Use the page below for modules that are possible.
Empower OT cybersecurity teams with actionable, prioritized guidance to secure operations and maintain uptime.
Dragos offers a wide range of operational technology (OT) cybersecurity posture assessments, including Architecture Review, ICS Device and Application Vulnerability Assessment, ICS Network Vulnerability Assessment, and ICS Penetration Testing to help your industrial organization improve its cybersecurity defenses, reduce risk, and mitigate cybersecurity incidents. These assessments are typically the first step in our customers’ OT cybersecurity journey and provide a roadmap to a comprehensive strategy to reduce cyber risk and improve resiliency in their operations environment.
Why Choose Dragos WorldView?
Dragos WorldView Threat Intelligence is used in security operations centers (SOCs), board rooms, and the physical facilities of electric grids, oil and gas pipelines, water treatment and distribution, and manufacturing plants. By offering actionable insights tailored to the unique needs of operational technology (OT) environments and industrial control systems (ICS), Dragos WorldView helps security practitioners stay ahead of emerging adversary operations.
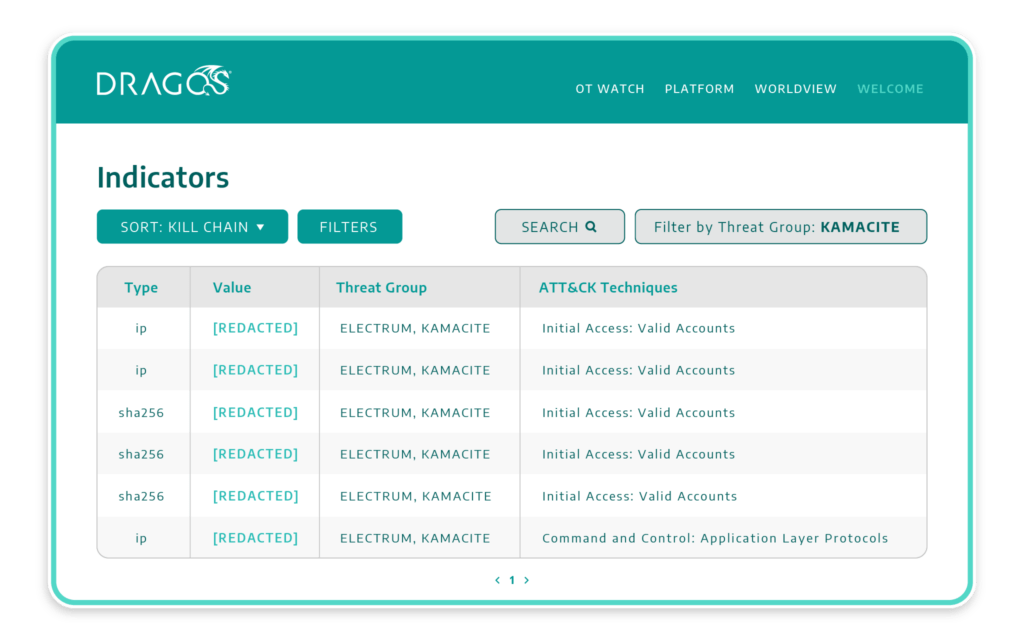
Integrate OT IOCs in Your SOC
IT-focused SOC staff have difficulty converting alerts into reduced risks for OT networks.
- Spot and block early-stage threats before they hit OT.
- Contextualize alerts for faster triage and investigations.
- Integrate and correlate in central SIEM, SOAR, TIP platforms.
Benefits of Dragos Assessment Services
CONTACT US




How Tabletop Exercises Work
What You Get
The exercise control package is considered the testing “control” and ensures that all participants receive exercise material in the same manner at the same time. The control package will detail rules of engagement and scenario content necessary for gameplay.
The narrative briefing is an interactive scenario briefing that will lead participants through mock investigations, analysis, discussions, and decisions. This will include scenario injects and artifacts.
A detailed report of continued best practices and findings that include recommended corrective actions, evaluation rating, and detailed planning considerations.
Penetration testing finds risks no tool can reveal.
What We Offer
Architecture Review
Evaluate Your Existing Security Program
- Assesses your existing OT cybersecurity posture, including detection and protection capabilities; mapped to the MITRE ATT&CK for ICS framework or other industry standards.
- Focuses on network architecture analysis, documentation review, and staff interviews to improve overall security of your ICS environment.
- Provides tactical and strategic recommendations to mature your organization’s ICS security program.
ICS Device and Application Vulnerability Assessment
Identify Risks to Industrial Assets
- Identifies vulnerabilities in ICS hardware or software.
- Provides visibility of risks to ICS environment.
- Provides prioritized recommendations to mitigate risks.
ICS Network Vulnerability Assessment
Close Gaps In Network Defense
- Evaluates protection, detection, and response capabilities that currently exist in your ICS environment.
- Identifies exploitable vulnerabilities in ICS environment.
- Provides action items to strengthen OT cybersecurity posture.
ICS Penetration Testing
Prevent Severe Breaches
- Leverages real-world attacker tactics, techniques, and procedures (TTPs) gained from intelligence.
- Identifies devices that could allow unauthorized access to critical ICS assets.
- Dragos Red Team demonstrates how attackers can move through ICS environments.
Readiness Assessment
Build a Foundation of Best Practices
- Incident response plan document review.
- Incident response C2M2 assessment.
- Best practices recommendations.
See the Dragos Platform in Action
Take the next step to protect your ICS environment now with a free demo
Control Loop: The OT Cybersecurity Podcast
See the Dragos Platform in Action
Take the next step to protect your ICS environment now with a free demo
