application is compromised.
Control System Networks
- Lateral movement aided by credential capture and reuse can enable control system network access. Asset owners should apply MFA to control system network access and use a separate authentication schema than that used in enterprise networks, including enforcement of separate passwords.
- ColdLock ransomware used Active Directory (AD) compromise to spread. Asset owners and operators should create dedicated security groups for ICS systems within a shared AD environment and limit permission for deploying Group Policy Objects (GPOs) or other changes to only a subset of administrators.
Detections for all VANADINITE behaviors are available in the Dragos Platform.
ICS Considerations for the Future
VANADINITE activity focuses on initial access and espionage operations. Dragos assesses VANADINITE may continue to use ransomware in future operations targeting industrial entities, and such attacks could have indirect, disruptive impacts to operations.
Dragos assesses with high confidence VANADINITE will continue to exploit public vulnerabilities in network and remote access infrastructure. Further, Dragos assesses with high confidence VANADINITE will continue targeting ICS entities in North America, Europe, and the Asia-Pacific (APAC) region, and operations will remain focused on initial access and information gathering operations, in addition to possible ransomware attacks. Dragos will continue to track VANADINITE and provide timely, relevant updates on any ICS-specific malware or attack development.
Ready to put your insights into action?
Take the next steps and contact our team today.
