The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a Binding Operational Directive (BOD) last week, requiring federal civilian executive branch (FCEB) agencies to make changes to their asset discovery, vulnerability detection, and reporting practices.
Operational technology (OT) and industrial control systems (ICS) are critical to the functions of both our federal government and Defense Department. CISA’s 23-01 BOD emphasizes the importance of asset and vulnerability management across both IT and OT – a critical component of any cybersecurity program.
Understanding the Requirements
The following requirements need to be in place by April 3, 2023:
- Perform automated asset discovery every 7 days. While many methods and technologies can be used to accomplish this task, at minimum this discovery must cover the entire IPv4 and IPv6 space used by the agency.
- Initiate vulnerability enumeration across all discovered assets, including all discovered nomadic/roaming devices (e.g., laptops), every 14 days, with privileged credentials. Where the capability is available, agencies must perform this same vulnerability enumeration on mobile devices and other devices that reside outside of on-premises networks. Any deviations need to be approved by CISA.
- Update vulnerability detection signatures within 24 hours of the last vendor-released signature update.
- Initiate automated ingestion of detected vulnerabilities into the CDM Agency Dashboard within 72 hours of discovery completion (or initiation of a new discovery cycle if previous full discovery has not been completed). CISA notes that agencies and CISA will jointly deploy an updated CDM Dashboard configuration that enables access to object-level vulnerability enumeration data for CISA analysts by April 3, 2023.
- Develop and maintain the operational capacity to initiate on-demand asset discovery and vulnerability enumeration to identify specific assets or subsets of vulnerabilities within 72 hours of receiving a request from CISA and provide the available results to CISA within 7 days of request.
In April 2023, October 2023, and April 2024, agencies must use an interface in CyberScope to provide CISA with a progress report that includes any obstacles, dependencies, or other issues (or agencies can work with CISA through the CDM program review process).
The Dragos Platform Enables Federal Agencies to Secure Operations and Meet Mission Requirements
The Dragos Platform, along with our threat intelligence and managed services programs, are carefully crafted and continuously updated to secure the world’s most critical infrastructures. We don’t build our offerings to match any directive or regulation, because our mission isn’t to meet requirements. Our mission is to safeguard civilization.
Thankfully, there’s a strong correlation between doing the right thing and meeting the expectations of governing bodies. As a result of strong security practices that are inherent within the Dragos platform, we are also able to ensure that our customers and partners can meet (and exceed) the ever-changing landscape of requirements across multiple industries.
| CISA BOD Requirement | How Dragos Helps Agencies Meet the Requirement |
| Automated asset discovery every 7 days | The Dragos Platform analyzes multiple data sources including protocols, network traffic, data historians, host logs, asset characterizations, and anomalies to provide visibility of your ICS/OT environment. Asset discovery is continuous – exceeding the requirements of this BOD. |
| Vulnerability enumeration across all discovered assets every 14 days | Dragos is the only ICS/OT cybersecurity company to provide corrected, enriched, prioritized vulnerability guidance that allows customers to manage the full lifecycle of specific vulnerabilities in their environment through continuous, automated collection and analysis. Organizations that have segregated ICS/OT networks will benefit from the vulnerability disposition tracking built-in to the Dragos Platform, alongside both remediation and mitigation guidance. |
| Update vulnerability detection signatures within 24 hours | The Dragos Platform was built for heavily regulated environments here any change must be validated, tested, and documented – even on a passive platform such as Dragos. Today, vulnerability information is published in knowledge packs; these knowledge packs deliver new protocol classifications, threat detections, and vulnerability information at once to minimize the amount of regulatory-required testing. |
| Initiate automated ingestion of detected vulnerabilities into the CDM Agency Dashboard within 72 hours of discovery completion | The Dragos Platform CentralStore provides consistent, centralized risk management and reporting – so you can easily transfer the information to the CDM Agency Dashboard. Both the Dragos Platform and CentralStore provide users with data visually, and through a robust API, allowing for ease of integration into existing workflows and processes. |
| Develop and maintain the operational capacity to initiate on-demand asset discovery and vulnerability enumeration | The Dragos Platform exceeds this requirement, while ensuring that the discovery of assets and the enumeration of vulnerabilities does not impact ICS/OT environments that cannot tolerate asset discovery scanning or active vulnerability enumeration. The Dragos Platform provides continuous monitoring and vulnerability identification – all while not impacting processes and assets under control. |
For more details on the Dragos platform and how we can help you secure your environment, download the Dragos Platform Datasheet.
For agencies who do not currently partner with us, Dragos experts remind you to ensure that the tools used to meet these requirements do not add increased risk to OT environments. This is especially critical for devices sensitive to changes in network utilization and interaction. And, as always, collaboration is critical – make sure agency leadership is engaging with asset operators and engineers when implementing anything that could impact production environments.
Implementing a Blended Active/Passive Asset Discovery and Vulnerability Detection Program Across IT and OT Networks
This BOD highlights several methods that can be used to perform asset discovery and vulnerability enumeration. These methods include both active (communications between a discovery tool and the target device across the network space) and passive (monitoring traffic and analyzing it for assets, communications protocols, and vulnerabilities). Both active and passive are valid methods and can achieve the goals of this BOD on enterprise IT networks.
ICS/OT systems require a more nuanced approach. Especially in more modern systems where the ethernet network is part of the control system, care must be taken not to alter the ICS/OT environment. Additionally, the risk of introducing technologies that can interact with ICS/OT systems must be carefully managed, both to prevent accidental outages and to avoid providing adversaries with a means by which to interact with the ICS/OT system directly.
Here are a few things to consider as you start this journey:
- Do I have an industrial DMZ that separates my IT from OT networks? If not, limit any active scanning only to subnets that are 100% known to only contain IT assets; use passive monitoring to validate the rest of the network space.
- Do I have IT assets that are dual use for both IT and OT? If so, separate these functions to separate physical machines if possible.
- Do my IT and OT environments share identity management/authentication services? If so, separate these services, one for IT and one for OT. In 2021, 100% of threat actor compromises leverages a shared authentication ecosystem to cross from IT into OT.
Once assets are properly segregated, the process of building a blended program is much simpler. By creating scanning boundaries that align with the IT/OT DMZ, not only is process safety and integrity maintained, but lines of effort and responsibility remain clear-cut between IT and OT teams.
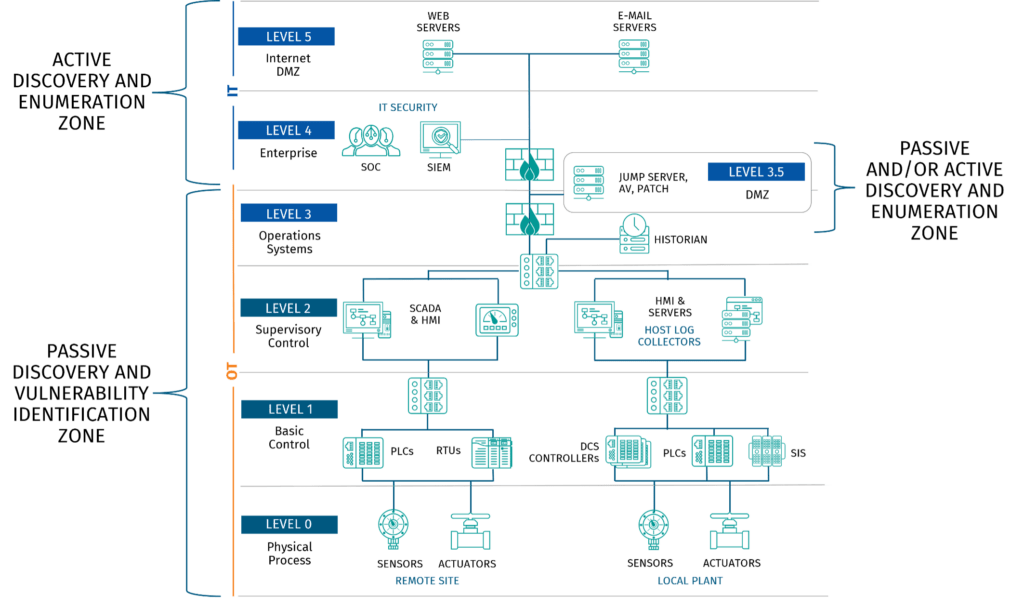
A common question as work progresses will be, “Can’t I actively interact with at least SOME assets in the OT environment?” The answer is, “It depends.” Always talk with your on-site asset operators who can guide you in making risk-informed decisions.
Ready to put your insights into action?
Take the next steps and contact our team today.
