For this year’s SANS Industrial Control System (ICS) Summit in June 2022, the SANS Institute and Dragos again partnered to develop an industrial-focused Capture The Flag (CTF) competition. The Dragos team used their extensive experience to create a a series of challenges that the ICS community can benefit from, ranging from beginner to advanced difficulty to allow all experience levels to participate.
Given the Transportation Security Administration (TSA) has implemented a series of security directives to help secure oil and gas environments from external cyber threats, Dragos developed a CTF backstory that exemplifies an ICS attack kill chain against an oil and gas environment using common and advanced Tactics, Techniques, and Procedures (TTPs).
Getting Started: A Realistic Security Scenario
ACME Fuel operates one of the largest pipelines on the West coast, supporting millions of consumers. Their largest pipeline runs from northern Alberta, through the Rockies, down to Washington, into Oregon, and finally, California, where it terminates north of San Francisco at the San Pablo Bay port where their liquid natural gas (LNG) facility ships millions of tons of gas per year to countries across the world.
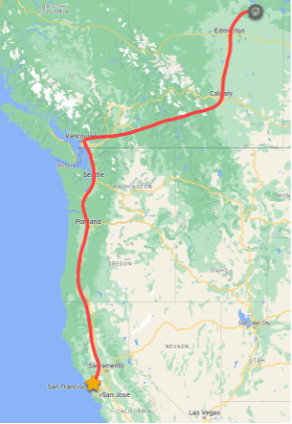
The consumer demand for natural gas has ebbs and flows like any service, but one key time of the year where demand is essential is during the holiday season. With the San Pablo Bay LNG facility running near capacity over Christmas, and with many asset owners and operators taking some much-needed time off; a perfect storm was brewing. Industrial adversaries are well aware of consumer demand based on weather patterns and calendar events. As cowardly as it is, this is when they often launch an attack campaign.
The attack campaign consisted of both physical and logical paths to afflict maximum damage to ACME Fuel’s industrial process. Using information gathered from extensive open-source intelligence (OSINT), the adversaries targeted a handful of corporate users via sophisticated phishing campaigns, masking as internal technical support, looking to update ad-hoc critical Windows patches. Additionally, they modified a number of universal serial bus (USB) devices with a wormable trojan designed to ransom industrial workstations, locking specific directories needed to perform day-to-day operations.
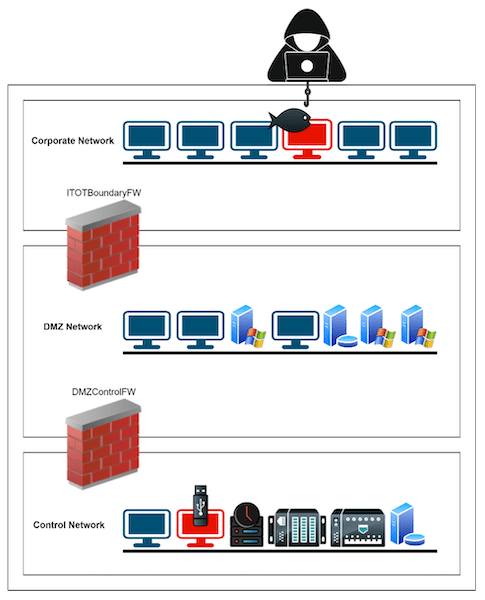
The technique of using logical and physical avenues to attack ACME Fuel allowed the adversaries to ransom assets from top-down and bottom-up, inflicting maximum damage across all levels of the Purdue Model. One thing they didn’t spend much time focusing on was covering their attack path, they came in hard looking to disrupt the process and ultimately make Christmas miserable for millions of customers and consumers.
Setting the Stage: Modeling Real-World Threats
The Dragos team aimed to build their CTF challenges to reflect real-world adversarial campaigns, leveraging common and advanced TTPs used to gain access to the environment’s Crown Jewels. To ensure this was accomplished, the Dragos team split their CTF challenges into the following categories:
Ransomware Analysis
A handful of flags reflect the ransomware attack leveraged by the adversary to lock up ACME Fuel’s ICS environment. CTF participants needed to leverage their cryptography knowledge to decrypt files using artifacts left behind by the adversary to gain back control of their systems.
ICS Protocol PCAP Analysis
The CTF included common Oil and Gas ICS protocols found within the ACME network. Participants needed to understand how the ICS protocol normally operates within an ICS environment. Using this understanding participants found flags associated with adversary activities within the network captures.
ICS Windows Event Log Analysis
There were a number of questions that challenged participants to analyze windows events logs to find flags. The participants had to use log analysis techniques to find the adversary behavior and isolate what had happened.
Memory Image Forensic Analysis
Questions within the CTF used memory images to challenge participants to understand what the adversary had done to critical ICS systems. Memory forensics is often used within an ICS incident response to understand at a detailed level what is happening to the system.
Engineering & Network Diagram Analysis
The CTF included architecture-level analysis of network and engineering diagrams. These questions challenged the participants to analyze these diagrams to answer conceptual-level questions around security solutions and traffic flows.
Game On: Developing Skills At All Levels
The SANS ICS Summit CTF was developed with a wide range of competitors in mind. With over 700 players participating, the CTF challenges needed to be created to allow each individual or team to learn new TTPs, increasing their offensive knowledge. While each CTF competition will crown leaderboard winners (top players received custom SANS/Dragos coins), each player that worked through the challenges, whether it be level 1, 2, 3, or 4, learned new skills that could be applied to their profession.
We’re happy to say we had some satisfied attendees!
“Very nice Event – learned a lot and had even more fun.” – BF
“…Thank goodness for SANS. This is always the best free training anywhere” – Dan
“Yeah, it’s a lot of fun, it’s been great, thanks for putting on the CTF” – Fable
In Conclusion
The goal of this year’s SANS ICS Summit CTF was to provide a fun competitive learning experience to the participants within the oil and gas theme. Both, SANS and Dragos accomplished this by providing four levels of play that saw over 1000 community members registered, with over 700 of them actively participating. Participants from all over the world and at all skill levels took part.
The top players and teams competed for prizes and most importantly bragging rights. While the newer members of the community were exposed to ICS security and gained important skills, all of the CTF participants were challenged and came away with a better understanding of the skills needed to protect civilization.
What’s Next? Dragos DISC CTF Coming in November
Looking for more CTF challenges? The annual Dragos Industrial Security Conference (DISC) runs the first week of November 2022, where the Dragos team will be generating another CTF event to further educate leadership, asset owners, operators, or anyone looking to get hands-on experience working with ICS challenges. Keep an eye out for more information on registering for DISC and the Dragos CTF in the near future.
Related Posts
Top 5 Cybersecurity Threats to Oil & Gas, and How to Protect Against Them
How to Prioritize Vulnerabilities in Your OT Environment with Risk-Based Vulnerability Management
US Transportation Security Administration Releases Updated Pipeline Security Directive: Key Revisions and Compliance Strategies
Ready to put your insights into action?
Take the next steps and contact our team today.
