Reflected in Knowledge Pack KP-2023-003 is analysis on 300 vulnerable assets including vulnerabilities from Yokogawa, Siemens, Rockwell Automation, Omron, Schneider Electric, Hitachi Energy, WAGO, Phoenix Contact, and Mitsubishi Electric. Over 290 characterizations and 565 detections are included for customers running Dragos Platform 2.2.1. Full release notes are available for registered customers in the Dragos Customer Portal, key highlights of this release are included below.
Characterizations
Of particular interest to customers with substations in the electric sector, Knowledge Pack KP-2023-003 includes several characterizations designed to improve asset identification supporting the IEC-61850 suite of protocols and several vendors that leverage these protocols. This includes ABB and GE devices and firmware, and characterizations using the GOOSE protocol to identify additional GE and SEL devices. Using Ovation System Reg files, we are identifying Emerson Ovation Workstations. Related to the Emerson family of products, ROC Plus modules identify devices grouped behind Emerson Remote Operations Controllers (ROC). Lastly, additional asset identification improvements have been achieved using a new analytic that processes DHCP Parameter Request Lists to extract hardware information and functional roles.
Detections
This Knowledge Pack includes a group of signatures that identify behaviors associated with DNS tunneling, such as large volumes of DNS queries or responses seen over a short period of time. These patterns are normally limited in legitimate traffic but have been observed with Cobalt Strike BEACON DNS Tunneling. Finally, a detection that identifies HTTP traffic containing a User-Agent associated with CCleaner is also included. CCleaner is a legitimate Windows application but has been seen used in supply chain attacks.
Dashboards
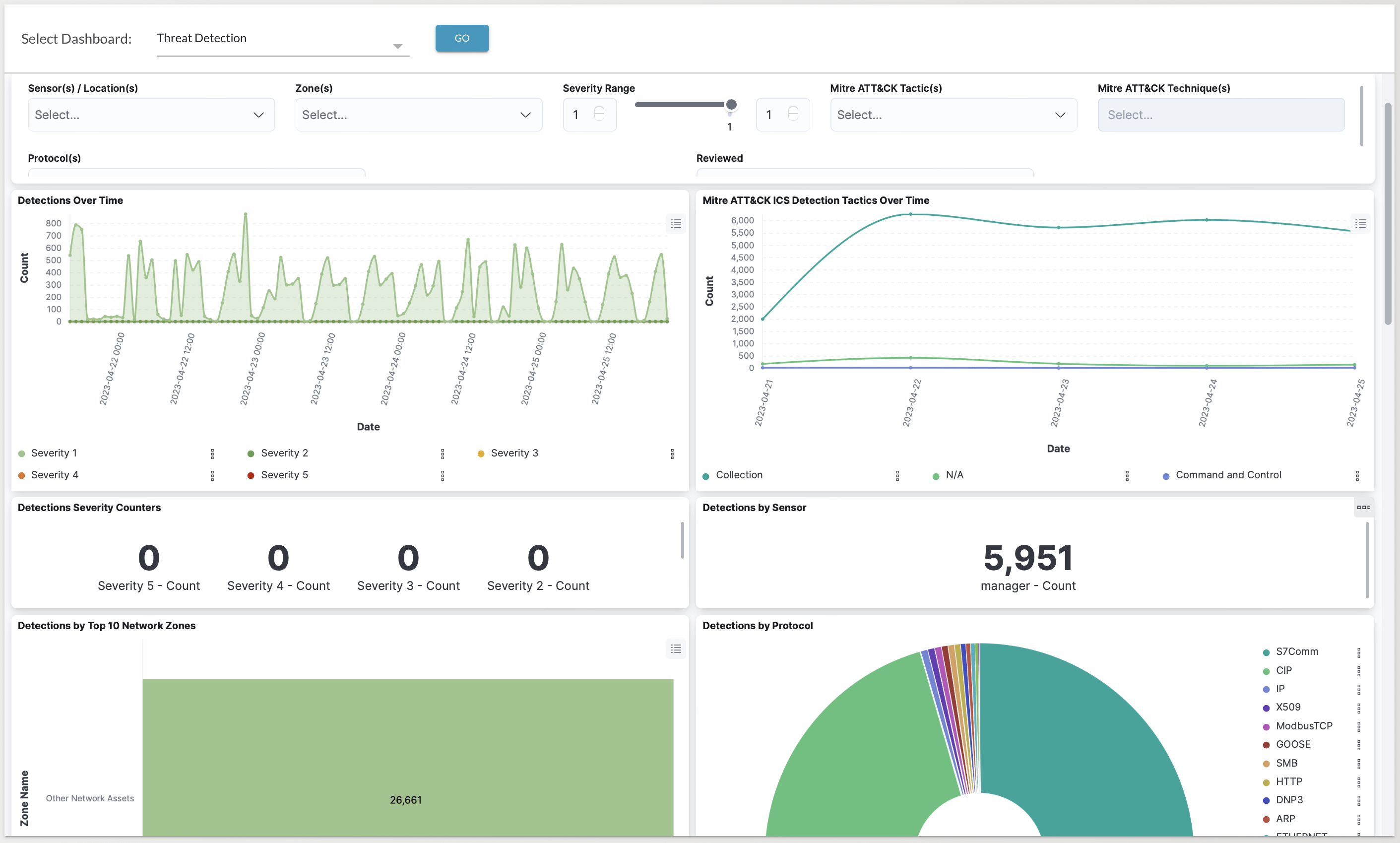
With KP-2023-003 we’re introducing two dashboards – one for Threat Detections and one for Platform Auditing. The first shows a summary of threats detected grouped by criteria such as Sensors, Zones, Severity Range, MITRE ATT&CK Tactic or Technique, and/or Protocols. Detections are displayed using several widgets including ‘Detections over Time’, ‘MITRE ATT&CK ICS Detection Tactics over Time’, ‘Detections Severity Counters’, and ‘Detections by Sensor’ amongst others.
Threat Detection Dashboard
The Threat Detection Dashboard provides an overview of Detections over time by Sensor and Zone and associated MITRE ATT&CK Tactics and Techniques. It allows the user to apply filters based on several different parameters including Severity Range, Protocol, Review status, and more.
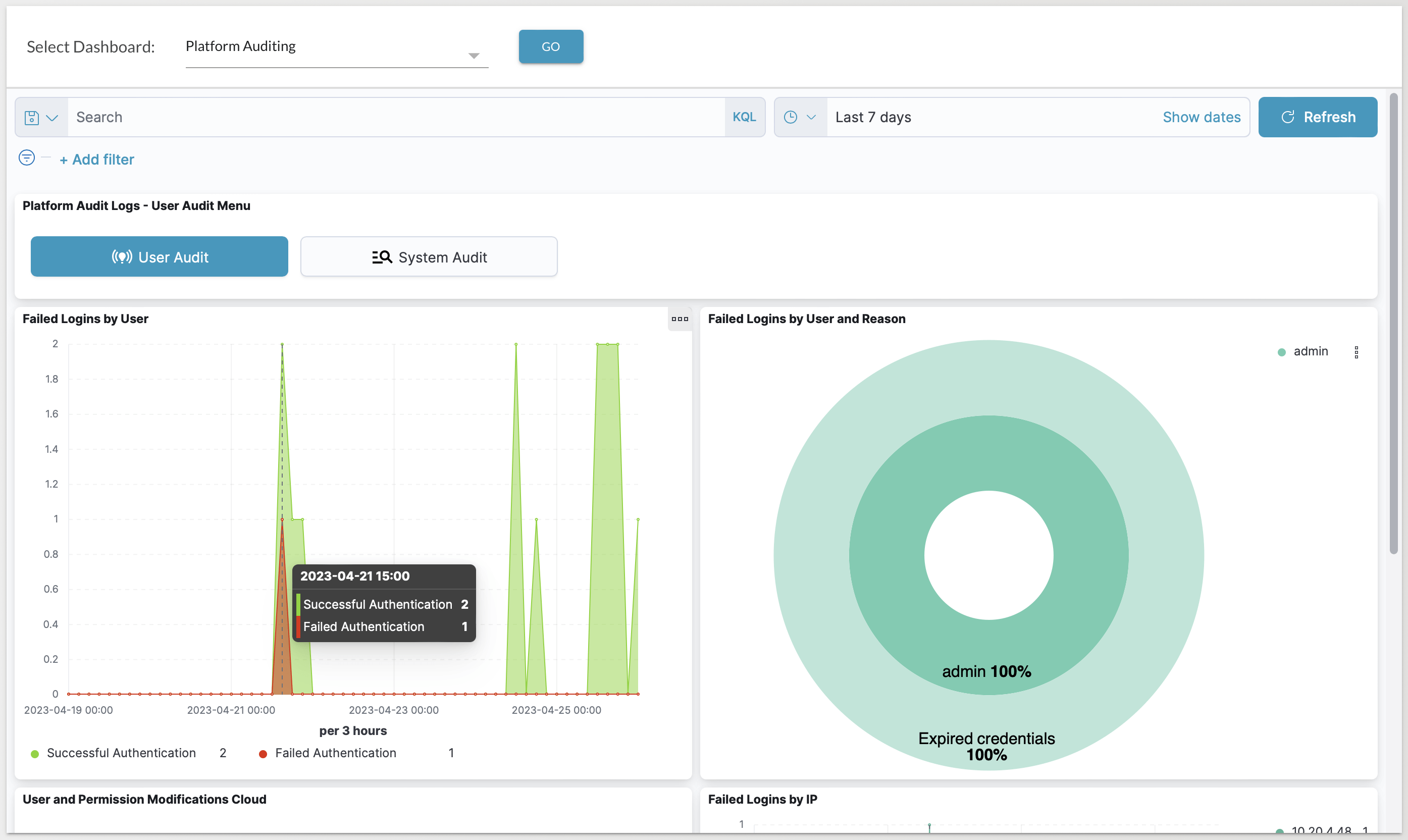
Platform Auditing Dashboard
The second dashboard included is the Platform Auditing Dashboard, which provides a quick overview of User and System audit information. and is available for Dragos Platform 2.2.0 and newer. The Platform Auditing dashboard includes two sub-sections: 1) User Audit and 2) System Audits.
- The User Audit page provides information regarding when users are logging into the Dragos Platform, both successfully and unsuccessfully. For failed logins, it further breaks down which users have the most failed logins and the reason (Incorrect Credentials, Expired Credentials, Account Locked, and so on) and the IP addresses that are triggering the failed logins.
- The System Audit page provides information regarding the time and date when the Platform Pairing Mode Update has occurred as well as Sensor Pairing Requests. Additionally, a histogram of the Sensor Content version for collectors is displayed. A record of when Sensor Content has been updated is also included. Finally, a record of service start-and-stop dates and times are also displayed.
Dragos Platform customers receive regular updates through Knowledge Packs which include enhancements to threat detections, protocol support, asset visibility, and playbooks to equip customers with continuous improvements for their OT cybersecurity operations. Each Knowledge Pack contains the latest exclusive insight from Dragos intelligence teams, streamlining the detection of devices and potential malicious activity across industrial networks. To learn more about Dragos Knowledge Packs and how we continuously incorporate our industry-leading OT expertise into the Dragos Platform, we invite you to read this overview or contact sales@dragos.com.
Ready to put your insights into action?
Take the next steps and contact our team today.