How well prepared are you to face the OT cybersecurity challenges that lie ahead? The changes in the operational technology (OT) cybersecurity landscape last year were a narrative filled with twists and turns. The Dragos 2023 OT Cybersecurity Year in Review turns this narrative into lessons and strategies, guiding you to a more secure industrial future – it is our roadmap to understanding and navigating these challenges in 2024.
What You Can Expect in the 2023 Year in Review
Here is a snapshot of what we’ll cover in Dragos’s 2023 OT Cybersecurity Year in Review:
- We introduce new Dragos Threat Groups identified in 2023 and other observed adversary activity in the past year.
- We summarize and drill down into the significant growth in ransomware attacks impacting industrial sectors.
- We cover increased activity by hacktivists and nation-state adversaries driven by geopolitical events in the past year.
- We discuss how the standardization of industrial control systems (ICS) environments are leading to impacts on multiple organizations and industries with single portable exploits.
- We feature the regulations and guidelines that helped focus and strengthen OT cybersecurity defenses.
Sign Up to Receive the 2023 Year in Review
Be the first to get a free copy of the Dragos 2023 OT Cybersecurity Year in Review.
Pre-Register TodayA Recap From Last Year’s Report
In case you missed it, here’s a recap of the crucial OT cybersecurity insights covered in last year’s report.
State-Sponsored ICS-Specific Malware Impacts Hundreds of Suppliers
Discovered in early 2022, PIPEDREAM is the seventh known ICS-specific malware. It follows STUXNET, HAVEX, BLACKENERGY2, CRASHOVERRIDE, TRISIS, and Industroyer2. The development of this malware demonstrates the risks of increasingly homogenous operational technology systems and modern component-based software.
- PIPEDREAM is the first scalable, cross-industry ICS attack framework; it targets five ubiquitous software components and protocols. Hundreds of suppliers and thousands of devices that use the software and protocols in question are potentially impacted.
- This malware has the potential for disruptive and destructive cyber attacks in OT networks and ICS environments. It is capable of end-to-end cyber attacks; it can be used in Stage 1 and Stage 2 of the ICS Cyber Kill Chain.
2 New Threat Groups Discovered Targeting OT Companies
Dragos began tracking two new threat groups in 2022, bringing the total of OT targeting Dragos-tracked threat groups up to 20. This represents a 300 percent increase in the number of observable OT threat groups active at one time since 2017.
 CHERNOVITE CHERNOVITE | The CHERNOVITE Threat Group is the developer of the seventh ICS-specific malware, PIPEDREAM. This cyber threat group demonstrates considerable knowledge of OT intrusion techniques and ICS protocols. They have capabilities to achieve Stage 1 and Stage 2 of the ICS Cyber Kill Chain. CHERNOVITE is highly motivated, well funded, and skilled in software development methods. |
 BENTONITE BENTONITE | The BENTONITE Threat Group is increasingly and opportunistically targeting maritime oil and gas (ONG), State Local Tribal and Territorial (SLTT) governments, and manufacturing sectors since 2021. BENTONITE conducts offensive operations for espionage and disruptive purposes, targeting vulnerabilities in internet-exposed assets to facilitate access. |
Dragos Threat Intelligence also observed activity by these Threat Groups: KOSTOVITE, KAMACITE, XENOTIME, ELECTRUM, ERYTHRITE, and WASSONITE .
Ransomware Attacks Impacting Industrial Sectors Increased by 87 Percent
Ransomware groups, while not targeting OT environments explicitly, have had a significant impact on OT networks, whether through the integration of operational technology (OT) kill processes into ransomware strains, flattened networks allowing ransomware to spread into OT environments, or precautionary shutdowns that prevent ransomware from spreading to industrial control systems.
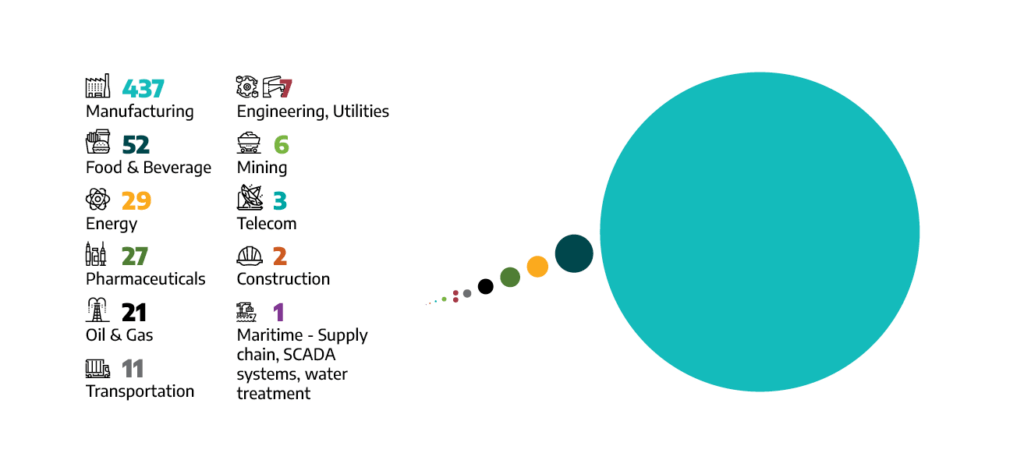
- Dragos tracked 605 ransomware attacks against industrial organizations in 2022, an increase of 87 percent over last year. Political tensions, the introduction of Lockbit Builder, and the continued growth of ransomware-as-a-service (RaaS) all contributed to the increase.
- Dragos assessed that manufacturing accounted for 72 percent of the 2022 ransomware attacks against industrial organizations – nearly twice as much as the other industrial sectors combined. Ransomware groups targeted 437 manufacturing entities in 104 unique manufacturing subsectors.
- Lockbit 2.0 and Lockbit 3.0 conducted 28 percent of the total ransomware attacks in 2022. The Conti ransomware group was associated with 10 percent of attacks, and Black Basta was responsible for 9 percent of attacks.
Many ICS Advisories Contain Errors and Lack Actionable Guidance
For each CVE, Dragos Threat Intelligence independently assesses, confirms, and often revises Common Vulnerability Scoring System (CVSS) scores to enable more effective prioritization, in addition to providing alternative mitigations to patching tailored to OT environments.
- In 2022, Dragos threat intelligence researchers analyzed 2,170 ICS/OT common vulnerabilities and exposures (CVEs) across 461 public advisories.
- One third of advisories analyzed contained errors (34 percent) and 15 percent of CVEs had errors in the CVSS score assigned. Of advisories with errors, Dragos assessed that 70 percent were more severe than had been received at publication.
- Dragos provided missing mitigation advice for 53 percent of advisories in 2022. Ultimately, Dragos recommended patching NOW for only 2 percent of ICS/OT vulnerabilities. NEXT to prioritize are the 68 percent of vulnerabilities that are network exploitable but have no direct operational impact. These ones can often be mitigated by implementing network segmentation and multi-factor authentication.
Industrial Organizations Are Still Struggling with the Basics
The ICS incident responders and OT defenders from the Dragos Professional Services team have consulted on numerous cases where significant time and resources could have been saved with preparation. In 2022, Dragos shared these insights to help OT asset owners avoid issues that increase the time, personnel, downtime, and expense of managing a cybersecurity incident. Key findings we reported to were:
- 80 percent of service engagements had a lack of visibility across OT networks—making detections, triage, and response incredibly difficult at scale.
- 50 percent of service engagements included a finding about improper network segmentation.
- 53 percent of service engagements included a finding of external connections from OEMs, IT networks, or the internet to the OT network.
- 54 percent of service engagements included a finding of shared credentials in OT systems, the most common method of lateral movement and privilege escalation.
The 2023 Year in Review is Now Available!
Get your free copy of the 2023 OT Cybersecurity Year in Review.
Ready to put your insights into action?
Take the next steps and contact our team today.

