In the previous blog in this series, we covered the foundational elements that make up Neighborhood Keeper, as well as how the information-sharing program fits into the broader context of Cyber Threat Intelligence (CTI). As we move through the rest of the series, we’ll be taking a more in-depth look at many of the topics and concepts previewed in the initial overview. This installment focuses on analyzing trends observed in the Neighborhood Keeper data and methodologies for participants to operationalize operational technology (OT) threat intelligence in defending their own networks.
Putting Context Around Trending Observations
First and foremost, the trends available within Neighborhood Keeper’s data are useful for contextualizing events observed within your organization’s environment. In practice, this means looking at common or trending detections in your own environment and comparing them with the detection data available in Neighborhood Keeper.
A potential example of this may be a new detection that is trending within your environment. As an initial investigatory step, you can investigate if the same detection is trending within the Neighborhood Keeper data. If it is, some potential questions that could help extract insights out of the data available in Neighborhood Keeper are:
- Is this a short-term or long-term trend within the Neighborhood Keeper community?
- If it is trending on a more recent basis, could this be indicative of an ongoing adversary campaign? How could I confirm or refute this in my own environment?
- If it is a long-term trend in the Neighborhood Keeper data, have there been any recent updates or upgrades to your environment that might correlate with the analytic now trending in your environment? Does the detection give me some idea where to begin my investigation?
- Are there other Neighborhood Keeper community participants I could reach out to for additional insight? Potentially from the pool of Trusted Advisors?
These questions and considerations can help provide context and guide the subsequent investigation. While no detection should be dismissed without proper consideration, detections can have varying implications and should be considered in context, to include the timing, the environment in which the detection fired, and any data normalization factors.
An emergent detection consistent with specific, known adversary tactics, techniques, and procedures (TTPs) historically associated with initial access operations should be considered a priority for investigation. Conversely, a trending detection related to a dual-use capability you might already expect to see in your environment (for example, SMB-related detections) that is a longer-term trend in the Neighborhood Keeper data may be considered a lower priority.
Making it Easier to Visualize Trending Activity
Neighborhood Keeper has always provided participants with the ability to observe the most common threat analytics and indicators of compromise (IOCs), as well as their percentage change, over pre-defined time periods. However, this information was previously contained in multiple views or required flipping back and forth between multiple filters, which complicated the ability to visualize these trends and their changes in a single location. Accordingly, Dragos has implemented a new view within the Neighborhood Keeper portal that consolidates trending detections over time within a single, aggregated plane to enable exactly the types of investigations detailed above.
This new panel can be found on the main page of the Neighborhood Keeper portal. After logging in, a new “Trend Insights” tab is visible to the right of the previously available selectors for individual timeframes:
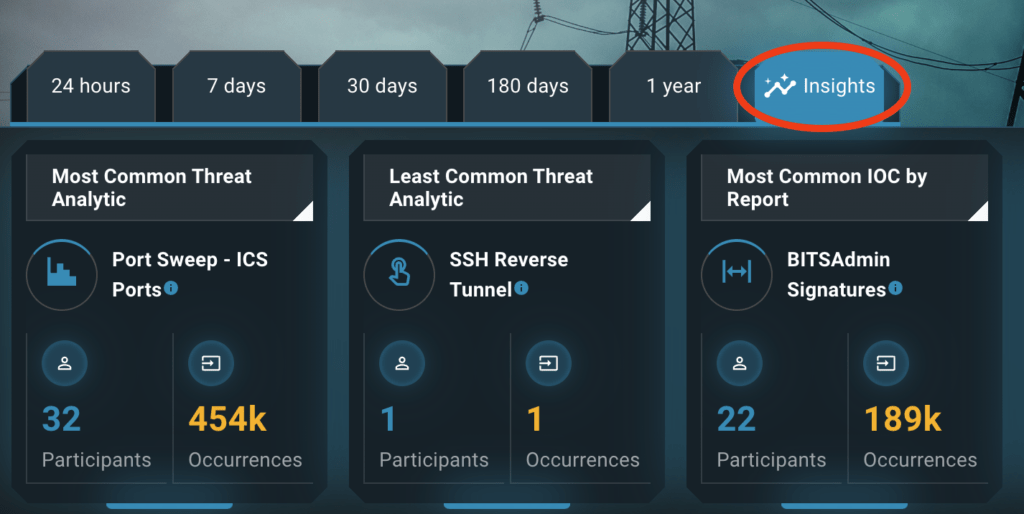
This new tab brings up tiles for the various trend insight categories, for example “Most Common Threat Analytic.” Clicking the tile itself brings into view stacked panels for 7, 30, and 180 days, which allows easy volume and trend observation for tracked threat analytics over defined timeframes:
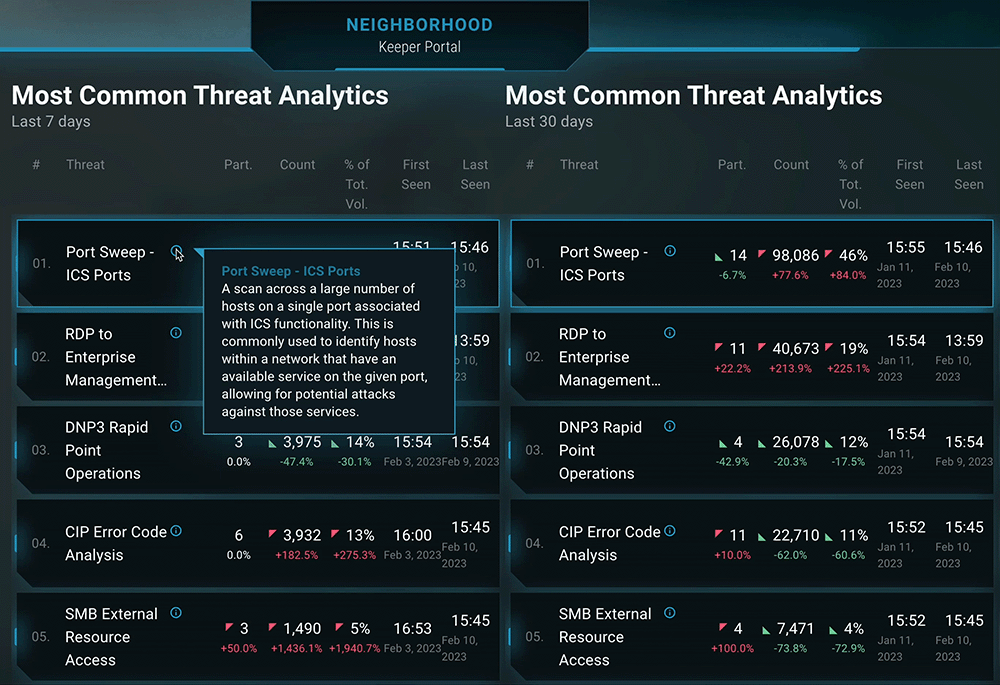
But backward-looking analysis isn’t the only use case for this new capability. Dragos has long been a proponent of applying the discipline of threat hunting to industrial environments. This is driven not only by the inherent limitations of relying on IOCs to detect ongoing malicious activity, but also the ability of a robust CTI program and regular hunts to significantly increase the maturity of an organization’s OT network defense.
Practical Examples of Trend Analysis in Neighborhood Keeper
Applying the discipline of trend analysis to develop informed threat hunting hypotheses can be a way to leverage Neighborhood Keeper’s information in a proactive manner for network defense. At its core trend analysis posits that future insight into any phenomena can be derived by examining past dynamics and that the longer the direction of any change is maintained, the signal that this change represents should be considered increasingly reliable. In the context of CTI and network defense, this means combining past knowledge of adversary behavior with emerging trends across our network and the larger community to identify and interdict adversary activity early in a new campaign.
As a practical example – an emerging trend is observed in Neighborhood Keeper of detections mapped to adversary reconnaissance within several participant OT networks, which is combined with knowledge of several recent attempted phishing emails reported by your company’s engineering staff.
One hypothesis that could be generated for this activity is that an adversary is using phishing emails to target specific company employees as a method of initial access to the enterprise IT network prior to pivoting into OT environments and performing reconnaissance. With this context in mind, the defender could conduct a focused threat hunt for adversary activity at the critical interconnects between their IT and OT networks, to include jump boxes, engineering workstations, or historians.
Another example could be detections observed which are associated with lateral movement trending within the Neighborhood Keeper data that are mapped to a specific adversary’s TTPs, but that similar activity has not yet been observed within your own environment.
A logical hypothesis related to this observation could be that the detections relate to an adversary campaign targeting the community, but that the adversary either hasn’t yet targeted the defender’s network or hasn’t reached the lateral movement stage observed in the trending Neighborhood Keeper detection. Accordingly, the defender might hunt for signs of any known initial access TTPs for the specific adversary, as well as more general techniques associated with initial access on the network to try to identify and disrupt the adversary before they can establish a sound foothold and begin pivoting through the network.
These are just a few of the potential use cases for leveraging trends within Neighborhood Keeper’s data. Neighborhood Keeper can provide a wealth of context for activity on your own network and across the broader community, and the recent updates to the portal implemented by the Dragos Neighborhood Keeper team aim to make this context more easily accessible for participants to speed analysis and decision making.
The next blog in this series will focus on Long Tail Analysis, and we look forward to continuing to provide Neighborhood Keeper participants strategies to extract maximal benefit from their involvement in the program.
Ready to put your insights into action?
Take the next steps and contact our team today.