Dragos’ Threat Intelligence team recently released two 2018 Year in Review reports discussing the major findings and trends our analysts and threat hunters identified throughout the year.
Our full reports provide in-depth looks at the vulnerability trends, threat landscape, and defensive recommendations for industrial control system (ICS) asset owners and operators.
Key Takeaways from Threat Intelligence & Vulnerabilities
- The amount of activity targeting ICS increased this year, and we identified three new activity groups targeting ICS: ALLANITE, XENOTIME, and RASPITE. This brings the total number of ICS-targeting threat activity groups to eight.
- Dragos identified four major elements contributed significantly to greater risk: (1) more numerous intrusions into ICS networks enabling research and reconnaissance of ICS operations and technology; (2) commodity malware and wormable ransomware causing ICS infections; (3) infrastructure-targeting activity groups adopting Living off the Land tactics and behaviors that bypass traditional security protection mechanisms; and (4) the compromise of several industrial control equipment manufacturers enabling potential supply-chain threats and vendor-enabled access to ICS networks.
- Dragos did not identify new malware with life-threatening or ICS-specific destructive capabilities, but we anticipate continued risk of operational losses due to either incidental malware infections in ICS environments, or as the result of mishaps during initial intrusion and reconnaissance operations within the operational technology (OT) realm.
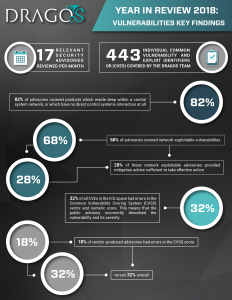
- Dragos tracked 204 public vulnerability advisories impacting ICS. A majority of these covered products residing deep in a control system network, with no direct control systems interaction.
- Public advisories had a high percentage of errors in the descriptions of vulnerabilities and their severity. 32% of all CVEs in the ICS space had errors in the Common Vulnerability Scoring System (CVSS) vector and numeric score.
 |  |
| Download the Key Findings Activity Groups Infographic | Download the Key Findings Vulnerabilities Infographic |
Threats in Brief
IT-focused malware is not new or unique, and we anticipate commodity malware infections will be prevalent for years to come due to ease of use, effectiveness within the enterprise, and the publicly-available nature of commodity malware. Malware – including worms like WannaCry – with the potential to bridge the IT/OT gap are an ongoing threat due to ICS environments being unable or unwilling to update machines due to poor patch management, downtime sensitivity, or system end-of-life considerations
Third-party access to OT networks is a common and necessary component of modern operations but introduces risk as compromises along the supply chain can move from vendors’ networks to the asset operator’s network. Most concerning to Dragos are several compromises of ICS vendors and manufacturers in 2018 by activity associated with XENOTIME, providing potential supply chain threat opportunities and vendor-enabled access to asset owner and operator ICS networks.
Adversaries are moving away from unique malware and vulnerabilities for the majority of operations, which is concerning because many OT security practices rely on anti-virus and vulnerability-based protection schemes to reduce risk. Thus, their fundamental behavior becomes a key detection element for defense.
Vulnerability disclosures and advisories are dangerously providing erroneous information which is relied upon by asset owners and operators to make risk decisions – this bad data makes those decisions ineffective. Dragos identified one-third of public advisories with Common Vulnerability and Exploit identifiers (CVEs) had errors describing and rating the severity of the vulnerability. However, Dragos did identify an increase in vendors self-reporting vulnerabilities and researchers engaging with vendors directly, which produced more accurate advisories; only 18% of vendor-produced advisories had scoring errors.
Applying Threat Intelligence
ICS-specific threat intelligence can help organizations lower their risk profiles and proactively protect against common and emerging techniques. Implementing analytics and defensive recommendations as well as vulnerability insights gleaned from WorldView reporting helps defenders adopt a “Whole of Kill Chain” approach, identifying adversary behaviors from the initial intrusion to second-stage impacts.
In 2019, Dragos expects to identify more activity groups targeting ICS, both due to greater visibility into the OT networks and better identification of adversary behavior driven by ICS threat intelligence. Dragos will continue our efforts to bring ICS cybersecurity intelligence and resources to all levels of the enterprise and community and collaborate across sectors to help fuel a greater understanding of the threats ICS industries face, and how to defend against them.
To view all Year in Review reports, go here: https://www.dragos.com/year-in-review/
Ready to put your insights into action?
Take the next steps and contact our team today.