In a predictable yet concerning trend, ransomware groups continued to impact industrial entities and critical infrastructure during the third quarter of 2023, leading to disruptions in operations. Although there has been a marginal decrease in the reported ransomware incidents compared to the previous quarter, the ramifications remain profound. Not only do they harm the impacted industrial entities, but they also affect related sectors and affiliated companies. Moreover, even when operational technology (OT) systems aren’t the primary objective, ransomware breaches into enterprise IT infrastructures, upon which OT systems depend, can adversely affect OT operations.
Ransomware Operation Impacts
Dragos previously assessed that the third quarter of 2023 would see increased business-impacting ransomware attacks against industrial organizations.1 This assessment was validated as the subsequent ransomware incidents exhibited more severe impacts than in the first or second quarters of 2023. A prime illustration of ransomware’s far-reaching impact was the Lockbit attack that occurred in July 2023 against the Port of Nagoya’s Unified Terminal System.
The Port of Nagoya, which handles almost 10% of Japan’s trade volume, experienced a significant disruption, bringing container operations across all its terminals to a standstill for several days. This caused considerable operational delays and sent economic shockwaves throughout Japan’s complex supply chain. Like many ransomware attacks, cascading downstream impacts were significant, including Toyota Motor Corporation shutting down operations at a packaging line that exports various products.2
In addition, Dragos’s ransomware analysis revealed other incidents that impacted the operations of multiple organizations, such as the following:
- Johnson Controls International and its subsidiaries’ operations.
- Norwegian recycling giant Tomra.
- Trucking and fleet management solutions provider ORBCOMM.
- the Russian medical laboratory Helix.
MOVEit Zero-Day Vulnerability
Zero-day vulnerabilities and known, unpatched vulnerabilities are among the recent techniques ransomware groups heavily relied on in the third quarter of 2023. Dragos observed a 340% increase in Cl0p ransomware victims compared to the previous quarter. This is potentially due to the MOVEit zero-day vulnerability, which was used in Cl0p operations. According to security blogs, the Cl0p ransomware group is expected to earn $75-100 million from extorting victims in their massive MOVEit data theft campaign. Dragos assesses with moderate confidence that ransomware groups, like Cl0p, will continue to prioritize zero-day vulnerabilities in their operations, given the lucrative experiences of ransomware groups in the third quarter of 2023.
Ransomware Trends, Patterns & Observations
The Dragos ransomware analysis evaluated variants used against industrial organizations worldwide and tracks ransomware information via public reports and information uploaded or appearing on the dark web. By their very nature, these sources report victims that were listed as targets and those that pay or otherwise “cooperate” with the criminals, and they do not necessarily match one-to-one with all incidents that took place in this last quarter.
Two interesting observations from the third quarter of 2023 compared to the previous quarters were observable decreases in active ransomware groups and ransomware incidents impacting industrial organizations. Specifically, of the 72 ransomware groups that have historically attacked industrial organizations and infrastructure, only 30 of the groups were active, and the number of ransomware incidents was 231 compared to 253 in the second quarter of 2023. As of this blog, Dragos is uncertain about the reason for the decrease in ransomware incidents between the second and third quarters of 2023.
Although the number of ransomware incidents in the third quarter of 2023 was slightly less than in the second quarter of 2023, the overall impact of these ransomware attacks against industrial organizations remains significant.
Regional Impact Observations, Third Quarter 2023
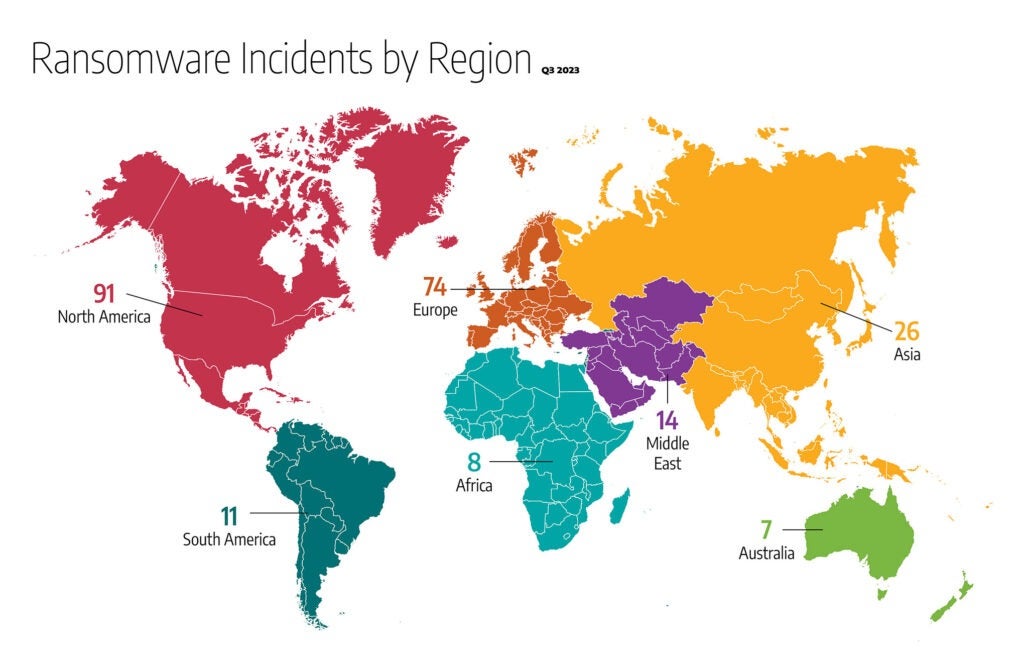
- 91 ransomware incidents impacted industrial organizations and infrastructure in North America. This figure represents roughly 39.4 percent of the observed 231 global ransomware attacks. This was a 25 percent decrease compared to Q2 of 2023. Within North America, the U.S. received over 37 percent of all ransomware incidents, compared to 43 percent last quarter.
- Approximately 32 percent of global ransomware incidents (74 in total) impacted Europe, roughly the same as observed in Q2 of 2023. (30.5 percent and 77 incidents).
- Asia is next with 11.3 percent, or 26 incidents.
- The Middle East region saw an increase in the number of incidents in the third quarter of 2023 compared to the previous quarter – 6 percent (14 incidents) and 3 percent (8 incidents), respectively.
- South America had 4.8 percent, totaling 11 incidents.
- Africa had 3.5 percent, totaling eight incidents.
- Australia also saw an increase in observed ransomware incidents, with 3 percent or seven incidents, compared to 1 percent or three incidents last quarter.
Industry Impacts, Third Quarter 2023
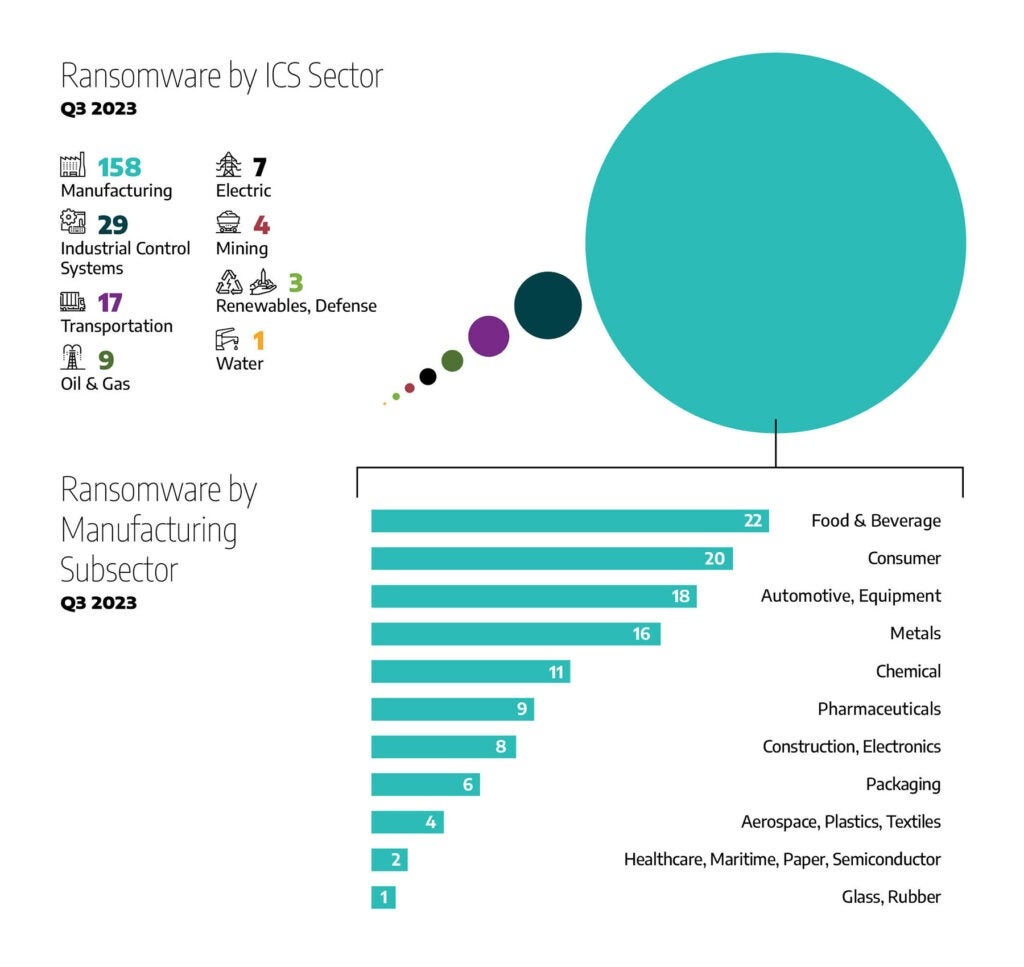
The most impacted industry during the third quarter of 2023 was manufacturing with 158 observed incidents in total, or 68.4 percent. The breakdown by sector is as follows.
- The next most impacted industry was companies that engineer and create industrial control systems (ICS) equipment (29 observed incidents, or 12.6 percent).
- The transportation sector was impacted 17 times , for a total of 7.4 percent of all observed incidents.
- The oil and natural gas sector had 3.9 percent of alleged attacks (9 incidents).
- The electric sector was impacted by three percent of the alleged attacks (7 incidents).
- The mining sector was impacted by 1.7 percent of the incidents (4 incidents).
- The renewable energy, defense, and water sectors each had one percent of the global alleged attacks each.
In addition to the primary industries and sectors mentioned above, Dragos observed 19 unique manufacturing sub-sectors that were impacted by ransomware during the third quarter of 2023.
- Food and beverage: 22 incidents (14 percent)
- Consumer: 20 incidents (13 percent)
- Automotive and Equipment: 18 incidents (11.4 percent)
- Metals: 16 incidents (10 percent)
- Chemical: 11 incidents (7 percent)
- Pharmaceuticals: 9 incidents (5.7 percent)
- Electronic: 8 incidents (5 percent)
- Packaging: 6 incidents (3.8 percent)
- Aerospace, Plastics, and Textile: 4 incidents (2.5 percent)
- Healthcare, Maritime, Paper, and Semiconductor: 2 incidents (1 percent)
- Glass and Rubber: 1 incident (less than 1 percent)
Ransomware Groups Trends, Patterns, and Observations – Third Quarter of 2023
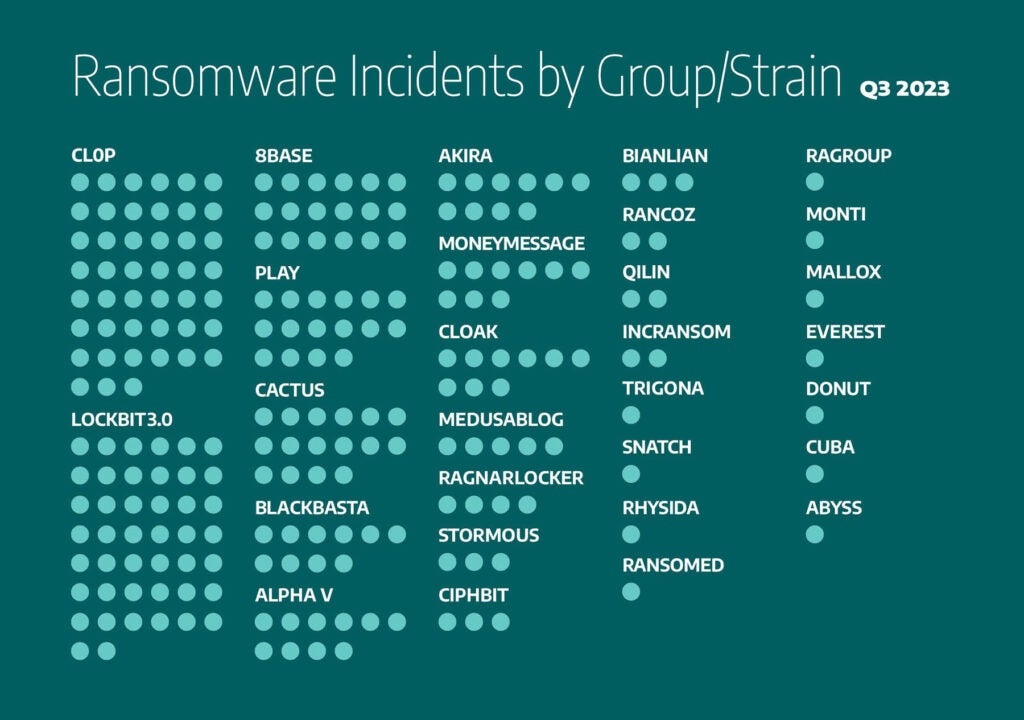
Dragos’s analysis of ransomware data from the third quarter of 2023 indicates that the Cl0p ransomware group was behind the most attacks against industrial organizations with 19.5 percent (45 incidents) of observed ransomware events The Lockbit 3.0 ransomware was the second most-used with 19 percent (44 incidents). The following rounds out the observed ransomware group trends for the third quarter of 2023:
- 8base was responsible for 7.8 percent of incidents (18 incidents)
- Play and Cactus: 6.9 percent of incidents each (16 incidents each)
- Blackbasta, AlphaV, and Akira: 4.3 percent each (10 incidents each)
- Noescape, Moneymessage, and Cloak: 3.9 percent each (9 incidents each)
- Medusablog: 2.2 percent (5 incidents)
- Ragnarlocker: 1.7 percent (4 incidents)
- Stormous, Ciphbit, and Bianlian: 1.3 percent (3 incidents each)
- Rancoz, Qilin, and Incransom: (0.9 percent each (2 incidents each)
The remaining ransomware groups were responsible for one percent of incidents or less.
The groups that Dragos observed in the second quarter but not in the third quarter of 2023 are Royal, Blackbyte, Unsafe, Dunghill Leak, Black Suit, Vice Society, Ransome House, and Nokoyawa. Dragos observed the following ransomware groups for the first time in the third quarter of this year: Cactus, Incransom, and Ransomed. It is still being determined if these new groups are new or reformed from other groups.
Ransomware Victimology Trends, Patterns, and Observations – Third Quarter of 2023
Interestingly, Dragos observed various ransomware groups appearing to only be used against specific industries and regions in the third quarter of 2023. Although these findings are interesting, they do not necessarily suggest that ransomware groups are focused on specific organizations or industries because victimology often changes, and a vast majority of ransomware operations are opportunistic.
The following victimology trends were observed in the third quarter of 2023:
- The Moneymessage ransomware group has only been observed attacking defense sector organizations.
- Rancoz and Akira ransomware groups appear to only attack entities in the United States.
- Ransomware groups Qilin, Incransom, Ciphbit, and Blackbasta have only been observed targeting the manufacturing sector.
- Cybercriminals seem to primarily leverage Play ransomware against entities in the US and Europe.
- Metaencryptor has only been observed being used against the European manufacturing sector.
- Cactus, AlphaV, and Bianlian ransomware groups have only impacted manufacturing and ICS equipment and engineering sectors.
The above observations are informed through ransomware group listings, which the ransomware group itself mainly self-identifies. There may exist other impacted regions or industries by these groups. However, Dragos is basing these trends on the groups’ own reported postings.
In Conclusion
Although the overall number of ransomware incidents was less than the last quarter of 2023, the impact remains high for affected organizations. Dragos assesses with high confidence that in Q4 of 2023, ransomware will continue to opportunistically attack industrial organizations, which will have varying operational disruptions. However, direct impacts to OT networks and processes will largely depend on the victim organization’s architecture and whether their OT systems are properly segmented or if the network architecture is flat and can be easily enumerated and traversed. Lastly, Dragos assesses with moderate confidence that new ransomware variants will pop up in the coming quarters and ransomware groups will likely continue to prioritize zero-day vulnerabilities in their attack operations.
Get free sample reports of Dragos WorldView to see more of the types of OT threat intelligence we provide. 
References
Ready to put your insights into action?
Take the next steps and contact our team today.

