In 2021, the industrial community attracted high-profile attention. Major cybersecurity incidents struck industrial organizations in a range of sectors, with international headlines detailing everything from a compromise of a water treatment facility with the intent to poison its community to a ransomware attack against a pipeline operator that disrupted gas supplies to the southeastern United States.
These reports underscored the potentially devastating outcomes a security breach of critical infrastructure could have on communities and a country’s economy. They also elevated the discussion the ICS/OT community has been having for years on cyber readiness and brought them to the proverbial kitchen table—and the policymakers’ and regulators’ office desks, too.
With the 2021 Dragos Year in Review, Dragos hopes to provide industrial organizations with meaningful insights that help them more fully understand the cyber risks surrounding their most important assets—their ICS/OT environments. The 2021 Year In Review shares data-driven insights that add context to the sensational stories and evidence from the field of how industrial organizations are progressing in their cybersecurity readiness and where they need to continue their work to provide safe and reliable operations into 2022 and beyond.
New Activity Groups Discovered
Dragos discovered three new activity groups with the assessed motivation of targeting ICS/OT. Two of the groups have achieved Stage 2 of the ICS Cyber Kill Chain showing their ability to get access directly to ICS/OT networks.
KOSTOVITE
- In March 2021 when KOSTOVITE compromised the perimeter of an energy operation and maintenance provider network, it exploited a zero-day vulnerability in the popular remote access solution, Ivanti Connect Secure. KOSTIVITE used dedicated operational relay infrastructure against this target to obfuscate the origin of its activities, then stole and used legitimate account credentials for its intrusion.
PETROVITE
- PETROVITE targets mining and energy operations in Kazakhstan. One targeted group has 16 business units that focus on mining and power generation throughout Kazakhstan. Dragos is aware of targeted operations that started during the third quarter of 2019 and have intermittently continued throughout 2021.
ERYTHRITE
- ERYTHRITE is an activity group that broadly targets organizations in the U.S. and Canada with ongoing, iterative malware campaigns. Dragos has observed ERYTHRITE compromising the OT environments of a Fortune 500 company and the IT networks of a large electrical utility, food and beverage companies, auto manufacturers, IT service providers, and multiple Oil and Natural Gas (ONG) service firms.
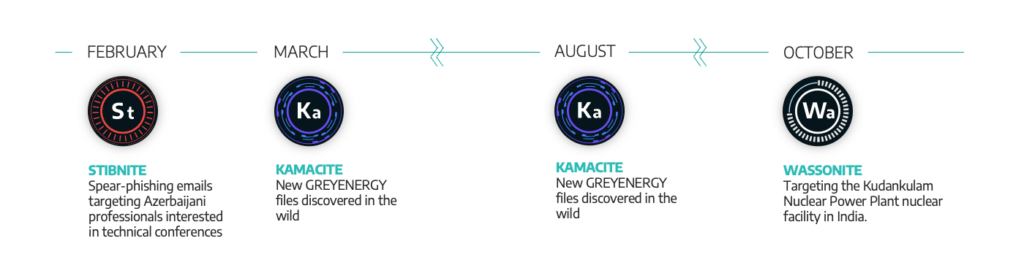
Activity Group Updates
Dragos discovered new cyber threat activity across the following known Activity Groups targeting ICS/OT industrial networks.
State of ICS/OT Vulnerabilities
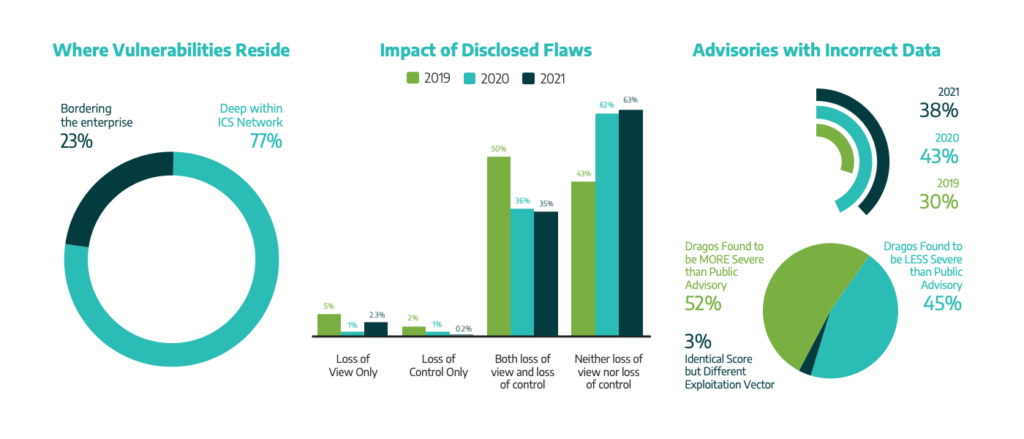
In 2021, the number of reported ICS vulnerabilities continued to increase, which coincided with an increase in vendors providing patches for disclosed flaws in advisories.
Dragos researchers analyzed 1703 ICS/OT common vulnerabilities and exposures (CVEs) during 2021, which is more than twice as many as last year. For each CVE, Dragos independently assesses, confirms, and often corrects the advisories and describes any flaws in firmware or software.
Taking Action on ICS/OT Vulnerabilities
Dragos works with the community to help vendors provide more accurate, actionable, and easier-to-track advisories. In 2021, we significantly enhanced the vulnerability management features offered to customers through the Dragos Platform.
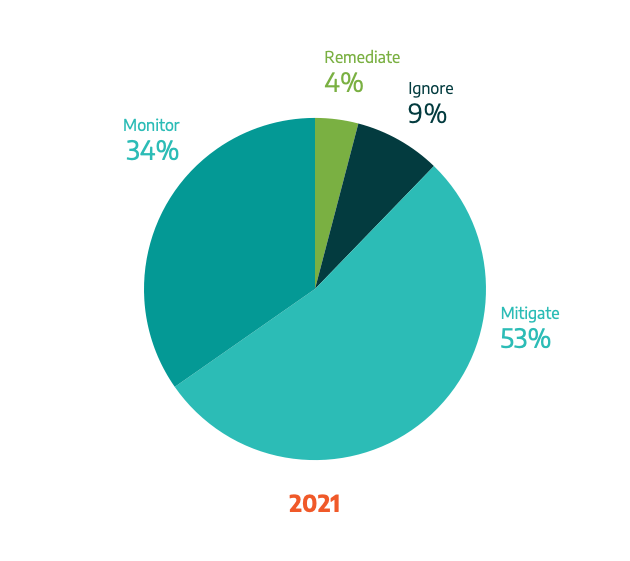
Dragos assesses vulnerabilities in our WorldView Intelligence reports and in the Dragos Platform and categorizes them by threat levels: Immediate Action, Limited Threat, Possible Threat, No Action, and Hype. Dragos also recommends four different responses to those threats: Remediate, Mitigate, Monitor, or Ignore.
The following summarizes our analysis of how to respond to vulnerabilities seen in 2021.
Industrial Risk to Ransomware
Ransomware became the number one attack vector in the industrial sector.
- Dragos assessed that manufacturing accounted for 65% of all ransomware attacks.
- Two ransomware groups, Conti and Lockbit 2.0, caused 51 percent of attacks—with 70% of their malicious activity targeting manufacturing.
Ransomware Incidents by Group/Strain

Lessons Learned from Dragos Customer Engagements
Following are four key findings discovered from customer service engagements in the past year:
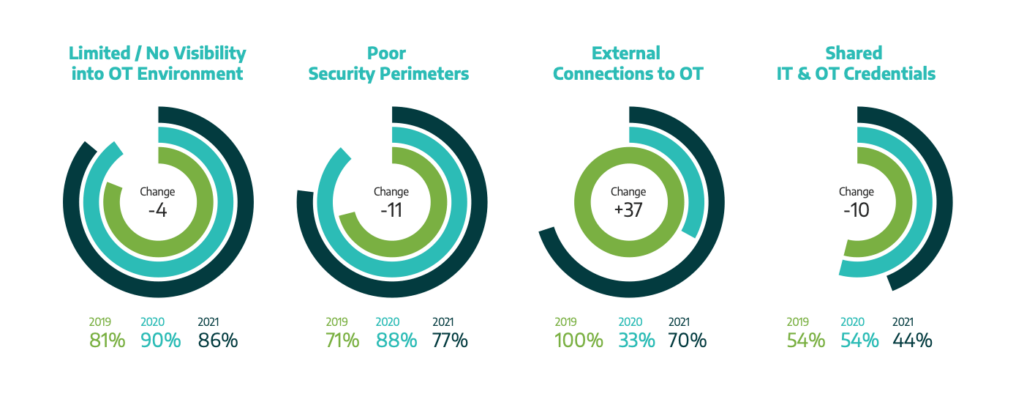
- 86% of service engagements have a lack of visibility across OT networks—making detections, triage, and response incredibly difficult at scale.
- 77% of service engagements included a finding about improper network segmentation.
- 70% of service engagements included a finding of external connections from OEMs, IT networks, or the Internet to the OT network.
- 44% of service engagements included a finding about shared credentials in OT systems, the most common method of lateral movement & privilege escalation.
See Our Data Compared to Previous Years
Prepare your enterprise with the data-driven analysis from the Dragos 2021 ICS/OT Cybersecurity Year In Review, including the security controls you need to have a world-class OT cybersecurity program in 2022.

Ready to put your insights into action?
Take the next steps and contact our team today.