Dragos currently tracks more than 3000 CVEs (Common Vulnerabilities and Exposures) that affect industrial control systems (ICS) and operational technology (OT) networks. Of these CVEs, more than 400 have at least one publicly available exploit and some have multiple public exploits. In this blog, we explain what a public exploit is, how to determine its impact on your ICS/OT networks, and how to approach remediation of known vulnerabilities with publicly available exploits.
What Is a Public ICS/OT Exploit?
An exploit is a tool that allows an adversary to bypass a security boundary within a piece of software or hardware. Exploits come in many forms. It could be a curl command, a URI, a blob of HTTP data, or even a reasonably written description. Dragos considers anything that allows a low-skilled adversary to knowingly and quickly bypass a security boundary to be an exploit.
While our interpretation of what constitutes an exploit is fairly liberal, the exploits in Dragos’s data set are typically represented in code. An exploit is considered “public” when it is freely available to anyone. For example, exploits posted to Exploit Database (Exploit-DB) are considered public because there are no restrictions to accessing Exploit-DB. Generally speaking, an exploit is treated as public if it is accessible by simply visiting a link. An exploit is considered ICS/OT related when it can reasonably be determined to affect a system within an ICS/OT network.
Public exploits significantly lower the skill and effort needed to exploit a software or hardware vulnerability. The public exploits tracked by Dragos affect every level of an Industrial environment as described in the Purdue Model. They provide adversaries with pre-packaged tools that are capable of infiltrating and spreading through an ICS/OT network. Adversarial usage of public exploits on ICS/OT networks is not theoretical. Dragos tracks multiple Activity Groups (AG) that use public exploits.
The public ICS/OT exploits that Dragos tracks have been developed by hundreds of individuals. They affect products developed by more than a hundred vendors and their impact on the industrial process runs the gamut. ICS/OT public exploits can be found in a virtual private network (VPN) appliance for example, or in remote desktop software, as is the case with the Oldsmar, FL Water Treatment Facility. While VPN appliances and remote desktop solutions are not ICS specific, it is reasonable to describe these systems as ICS/OT related. Perhaps even more controversial is how to handle Microsoft Windows Operating System (Windows OS) exploits.
ICS/OT Public Exploit Trends
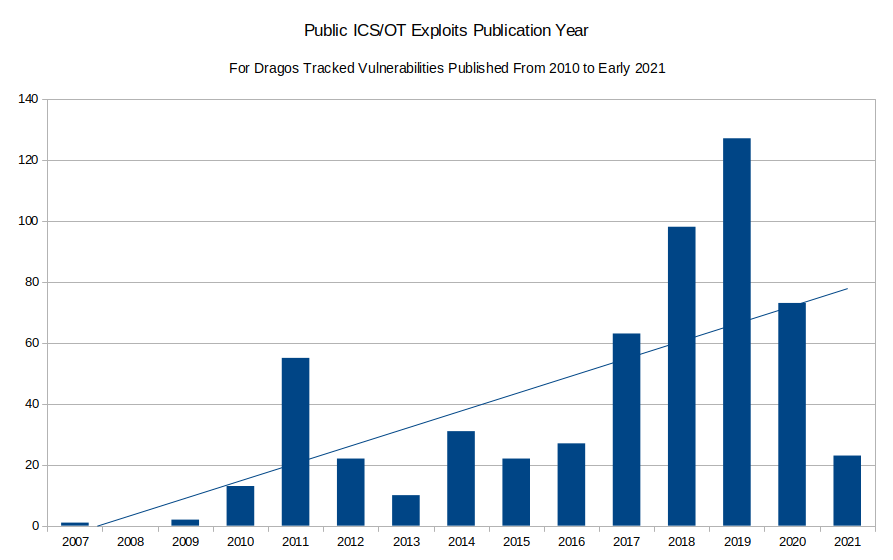
CVE publication has been on a general upward trend over the last two decades and each of the last four years have set new records for CVEs published. A very similar trend is observed over the last decade of public ICS/OT exploits, as shown in Figure 1 below.
Public Exploits Viewed Through the Purdue Model
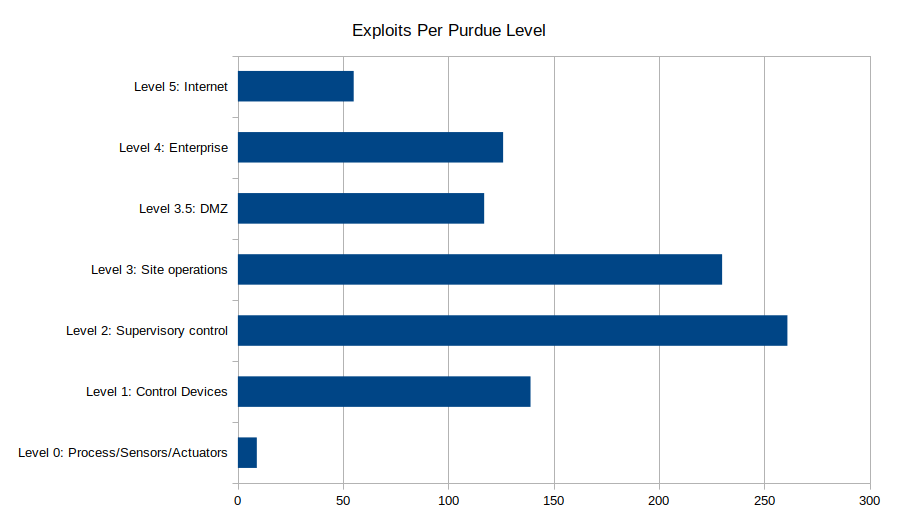
When discussing ICS/OT exploits, it is important to understand the potential impact the exploit might have on the industrial process. For this, we rely on the Purdue Model. In Figure 2, the public ICS/OT exploits are mapped to the Purdue Level of the affected software/device. This figure shows that the majority of these public exploits map within the ICS network (Levels 1, 2, and 3).
Key Findings for Better Vulnerability Remediation
Dragos’s white paper, Examining ICS/OT Exploits: Findings From More Than a Decade of Data, which is a companion reference to this blog, provides more details on the impact of public exploits at different levels of the Purdue Model and the vendors who are most impacted by these exploits. This research covers the last ten years of ICS/OT public exploit activity. Leveraging the knowledge of these exploits and guidance in the white paper will enable ICS operators to better remediate ICS/OT vulnerabilities.
The white paper answers some key questions about the findings, including:
- What well-known organizations publish nearly 25% of all public exploits?
- Why did the total amount of ICS/OT exploits and the percentage of ICS/OT CVEs with a public exploit decrease in 2020?
- Why is the ability to pivot and persist within an ICS/OT network the most common impact of a public ICS/OT exploit?
- What ICS/OT public exploits are potentially useless within the context of an ICS/OT network?
- Based on the known public ICS/OT exploits, what vulnerabilities should be remediated first?

Ready to put your insights into action?
Take the next steps and contact our team today.