Dragos first disclosed four new threat activity groups targeting ICS/OT last week in the ICS Cybersecurity 2020 Year in Review report. In this blog post, we will provide more information on one of the new groups: KAMACITE. The fundamental assessment of threats tracked by Dragos is that they are explicitly attempting to gain access to ICS networks and operations or are successful in achieving access, not simply trying to gain access to an industrial organization. To learn more about ICS threat activity groups and how they’re created, we invite you to read our blog post entitled “Uncovering ICS Threat Activity Groups.”
Activity Group: a set of intrusion events related with varying degrees of confidence by similarities in their features or processes used to answer analytic questions and develop broad mitigation strategies that achieve effects beyond the immediate threat.
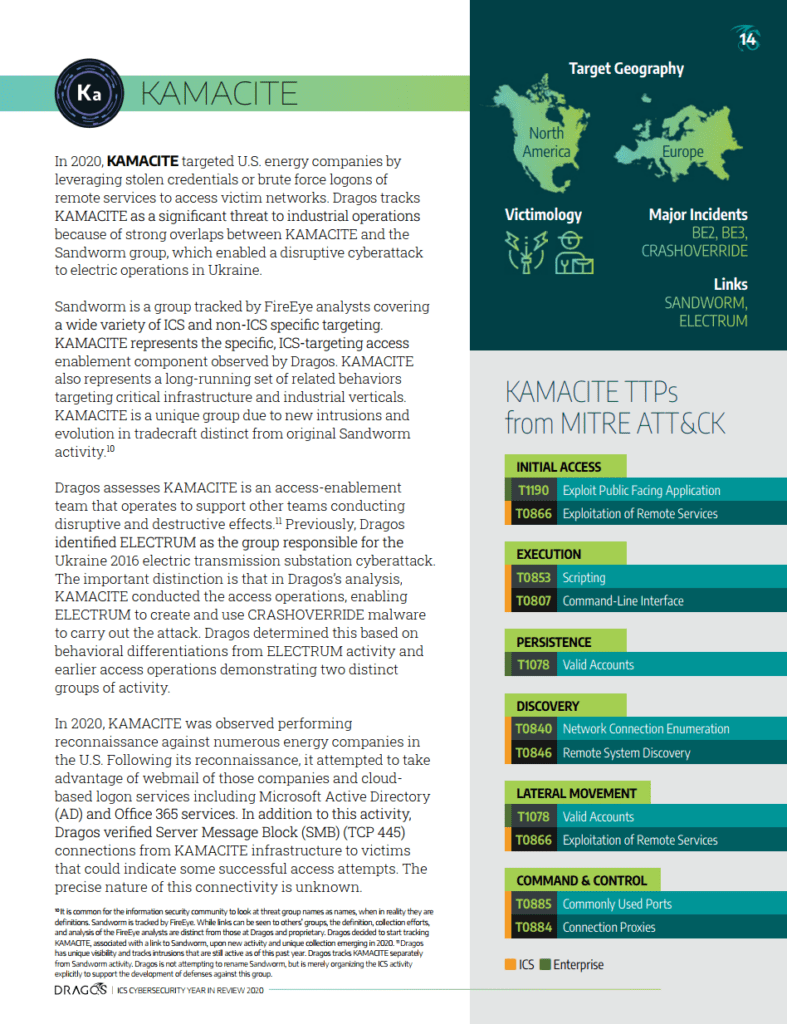
The new KAMACITE activity group represents a long-running set of related behaviors targeting electric utilities, oil and gas operations, and various manufacturing since at least 2014. The group facilitated Industrial Control System (ICS)-specific operations including the BLACKENERGY2 campaign and the 2015 and 2016 Ukraine power events. KAMACITE represents a distinct set of tools, targets, and behaviors to gain and maintain long-term access within ICS networks. While the group has evolved over time, many aspects of its operations and tradecraft have remained remarkably similar over the past six years. The group is responsible for enabling other entities – such as ELECTRUM – to deliver ICS-specific attacks, even though KAMACITE has not directly caused an ICS disruptive event.
KAMACITE typically transfers operational control to other entities (such as ELECTRUM in the 2016 Ukraine event, and some unknown entity in the 2015 Ukraine event) to execute ICS disruptive effects while maintaining long-term access. The group has demonstrated understanding and operational ability within ICS networks since the early 2010s and is a major concern for asset owners and operators.
KAMACITE almost exclusively leverages compromised third-party servers for network infrastructure. Network infrastructure and communication frequently only reference server Internet Protocol (IP) addresses with rare use of domains. KAMACITE-specific activity frequently takes over servers used for other purposes for communications. This includes Tor nodes and relays, and Virtual Private Server (VPS) instances associated with criminal operations. This pattern of behavior persists from BLACKENERGY2 Command and Control (C2) infrastructure, both Ukraine events, and recent intrusion attempts against the United States (U.S.) energy sector and government entities.
The group utilizes a combination of phishing with malicious attachments and external access via legitimate services (e.g., replaying captured credentials) to gain initial access to victim organizations. Historical phishing activity is associated with delivery or follow-on download of custom malware frameworks such as BLACKENERGY2, BLACKENERGY3, and GREYENERGY. Examples of phishing lures used by KAMACITE include Ukrainian political and financial themes and technical conference content.
Based on observed capabilities and malware, Dragos assesses with moderate confidence that KAMACITE leverages initial access to victim networks to capture credentials using publicly available tools such as Mimikatz. This can be used via built-in system tools or common administration frameworks (such as PSExec) for remote access and code execution. This appears to be the case for intrusions such as the Ukraine power incidents in 2015 and 2016 and aligns with emphasis on credential capture and reuse in more recent KAMACITE operations against U.S. energy companies.
KAMACITE operations are linked to potentially five major ICS cybersecurity events, two of which resulted in disruption. Although leading to a disruptive event, Dragos assesses with high confidence that another entity is responsible for actual ICS operations in some cases. KAMACITE has proven to at least facilitate operations leading to physical disruption.
Events linked to KAMACITE include:
- 2014 BLACKENERGY2 Events: Intrusions targeted industrial entities in the U.S. and Europe. Although linked to an earlier crimeware variant, BLACKENERGY2 featured plugins with ICS-specific functionality for system enumeration and information collection.
- 2015 Ukraine Power Event: KAMACITE facilitated intrusion via phishing and delivery of BLACKENERGY3 malware. This allowed network enumeration and follow-on penetration of control system environments that enabled disruption.
- 2016 Ukraine Power Event: KAMACITE facilitated intrusion and transition of operations to ELECTRUM after penetrating the ICS environment, leading to delivery and execution of CRASHOVERRIDE malware.
- 2017 German Electric Sector Intrusions: While details on this event remain limited, multiple sources have described a campaign of intrusions targeting electric sector entities in Germany with behaviors matching KAMACITE characteristics.
- 2019-2020 U.S. Energy Sector Intrusions: A persistent campaign was linked to KAMACITE behaviors against multiple U.S. energy companies – including possible electric utilities – in mid-2020.
Based on these events, KAMACITE is at minimum a Stage 2 ICS access enabling entity as defined by the ICS Cyber Kill Chain and is associated with multiple ICS attacks resulting in physical disruption.
KAMACITE aims to penetrate control system environments to enable ICS-specific disruptive events. While Dragos assesses that the group transitions access to follow-on teams with ICS-specific capabilities (e.g., enabling ELECTRUM to execute CRASHOVERRIDE in the 2016 Ukraine event), KAMACITE operations are vital for the success of these engagements. Based on all available evidence, KAMACITE activity is associated with preparations for immediate execution of ICS-specific attacks.
KAMACITE relies on a combination of custom malware, open source tools, and native system commands with distinct network communication patterns to operate in IT and ICS environments. While individual KAMACITE-related events and campaigns feature specific details, the below observations capture general KAMACITE behaviors since 2014.
Host
- From 2014 through 2018, KAMACITE activity was associated with evolving malware variants. It began with the “Energy” series (BLACKENERGY2, BLACKENERGY3, and GREYENERGY), then the EXARAMEL family (CRASHOVERRIDE and EXARAMEL). In addition to technical and code overlaps among these items, execution and installation relied on similar features such as ability to execute unknown, unsigned software in victim environments. Applying limiting application execution to prevent execution or monitoring for new, unsigned binaries entering into sensitive environments, such as control system networks, can defend against unknown malware variants exhibiting similar characteristics.
- KAMACITE behavior frequently leverages continuous credential theft and reuse to enable operations, including lateral movement in compromised networks and initial remote access to victims. KAMACITE now relies on this technique more than in the past, making it an important item for mitigation or detection. Defensive recommendations include implementing and enforcing robust Multi-Factor Authentication (MFA), especially for external or remote access logons, and disabling or prohibiting local administrator accounts wherever possible to minimize the impact of stolen credentials as part of an intrusion. Organizations must log and analyze remote access and similar activity and look for suspicious patterns of behavior to identify lateral movement or other activity.
Network
- Some KAMACITE credential capture activity is associated with adversary-registered domains, network Command and Control (C2) in the group’s operations almost always rely on direct communication to IP addresses. Identifying communication to an IP address without a corresponding Domain Name System (DNS) lookup (associated with resolving a domain to the server) can identify this type of activity. It may also result in significant false positives depending on the environment, so this alerting must be tested and evaluated within specific environments prior to deployment.
- KAMACITE specifically and Sandworm more generally use compromised third-party infrastructure for most communication directed to victims, either as C2 addresses or infrastructure from which remote logons are launched. Some of these items also overlap with criminal networks and Tor relay nodes. Limiting or blocking communication to these items may reduce attack surface. Since the group’s infrastructure may overlap with legitimate services, organizations and defenders must ensure they appropriately flag and document any alerts or blocks so traffic is viewed in proper context of likely KAMACITE malicious activity.
Control System Networks
- KAMACITE relies on captured credentials or subverted network controls to access control system networks from general IT. MFA implementation and separate credential schemas for VPN and control system logons can increase the difficulty of credential replay attacks. Analyzing and tracking remote logon activity against known good patterns of behavior can identify anomalous or potentially malicious activity with respect to control system network access.
- The group is associated with use and deployment of custom, simple port scanners for network and service enumeration. This behavior was observed in GREYENERGY campaigns and in events leading up to the operational handover to ELECTRUM in CRASHOVERRIDE. Identifying rogue or unknown network scanners in control system environments can identify behavior like that exhibited by KAMACITE for Stage 2 survey and reconnaissance operations.
Dragos Platform
- Detections for all KAMACITE behaviors are available in the Dragos Platform.
KAMACITE is one of the few activity groups tracked by Dragos that has either directly caused (possibly the 2015 Ukraine power event) or enabled (the 2016 Ukraine power event) a disruptive ICS incident. Operating primarily through Stage 1 and initial portions of Stage 2 of the ICS Cyber Kill Chain, KAMACITE activity is more directly observed than ICS-specific entities (such as ELECTRUM) given the group’s prolific behavior in initial IT-targeting operations. Based on this behavior, Dragos tracked continued KAMACITE activity across multiple regions – including Western Europe and the U.S. – from 2017 to the present. While Dragos cannot connect KAMACITE to any known disruptive event since the 2016 Ukraine event, the group remains active.
Ready to put your insights into action?
Take the next steps and contact our team today.