Dragos recently published its’ Dragos 2021 Year In Review report, highlighting four key findings within the Operational Technology (OT) landscape. This blog continues the series that expands on each of these findings. It focuses on the following key finding that: 44% of Dragos services engagements, included findings related to shared credentials.
Dragos considers shared credentials to be accounts that are utilized in both the IT and OT networks, including default accounts and vendor accounts. Leveraging valid accounts for lateral movement is a technique used by nearly all adversaries, even those not focused on industrial control systems (ICS). ICS adversaries seek to discover and compromise these shared accounts because they are frequently used to access critical industrial systems and can enable them to pivot from corporate IT networks to ICS/OT environments.
When performing OT assessments, it is common for Dragos to find the use of shared credentials such as an Active Directory instance or domain that is shared between the IT and ICS/OT environments. However, it is worth noting how much varies depending upon the vertical. Figure 1, shown below, illustrates that while shared credentials are common across the industry, there are some verticals where shared credentials were extremely rare. For example, it is scarce in Electric, Nuclear, and Chemical, but frequently observed in others such in as Rail, Water, and Food & Beverage.
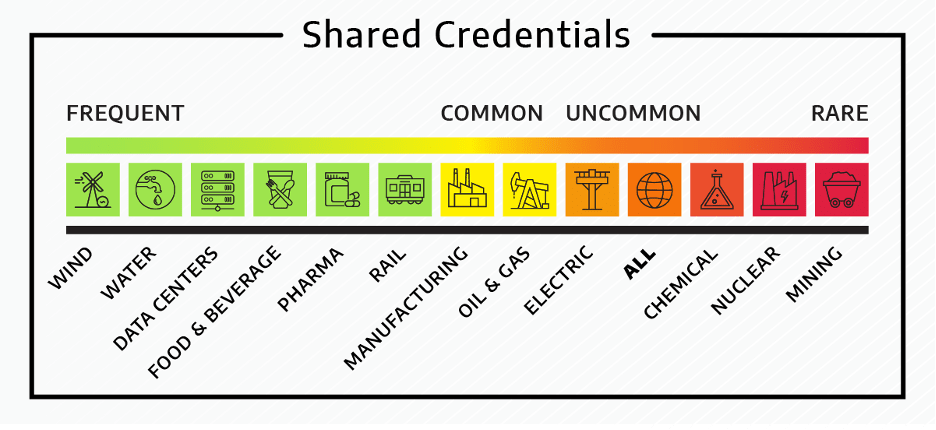
The statistic of 44% of assessments across all OT industries including a finding related to shared credentials between IT and OT systems is not alarming by itself, especially when it represents a positive change compared to the 54% in 2020. However, when combined with another key finding from the Year in Review, such as 77% included a finding of improper network segmentation, the potential consequences of shared credentials being exploited increases significantly.
Combining these two critical findings can lead to a weakening of the security posture and may enable an adversary to easily traverse to ICS assets using the credentials obtained from IT accounts. For example, an adversary could run open-source tools such as BloodHound to map out a target environment, revealing information that could then be leveraged to create a blueprint for a potential attack with their initial foothold. The adversary running the tool will have information showing the path to critical assets, or Crown Jewels, and potential users of interests that may assist in reaching those critical assets which could have a catastrophic event for the target organization. In a previous blog, Dragos explored one way an adversary may leverage the Windows Native Network Shell (Netsh) utility to perform lateral movement between the corporate and OT/SCADA environments.
With the reconnaissance completed (i.e., the blueprint of the environment), adversaries can focus on searching for targets and credentials. They can be used to execute the attack or move forward in their mission. Two of the most common findings that make this extremely easy for adversaries are the use of default credentials and/or credential reuse in these environments. Both will be analyzed here.
Default Credentials
When identifying any control system devices, workstations, servers, or applications, an adversary would likely attempt to leverage a manufacturer or supplier set of default credentials. These credentials are easily found in vendor documentation and online repositories available on the Internet. While the intention of these credentials being created is for the initial configuration and deployment of the device(s), the default accounts commonly have administrative permissions. These types of permissions, if leveraged by an adversary, would allow them to make unauthorized changes to the device(s) or application(s), causing an event that will likely vary in terms of consequences depending on the environment or vertical the change is being made in.
Dragos recommends, wherever possible, enforcing at least the following good practices:
- Ensure credentials are removed from any equipment or changed and audited on a routine basis to ensure compliance with your organizational or governmental policies.
- Deploy an OT network visibility solution, such as the Dragos Platform, to monitor for connections leveraging vendor accounts and default credentials.
- Implement compensating controls and defense-in-depth practices to limit exposure of the device(s) and/or application(s).
Credential Reuse
Another finding that the Dragos team often encounters in assessments is the presence of credential reuse. There is no question that reusing credentials may feel more efficient to your endpoint administrators in maintaining your operating environments, but it’s often overlooked that the same technique is also more efficient for an adversary or activity group to move laterally across your operating environment. Consequently, this type of activity tends to not raise any alarms due to the potential activity not being new in your operating environment, leading the events to go unnoticed or unconsidered. Figure 2, shown below, illustrates how the dangers of credential reuse.
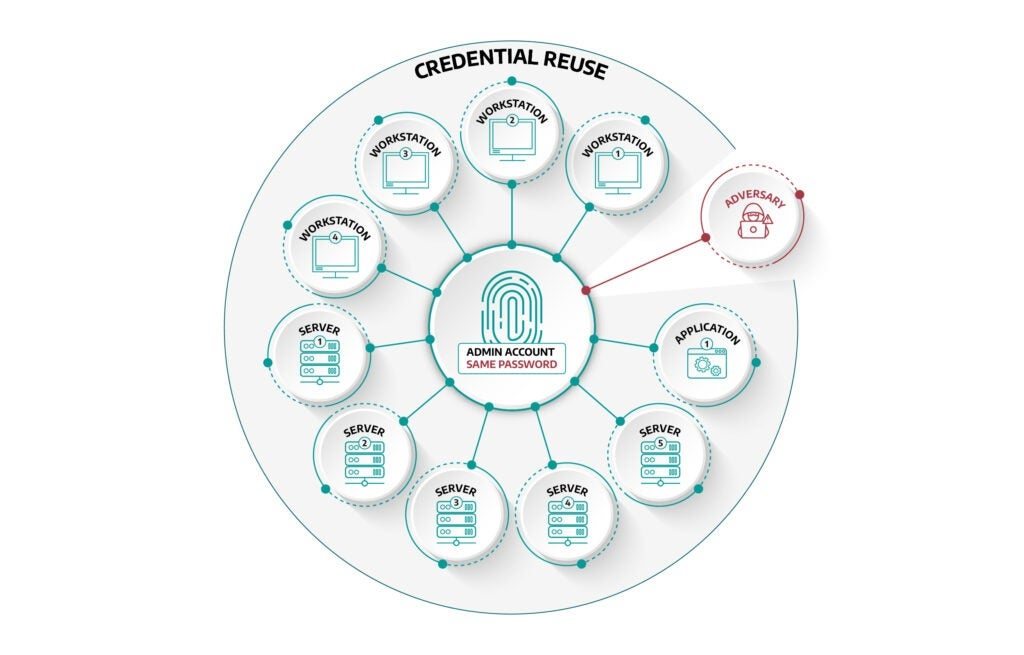
If an adversary or activity group was able to compromise an administrator account, and that administrator account was configured with the same username and password on all of your endpoints, that adversary or activity group now has the capability to perform activities including, but not limited to:
- Laterally moving throughout your operational environment
- Establishing persistence on any number of footholds or endpoints
- Disabling any protective measures put in place (if applicable) on any of the endpoints
- Clearing logs on endpoints to hide their activities and limiting any incident response
Depending on your environment or vertical, the consequences of this type of privilege vary exponentially. It would be relatively difficult to defend against this type of incursion due to the scope of assets the adversary has access to. Dragos recommends that asset owners address these two cases by monitoring the connectivity to OT devices or applications. For example, the Dragos platform passively analyzes network traffic looking for a plethora of misconfigurations and threat behaviors including assets using vendors’ default credentials or passwords traversing the OT/SCADA network in plain text. Details on how the Dragos platform could help with asset visibility are available in the following white paper: 10 Ways Asset Visibility Builds the Foundation for OT Cybersecurity.
In addition to network monitoring, implementing some form of credential management where each endpoint has a unique set of credentials and the credentials for those endpoints are audited and monitored on a scheduled, routine basis is the most complete way to protect against this type of activity. Implementing a password vault solution can take significant time and resources and may even involve changes in the design of your network architecture. For asset owners looking to progress to a password vault solution, Dragos recommends combating credential reuse with a compensating control, such as OT monitoring, until a password vault solution can be implemented. Dragos recommends maintaining OT monitoring of those assets, even after the successful password vault implementation, as the monitoring provides continuous validation of the effectiveness of the vault solution, by altering on new uses of credential reuse.
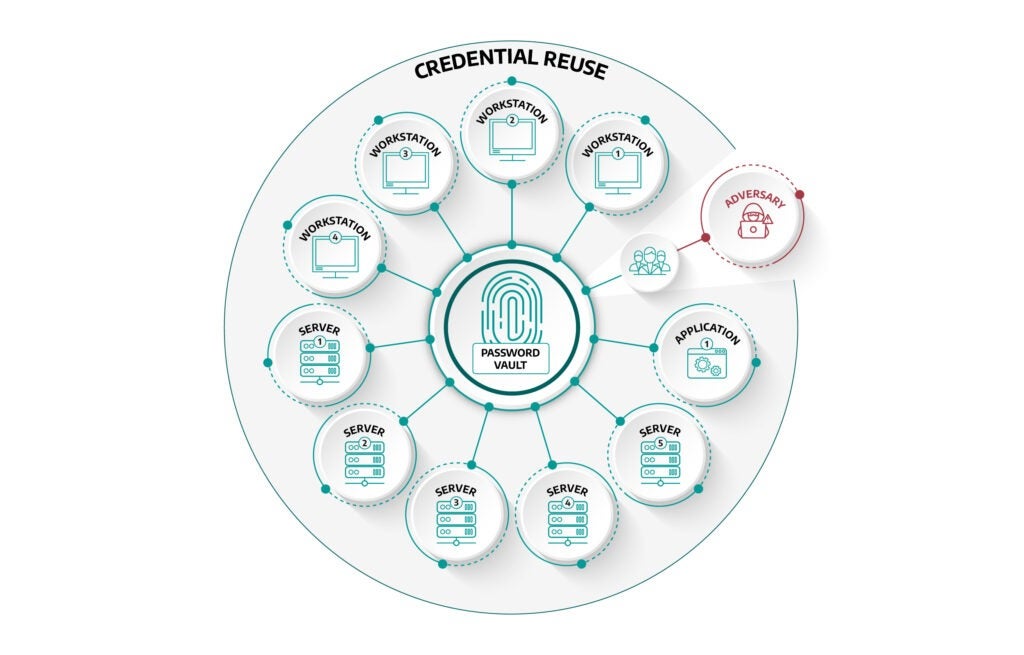
Figure 3, shown above, demonstrates how a solid Credential Management solution can limit the effectiveness of credential reuse for an adversary. Without the solution, shown in Figure 2, if an adversary had compromised an administrator account in your environment, they would have had access to all the endpoints in the environment. However, with a credential management solution deployed, shown in Figure 3, the adversary would have a more difficult time obtaining anything remotely close to the previous example. This is due to the following chain of events needing to be required.
- The adversary would need to identify where the password vault is located.
- If located, they would need to identify a user that has access to the vault.
- If identified, they would need to attempt to compromise credentials to access the vault and work towards bypassing the multifactor authentication that has been implemented.
- If authenticated, they would need to see what the impacted user has access to, which potentially could not be very much depending on who was accessed due to the strict role-based access controls.
There is no longer a single set of credentials used to access every endpoint in the environment. The role-based access controls implemented reduce an adversary’s potential footprint in an environment and would force them to spend a lot of time performing reconnaissance and attempting to bypass the number of additional safeguards in place.
These number of safeguards force additional hops for an adversary or activity group to take before attempting to compromise your operational environment which provides you the availability to monitor, detect, and respond to the attempted activities, which in turn protects your critical assets or Crown Jewels.
Active Directory Instance Shared Between the IT and ICS/OT Environments
Active Directory Domain Services (AD DS) are the core functions of an Active Directory environment that manages users and computers and allows system administrators to organize the data into logical hierarchies.
An environment with a single Active Directory domain across multiple security zones would enable an adversary that obtained user access to enumerate across security zones. Figure 4, shown below, explains how If there is only one domain which includes corporate systems and ICS/OT systems, the barrier to enumeration would be significantly lower than if they had to compromise a second Active Directory environment behind additional firewalls and security controls. The potential impact is even more severe, if the adversary compromised a domain administrator account. With a domain administrator account, they could change AD settings ranging from Group Policy Objects to editing, deleting, or creating users. The adversary may then proceed to use the account(s) to gain access to assets in the ICS/OT networks.
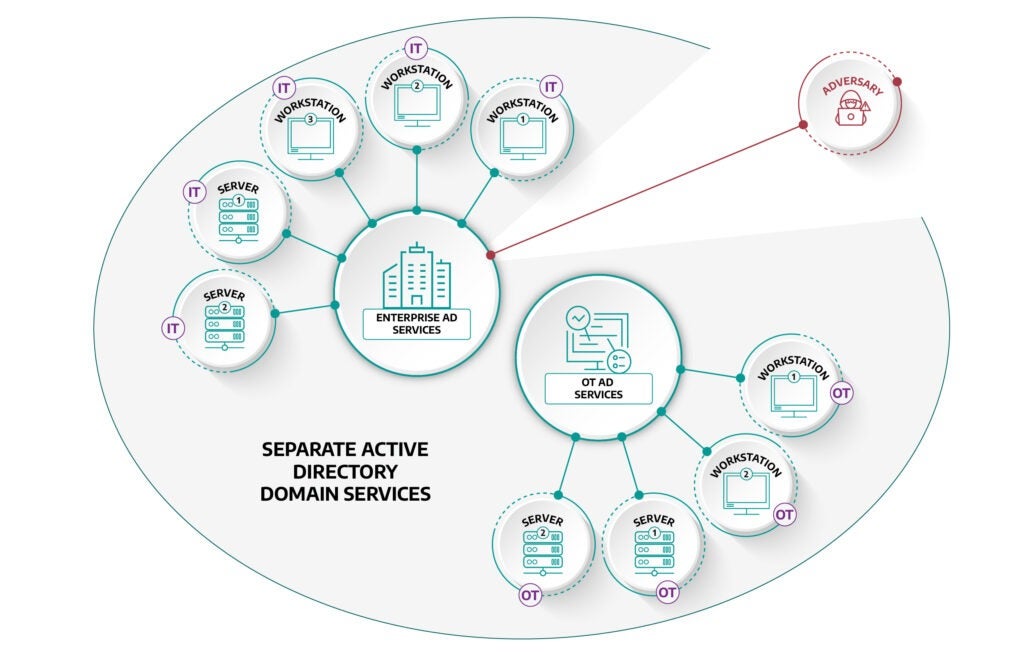
Dragos recommends leveraging a defensive network defensive architecture that limits the lateral movement both north-south (i.e., corporate environment and OT environment) and east-west (i.e., zones of different trust within the OT environment). This includes implementing separate Active Directory domains for the ICS/OT environments completely isolated from the corporate environment. This segmentation reduces the adversary’s ability to pivot into the ICS/OT environment from the corporate network easily. Even if Domain Administrator permissions were obtained on the corporate domain, they could not be leveraged on the other domains unless there are domain trusts, or the credentials are the same on all the domains. Additionally, Dragos recommends utilizing Multifactor Authentication (MFA) for remote connections and OT network monitoring to detect when new or anomalous remote connections are established between IT and OT and analyze of the communications to and from OT devices.

Ready to put your insights into action?
Take the next steps and contact our team today.
