Security analysts consistently get asked if there is a concern about an indicator of compromise (IOC) from a report months ago alerting in their dashboard. The answer is always, “it depends.” This blog addresses some of these concerns and discusses the end of life of an IOC.
There isn’t necessarily an end of life for an IOC. But, there is a network defense strategy to address IOCs. More on that later. But first, let’s talk about IOCs.
Denying IOCs to Adversaries
Many IOCs can be used to track adversary activities. The Pyramid of Pain created by David Blanco is a great diagram for tracking adversary activities, which states that “the relationship between the types of indicators you might use to detect an adversary’s activities and how much pain it will cause them when you can deny those indicators to them.”
We will be discussing the three indicators that are brought up most often by customers: hashes, IP addresses, and domains, which are circled in the figure below.
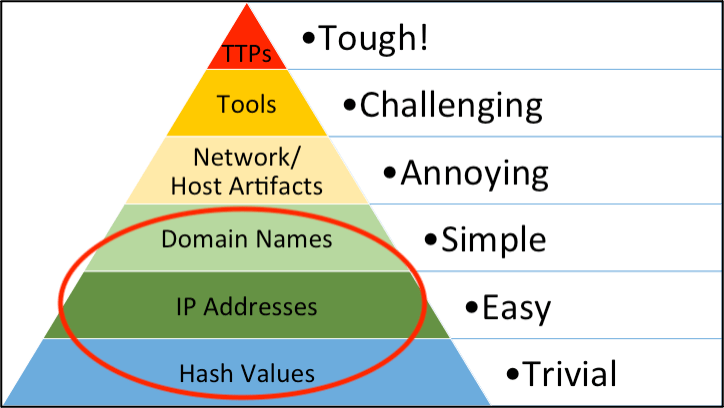
A file hash (MD5, SHA1, or SHA256, etc.) is a unique value that corresponds to a file—the file in these cases is a piece of malware. If you know the malware’s hash value, then typically detecting the malware on your network is “trivial.” However, keep in mind that its corresponding hash value will change if you flip one bit of the malware. This is one reason we have detection of malware behavior versus just detection of malware hash value.
An IP address identifies a device on the internet or local network. Detecting malicious IP addresses targeting a device on your network is “easy” if you have detections to identify this malicious activity. IP addresses are not a significant cost burden for the adversary, allowing them to move infrastructure when needed.
A domain is a string (i.e., dragos.com) tied to an IP address. Adversaries can have multiple malicious domains associated with an IP address or they can match one-to-one. Domains are the cheapest options for an adversary. Keep in mind that once a domain is malicious, it is malicious “forever”. There are, however, exceptions to this rule.
Burning IOCs
Some things can immediately lower the confidence of an IOC. Burning IOCs originate from the term burn notice, which means that an intelligence source is now unreliable. The first event that will burn IOCs is any public threat reporting.
The second common way IOCs will be burnt is by blocking IP addresses and domains. This tips the adversary that something has changed in their operations. Typically, an allow list versus a blocklist is preferred. However, this is not always possible.
Burning an IOC doesn’t mean the adversary will abandon that infrastructure permanently. In April 2021, we watched STIBNITE move infrastructure six times over a week, only to return to known infrastructure.
End of Life of an IOC
A common question we are asked is: When should I remove an IOC from my security information and event management (SIEM) system or similar? This answer will vary.
We recommend, when possible, not expiring IOCs but leveraging threat behaviors. All Dragos customers ingest IOCs differently and have different ways of validating and excluding irrelevant indicators. While Dragos cannot give a definite answer on how to use IOCs in every environment, here are some suggestions:
- IP addresses are valuable but very time-sensitive and can be considered a false positive, as adversaries vary their infrastructure – as we mentioned above. Think of IP addresses as having an expiration date. It is essential to ingest Dragos IOCs with a date filter to ignore IP addresses that are a year or even six months old. This can help clean indicator lists and ensure the most up-to-date information.
- Domains are more difficult because it depends on the specific domain. Dragos domain descriptions include additional context to help analysts triage whether they see the specific domains in question in their environment or not. This helps determine if the infrastructure was created by an adversary specifically for malicious activity or if it is a legitimate but compromised domain. However, in most cases, think of these domains as bad forever.
- File hash does not have an expiration date. Dragos reporting includes descriptions of malicious items associated with file hashes.
Leveraging IOCs While Avoiding Alert Fatigue
While behavioral-based detections have the highest fidelity for defenders, indicator-based detection allows for quick deployment of technical artifacts highly specific to a particular adversary. IOCs are useful when deployed efficiently to support cyber defense but can become a direct path to alert fatigue for the Security Operations Center (SOC) if not used with aptitude.
The first key to the successful leveraging of IOCs is building a set of trusted sources for your collection management framework (CMF). Identify trusted industry partners that track adversary targeting of your vertical and technology stack and begin to aggregate their feeds for ingestion internally. Expanding the scope of the collection too far beyond what is relevant to your organization can limit the value derived from IOCs associated with campaigns that pose the highest threat, so the definition of scope is critical here. Beyond the initial span of indicator sources, it is crucial to consider the intelligence producer’s confidence in the IOCs when leveraging them for alerting. Most intelligence providers will apply some sort of scoring metric to indicators, so identifying the appropriate strategy around the confidence of IOCs for your defenders is critical here.
An additional key focus point for leveraging IOCs in security operations is automation. Look behind the scenes into almost any security organization and you will find an overworked SOC. Manual triage of indicators leads to frustration and the question of time value in an already overtasked environment. Automating the ingestion, triage, and alerting of indicators can improve security operations, with timely response to potential nefarious activity on a network, with limited strain on human resources. A common high-value practice observed among Dragos customers is an automated weekly scan of relevant indexes in a SIEM or logging solution against active indicators aggregated from a properly scoped CMF. The SOC or Threat Intelligence team then assesses alerts from the weekly scan based on a pre-determined prioritization scoring. This once weekly, automated process limits the strain felt by playing whack-a-mole with new reporting containing IOCs that may be important to the organization, while also allowing for timely investigation and response to potential threats.
The final essential element to deriving value from IOCs is timely deployment. As detailed above, IOCs, like your groceries, can be thought of as coming with a “best if used by” date. This is not to say that every indicator “expires.” Adversaries can, and have, returned to legacy infrastructure used in historical campaigns to begin retargeting organizations. Burning of infrastructure comes with a cost to the adversary. Still, they must continue with their operational directives as they are discovered by defenders and reported on in the wild. Because of the shift in confidence levels that come naturally with IOCs, defenders should focus on their practical use in security operations when they are utilized. It is not uncommon for an analyst to query an indicator and find a hit on an endpoint. However, it is common that that indicator was most recently used by the adversary over a year ago and has now become benign even though it was picked up by AWS or Azure. Avoiding detections like this becomes a balancing act for defenders.
Conclusion
Indicators of compromise can be useful forensic artifacts, but there is never a one-size-fits-all solution to leveraging them. IOCs often have a time constraint to their usefulness and require some strategy to be used as a component of security operations. When an indicator match is identified in internal telemetry, defenders should first work to frame the validity of the detection by asking the following questions:
- What confidence level was reported by the source?
- When was this indicator last seen?
- Is this indicator associated with other threats to the organization?
- What is the threat model behind the indicator and what was the adversary attempting to accomplish?
As these questions are answered, defenders become more informed on potential next steps to investigating an event – and what the severity of the detection may be.
The Pyramid of Pain (shown above) should continue to be considered in detection and response strategy. While an IOC can be an easy, early indicator of adversary activity, the focus should always lie on the apex of the Pyramid: detecting adversary behaviors and tactics, techniques, and procedures. The reporting source of the IOC should always provide context around the campaign, to enable defenders to effectively investigate the detection and thereby cause the most pain to the adversary. This is a critical evaluation criterion to consider when looking for intelligence providers. Consider providers who deliver timely, relevant indicators in addition to complete, accurate intelligence on how the adversary operates.

Ready to put your insights into action?
Take the next steps and contact our team today.

