The ransomware threat ecosystem remained highly active in the second quarter, fueled by new groups, rebranding of existing entities, expansion of Initial Access Broker (IAB) operations, and social engineering techniques. Escalations in geopolitical tensions during Q2 introduced a new dimension to ransomware threats. Specifically, the Israel-Iran conflict in the Middle East spurred a rise in hacktivist personas employing ransomware to disrupt industrial operations and Iranian-based ransomware groups offering higher affiliate payouts for successful attacks on organizations in the U.S. and Israel.
In the second quarter (April – June) of 2025, Dragos identified 657 ransomware incidents impacting industrial entities worldwide, a decrease from the 708 incidents documented in Q1 2025. North America was the most targeted region in Q1 with 413 incidents and remained the top-impacted region in Q2 with 355 incidents. Though the quantity of observed incidents were down overall, three regions experienced an increase in incidents. Europe led the increase in incidents with 135 in Q1 and 173 in Q2. The Middle East saw an increase from 11 attacks in Q1 to 17 in Q2. Africa experienced the smallest increase, with 3 incidents in Q1 and 5 in Q2.
Manufacturing continued to be the most impacted sector, accounting for 65% of incidents recorded in Q2. The top manufacturing subsector impacted by ransomware was construction, accounting for 110 of the 428 manufacturing incidents in Q2. The electric sector saw a decrease in incidents from Q1 (15 incidents) to 3 incidents in Q2. The mining sector experienced 11 incidents in Q2, up from 2 incidents in Q1 2025 and 4 incidents in Q4 2024.
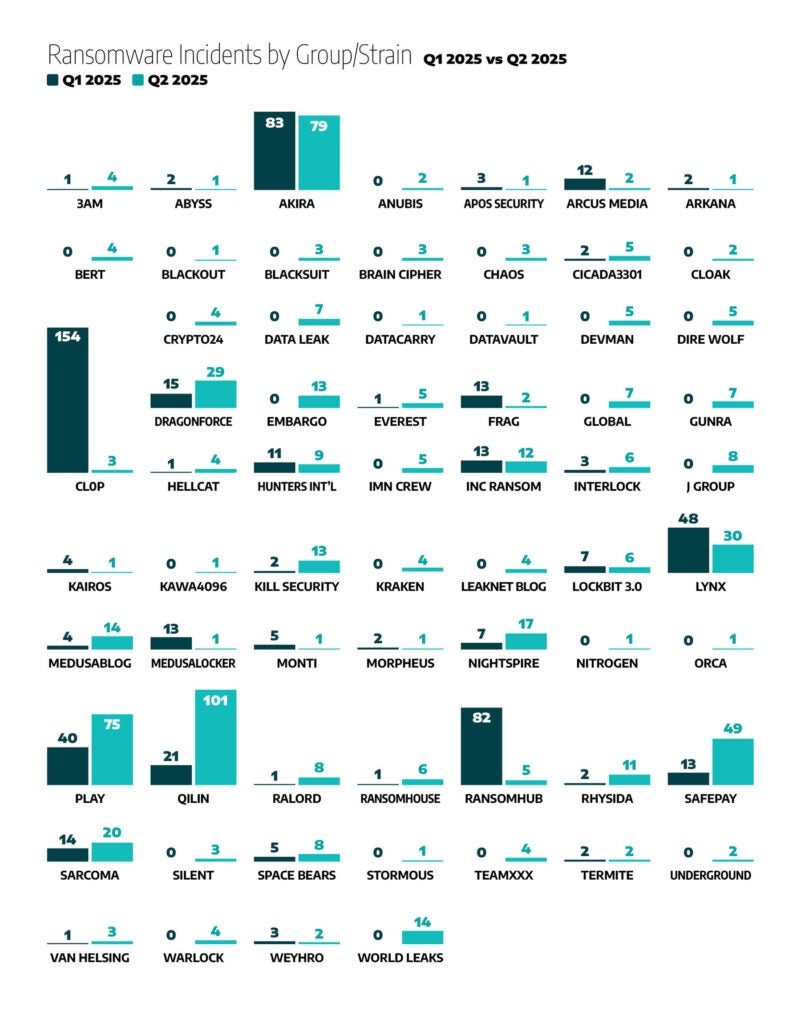
The RansomHub group dominated the ransomware landscape in 2024 and was one of the top three ransomware operations that impacted industrial organizations throughout 2024, alongside LockBit3.0 and Play. RansomHub was responsible for a mere 5 incidents in Q2, with no known victims since April 2025. Qilin was the most active group in Q2 with 101 incidents. CL0P ransomware accounted for 154 incidents in Q1 and only 3 attacks in Q1. CL0P’s dramatic surge in Q1 was driven by exploiting Cleo Managed File Transfer vulnerabilities (CVE-2024-50623, CVE-2024-55956), heavily impacting manufacturing and supply chains.
Q2 2025 also marked notable successes from international law enforcement, significantly reshaping the ransomware threat landscape affecting industrial organizations. Highlighted actions included Operation Endgame 2.0, a coordinated European operation dismantling critical ransomware infrastructure such as crypto mixers and dark-web marketplaces, thereby complicating ransomware groups’ financial operations. Additionally, the mid-May arrest by Moldovan and Dutch authorities of a DoppelPaymer ransomware affiliate, responsible for multimillion-dollar losses to European entities, further increased pressure on ransomware affiliates. This operational disruption likely accelerated affiliate migration observed from dormant groups like RansomHub to increasingly active operations such as Qilin.
Emerging Ransomware Groups
During Q2 2025, several new ransomware groups emerged, significantly escalating threats to industrial and enterprise organizations. These groups introduced innovative and adaptive tactics, techniques, and procedures (TTPs), creating complex new defensive challenges for cybersecurity teams. Newly identified ransomware groups impacting industrial sectors include:
- Gunra
- Dire Wolf
- Kraken
- Silent
- Anubis
- BERT
- Chaos
- Crypto24
- IMN Crew
- Kawa4096
- Underground
- Warlock
Qilin: Full-Spectrum Extortion Provider
In Q2 2025, Qilin significantly differentiated itself from other ransomware groups by evolving into a sophisticated, state-aligned threat group. Following disruptions within legacy ransomware ecosystems, particularly LockBit and RansomHub, Qilin swiftly solidified its position by aggressively recruiting displaced, highly skilled affiliates, culminating in control of approximately 19% of ransomware incidents impacting industrial organizations in Q2.
Notably, Qilin introduced unprecedented professionalization into its ransomware-as-a-service (RaaS) platform, including specialized legal advisory services to assist affiliates in maximizing negotiation leverage. Additionally, Qilin incorporated internal media and public relations teams (“journalists”) dedicated explicitly to shaping public narratives and intensifying psychological pressure against targeted victims.
Technically, Qilin distinguished itself by systematically exploiting critical vulnerabilities in widely deployed Fortinet products through automated tooling. This enabled rapid initial access, streamlined privilege escalation, and significant penetration depth within victim networks.
Perhaps most critically in March 2025, Qilin ransomware was adopted operationally by North Korea’s state-sponsored threat group Moonstone Sleet. This development signals a strategic pivot toward geopolitical influence operations, extending beyond purely financial extortion motives. Correspondingly, Qilin’s activity dramatically surged from 21 ransomware incidents affecting industrial organizations in Q1 to 101 incidents in Q2. This marked escalation underscores the group’s strategic commitment to impact industrial sectors, further solidifying Qilin’s emerging threat status.
Devman: High-Profile Targeting and Publicity-Driven Strategy
Devman ransomware notably intensified its strategic targeting of high-profile organizations within critical infrastructure and healthcare sectors. Devman explicitly directs affiliates to pursue large-scale organizations, setting revenue thresholds of $100 million for critical infrastructure and $50 million for healthcare entities, optimizing for maximum operational disruption and financial gain.
Technologically advanced, Devman transitioned rapidly from version 1.0 (C++) to version 2.0 (Rust), significantly enhancing stealth capabilities and operational efficiency. The group operates independently, employing sophisticated phishing campaigns, credential theft, brute-force remote desktop protocol (RDP) attacks, and exploitation of vulnerabilities in edge services to establish initial access.
Uniquely, Devman actively pursues media exposure and public narratives, strategically utilizing publicity to amplify psychological pressure on victims and reinforce its reputation in the cybercriminal landscape. Its disciplined, corporate-style internal structure emphasizes rigorous affiliate vetting and operational control.
Devman’s operational choices, targeted, sophisticated attacks, deliberate publicity strategy, and disciplined internal controls collectively position the group as a formidable threat. This strategic combination of technical depth, operational rigor, and narrative-driven psychological warfare presents significant challenges for defenders across industrial and critical infrastructure sectors.
SafePay: Aggressive Expansion and Double-Extortion Strategy
In Q2 2025, SafePay ransomware significantly accelerated its operations, emerging as a top ransomware group through aggressively impacting industrial sectors. The number of industrial sector victims notably increased from 13 in Q1 to 49 in Q2.
SafePay maintains centralized control, directly managing all attack phases from initial intrusion through negotiation, encryption, and data leaks. Likely derived from leaked LockBit, directly managing all attack phases from initial intrusion through negotiation, encryption, and data leaks. Likely derived from leaked LockBit 3.0 source code, its ransomware toolkit emphasizes modular flexibility and advanced double-extortion tactics, combining destructive encryption and extensive data exfiltration. 3.0 source code, its ransomware toolkit emphasizes modular flexibility and advanced double-extortion tactics, combining destructive encryption and extensive data exfiltration.
SafePay consistently exploits RDP and VPN vulnerabilities, using compromised credentials, weak passwords, and tools like Mimikatz, LOLBins, and custom lateral movement scripts for rapid privilege escalation. Notable incidents involved global entities like Ingram Micro, underscoring SafePay’s focus on impactful, high-profile targets across manufacturing, healthcare, construction, transportation, and technology sectors.
Ransomware Activity Trends and Observations
In Q2 2025, Dragos observed notable trends and developments in ransomware activity that continued to shape the industrial cybersecurity landscape. This section highlights operational shifts, key patterns, and critical observations that defenders must consider to proactively manage and mitigate ransomware threats.
Continued Exploitation of Critical Vulnerabilities
- SAP NETWEAVER Visual Composer. CVE-2025-31324 emerged in April 2025 as a high-value target for multiple malicious actors. Multiple groups pursued opportunistic attacks, aiming to deploy ransomware or gain access to sensitive enterprise systems for extortion. The involvement of groups like BianLian and RansomEXX reflects the continued interest in weaponizing high-profile vulnerabilities for financial gain. These developments emphasize the urgent need for organizations to immediately apply patches and monitor for suspicious activity.
- SimpleHelp RMM. Ransomware actors actively exploited unpatched SimpleHelp Remote Monitoring and Management (RMM) software in Q2. Ransomware groups like DragonForce leveraged CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728 to achieve remote code execution and privilege escalation in targeted environments. This vector has enabled actors like DragonForce to pivot from service providers to downstream victims in double extortion attacks.
- FortiGate Firewalls. The Qilin ransomware group launched attacks exploiting Fortinet vulnerabilities CVE-2024-21762 and CVE-2024-55591 between May and June 2025. These flaws enable authentication bypass and remote code execution on unpatched FortiGate and FortiProxy devices. Initial access in these intrusions was obtained using these vulnerabilities, resulting in the deployment of Qilin ransomware. CVE-2024-21762, patched in February 2025, remains a concern with a high number of exposed systems. The same vulnerability has been leveraged by other ransomware groups, including those deploying the SuperBlack strain of ransomware.
Ransomware with Built-in Wiper
Anubis is an emerging RaaS operation that advertises attractive monetization strategies and combines file encryption with file destruction. Combining RaaS with added monetization strategies, such as data ransomware and access monetization affiliate programs, Anubis is maximizing its revenue, potentially expanding its reach within the cybercriminal ecosystem. What further sets Anubis apart from other RaaS is that the ransomware has an optional wipe mode. This suggests Anubis can apply additional pressure to their victims during ransomware negotiations or even delete the files once the ransom is paid. The group has claimed attacks against a range of industries, including healthcare, engineering, and construction, across multiple regions, with two attacks against industrial organizations in Q2 2025.
Continuation of Tailored ESXi Ransomware Variants
Groups like Eldorado and Play have previously developed Linux lockers specifically to target VMware ESXi environments. These lockers encrypt critical virtual machine files while disabling active VMs, disrupting business operations with minimal pre-encryption dwell time. Other ransomware operations have followed suit, creating tailored ransomware to disrupt ESXi environments. In April 2025, a new ransomware variant called BERT emerged with the built-in ability to forcibly shut down ESXi virtual machines to maximize impact and disrupt recovery efforts. While BERT only accounted for 4 attacks on industrial organizations in Q2, this demonstrates a persistent effort by multiple ransomware operations to tailor attacks against virtual environments.
Impersonation of Help Desk Staff Leads to Ransomware Deployment
In Q2, Dragos observed an increase in IAB activities, including the use of an attack pattern first reported by Microsoft in May 2024 in connection with the threat group designated Storm-1811. In this pattern, the attacker uses “email bombing” to overload a targeted organization’s employee with unwanted emails, and then makes a voice or video call over Microsoft Teams posing as a tech support team member to deceive that employee into allowing remote access to their computer.
Affiliates of the Three AM ransomware group modified this attack pattern to use phone calls to spoof the phone number of the targeted organization’s IT departments. One reported attack included the deployment of a virtual machine to a compromised computer, providing the ransomware operators with an initial foothold hidden from the view of endpoint protection software. Organizations should educate staff on the exact ways IT support will contact them and which tools they will use to provide remote technical support, so they can recognize social engineering efforts.
Ransomware Impacts on Industrial Organizations
In Q2 2025, ransomware attacks continued to cause significant disruptions to industrial organizations, severely impacting operations, data integrity, and supply chains. The following incidents represent the most operationally impactful ransomware attacks affecting industrial sectors:
Nova Scotia Power
- Date: April 25, 2025
- Impact: Nova Scotia Power experienced a ransomware attack that disrupted power meters from communicating with the company’s billing systems. The incident resulted in company personnel manually taking meter readings or customers receiving estimated bills. Customers’ personal information was also taken by the unnamed attackers.
Nucor Corporation
- Date: May 13, 2025
- Impact: Steel manufacturer Nucor experienced a cyberattack that led to a temporary halt in production operations to contain and respond to the incident. According to the company’s SEC filing, an unnamed attacker exfiltrated a limited amount of data from the company’s compromised IT systems.
Masimo Corporation
- Date: May 6, 2025
- Impact: Medical technology company Masimo Corporation experienced unauthorized activity on its on-premises network, affecting manufacturing operations. As a result of the incident, some of Masimo’s manufacturing facilities were forced to operate below normal capacity, temporarily affecting the company’s ability to process, fulfill, and ship customer orders.
United Natural Foods (UNFI)
- Date: June 9, 2025
- Impact: Food distributor United Natural Foods (UNFI) experienced a cyberattack that forced the company to take some systems offline and operate at reduced capacity. The company experienced delays in processing customer orders throughout June 2025 due to recovery efforts related to its electronic ordering and invoicing systems. The company experienced delays in processing customer orders throughout June 2025.
Regional Impact Observations, Second Quarter of 2025
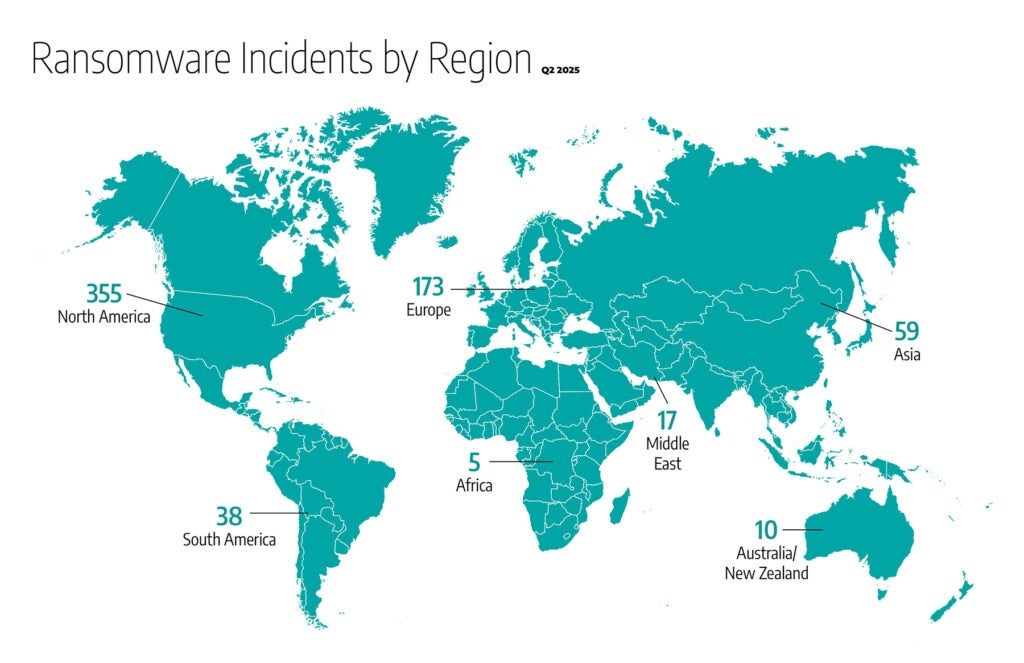
In Q2 2025, ransomware incidents underscored the diverse and pervasive nature of the threat landscape, continuing to affect numerous geographic regions and industry sectors. Manufacturing, transportation, and industrial control systems (ICS) equipment and engineering remained consistently impacted sectors. North America continued to experience the highest frequency of attacks, accounting for more than half of all global ransomware activity impacting industrial organizations.
- North America: Recorded 355 incidents, maintaining its position as the most impacted region, accounting for approximately 54% of global ransomware incidents. The United States and Canada remained primary targets, notably within manufacturing, transportation, and (ICS) equipment and engineering sectors.
- Europe: Reported 173 incidents, representing roughly 26% of global ransomware activity, a noticeable increase compared to 135 incidents (approximately 19%) in Q1. The United Kingdom, Germany, and Italy remained key impacted countries, with notable ransomware activity concentrated primarily in the manufacturing, transportation, and engineering ICS sectors.
- Asia: Documented 59 incidents, comprising approximately 9% of global ransomware activity. India and Japan remained significant targets, with incidents primarily impacting transportation, manufacturing, and telecommunications sectors.
- South America: Experienced 38 incidents, accounting for about 6% of global ransomware incidents. Brazil remained the most affected nation, with incidents primarily targeting transportation and manufacturing sectors.
- Middle East: Reported 17 incidents, representing nearly 3% of global ransomware incidents. The UAE and Saudi Arabia remained focal points, with attacks primarily targeting Oil and Gas (ONG) and manufacturing sectors.
- Oceania: Observed 10 incidents, accounting for approximately 1.5% of global activity. Australia remained the primary impacted country, with ransomware attacks primarily targeting manufacturing, industrial control systems (ICS), and ONG sectors.
- Africa: Recorded 5 incidents, comprising less than 1% of global ransomware incidents. South Africa remained the most prominently impacted, highlighting ongoing threats to industrial infrastructure despite limited reporting.
Industry Impacts, Second Quarter of 2025
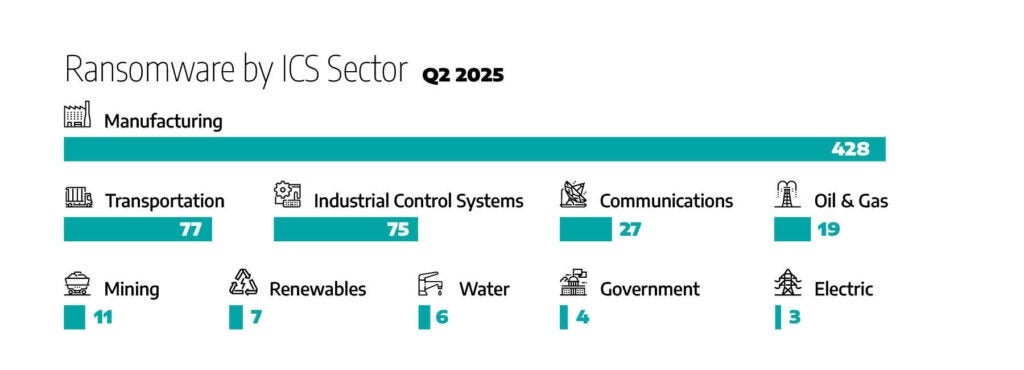
Ransomware incidents in Q2 2025 continued to significantly impact industrial organizations, reinforcing attackers’ sustained interest in critical sectors. Manufacturing remained the most heavily targeted sector, alongside consistent attention to transportation and industrial control systems (ICS) equipment and engineering.
- Manufacturing: Reported 428 incidents, accounting for approximately 65% of total ransomware activity, continuing as the most targeted sector despite a slight decline compared to 480 incidents in Q1.
- Transportation and Logistics: 77 incidents were documented, representing approximately 12% of total activity. This highlights persistent targeting, though it is lower compared to 108 incidents in Q1.
- Industrial Control Systems (ICS) Equipment and Engineering: Reported 75 incidents, comprising roughly 11% of total activity, marking a significant increase compared to 32 incidents in Q1, reflecting the heightened threat to this sector
- Communications: Recorded 27 incidents, accounting for approximately 4% of total activity, reflecting sustained attacker interest despite a decrease from 39 incidents in Q1.
- Oil and Natural Gas (ONG): Experienced 19 incidents, representing about 3% of total ransomware activity.
- Mining: Reported 11 incidents, reflecting continued attention to the sector, marking a notable increase compared to 2 incidents in Q1.
- Renewables: 7 incidents, up from 5 in Q1 2025.
- Water: 6 incidents, up from 2 in Q1 2025.
- Government: 4 incidents, down from 10 in Q1 2025.
- Electric: 3 incidents, down from 15 in Q1 2025.
As illustrated in Figure 3, Ransomware Incidents by ICS Sector, Q1 2025 vs. Q2 2025, ransomware activity impacting industrial sectors remained significant in the second quarter of 2025. Manufacturing continued as the most impacted sector, though slightly decreased compared to Q1, while incidents affecting Industrial Control Systems (ICS) experienced notable growth, becoming the second-most impacted sector, followed closely by transportation and logistics.
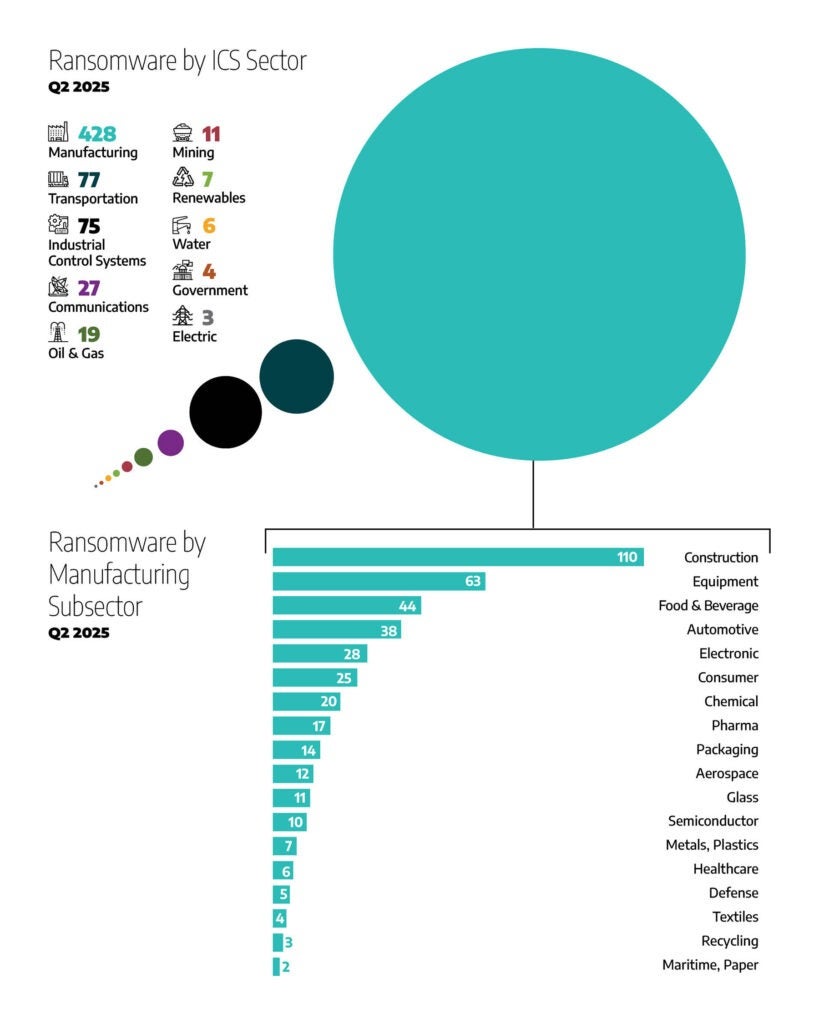
In addition to these primary industries and sectors, Dragos observed ransomware activity impacting multiple subsectors within Manufacturing (428 total incidents). The percentage breakdown, based on all manufacturing incidents, is as follows:
- Construction: 110 incidents (approximately 26% of manufacturing)
- Equipment: 63 incidents (15%)
- Food and Beverage: 44 incidents (10%)
- Automotive: 38 incidents (9%)
- Electronics: 28 incidents (7%)
- Consumer Goods: 25 incidents (6%)
- Chemicals: 20 incidents (5%)
- Pharmaceuticals: 17 incidents (4%)
- Packaging: 14 incidents (3%)
- Aerospace: 12 incidents (3%)
- Glass: 11 incidents (3%)
- Semiconductor: 10 incidents (2%)
- Metals: 7 incidents (2%)
- Plastics: 7 incidents (2%)
- Others (including Healthcare, Defense, Textiles, Recycling, Maritime, and Paper): The remaining percentage of manufacturing incidents is distributed in smaller numbers across these industries.
Ransomware Groups Trends, Patterns, and Observations, Second Quarter of 2025
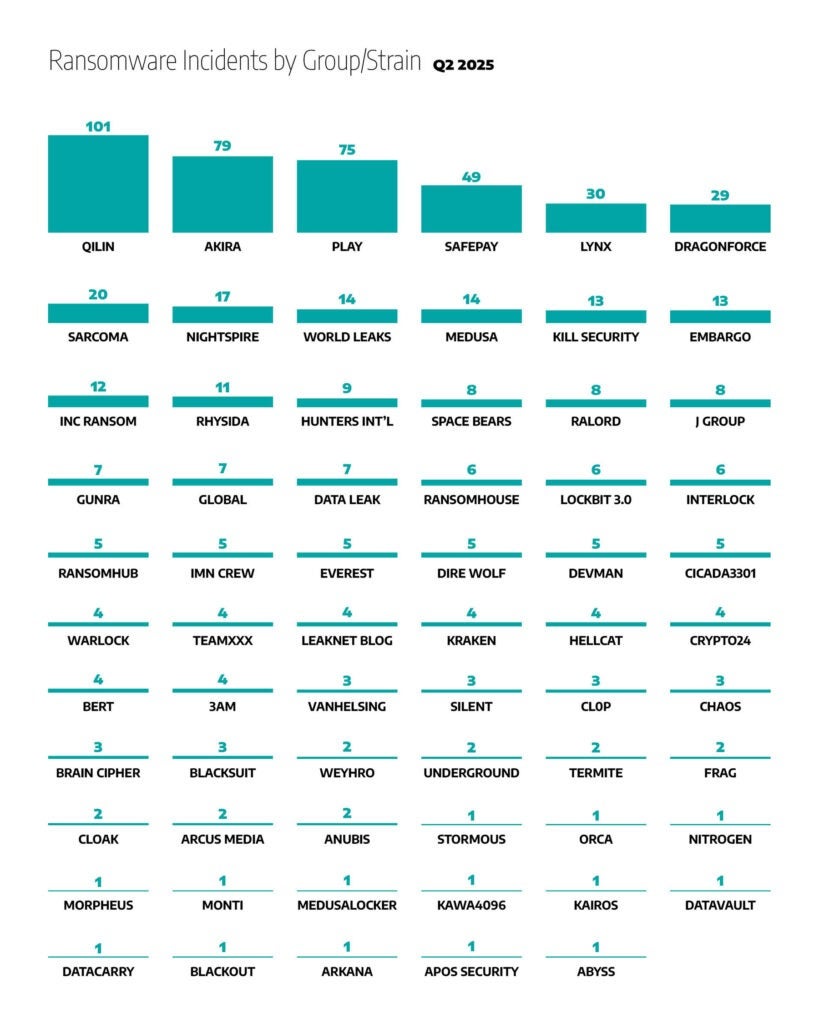
Dragos’s analysis of ransomware activity in Q2 2025 demonstrates ongoing fragmentation within the ransomware ecosystem. Established groups continued significant targeting alongside emerging groups, notably impacting industrial organizations. Key groups and their associated activities include:
- Qilin: Accounted for 101 incidents (~15% of global ransomware activity), significantly increasing from 21 incidents in Q1. Known for advanced tactics and associations with nation-state-linked operations, notably targeting critical infrastructure.
- Akira: Linked to 79 incidents (~12%), maintaining substantial activity with consistent targeting of manufacturing and transportation sectors through sophisticated phishing and multi-platform ransomware deployments.
- Play: Reported 75 incidents (~11%), nearly doubling from 40 incidents in Q1. Continued focus on critical infrastructure, leveraging zero-day vulnerabilities and compromised credentials.
- Safepay: Involved in 49 incidents (~7%), marking substantial growth from 13 incidents in Q1, using aggressive double extortion methods targeting industrial sectors.
- Lynx: Documented 30 incidents (~5%), decreasing from 48 incidents in Q1 but still maintaining impactful activity targeting manufacturing and logistics through double extortion.
- DragonForce: Recorded 29 incidents (~4%), increasing from 15 incidents in Q1, maintaining consistent targeting of supply chains within manufacturing and construction sectors.
- Sarcoma: Observed 20 incidents (~3%), continuing its double-extortion model, although slightly higher compared to 14 incidents in Q1, notably impacting electronics manufacturing supply chains.
- NightSpire: Reported 17 incidents (~3%), increasing from 7 incidents in Q1, utilizing double extortion methods against industrial organizations.
- World Leaks and Medusa: Each involved in 14 incidents (~2% each), reflecting sustained targeting, particularly focused on critical sectors.
- Kill Security and Embargo: Each accounted for 13 incidents (~2%), continuing targeted attacks using credential theft and double extortion.
- INC Ransom: Recorded 12 incidents (~2%), stable activity focusing on double extortion tactics and credential abuse.
- Rhysida: Reported 11 incidents (~2%), increasing significantly from 2 incidents in Q1, focusing on industrial targets.
- Hunters International: Documented 9 incidents, slightly decreasing from 11 in Q1, leveraging remote access vulnerabilities.
- Space Bears, RALord, J Group: Each reported 8 incidents, indicating consistent activity, particularly within industrial sectors.
- Gunra, Global, Data Leak: Each accounted for 7 incidents, contributing smaller-scale but persistent ransomware activity.
- RansomHouse, LockBit 3.0, INTERLOCK: Each involved in 6 incidents, indicating sustained activity despite varied external pressures.
- RansomHub, IMN Crew, Everest, Dire Wolf, Devman, Cicada3301: Each reported 5 incidents, reflecting targeted but reduced or stable activity compared to prior quarters.
- Warlock, TeamXXX, Leaknet Blog, Kraken, Hellcat, Crypto24, BERT, 3AM: Each recorded 4 incidents, maintaining limited but consistent activity across sectors.
- VanHelsing, Silent, CL0P, Chaos, Brain Cipher, Blacksuit: Each involved in 3 incidents, showing minor shifts in their ransomware activity levels.
- Weyhro, Underground, Termite, Frag, Cloak, Arcus Media, Anubis: Each documented 2 incidents, reflecting lower-level persistent threats.
- Stormous, Orca, Nitrogen, Morpheus, Monti, MedusaLocker, Kawa4096, Kairos, DataVault, DATACARRY, Blackout, Arkana, Apos Security, Abyss: Each accounted for 1 incident, representing minimal but notable contributions to the ransomware ecosystem.
The figure below highlights notable shifts in ransomware activity between Q1 and Q2 2025, underscoring the rapidly evolving ransomware landscape. Several ransomware groups significantly increased their activity levels during this period, while others exhibited decreased or relatively stable activity. Dragos continues to investigate whether newly observed ransomware entities represent entirely new groups entering the threat ecosystem or existing groups undergoing rebranding.
Looking forward, ransomware threats are poised to evolve rapidly, driven by increasingly sophisticated operational capabilities and strategic shifts. Industrial and critical infrastructure organizations will likely face intensified targeting through:
- The increased use of AI-driven phishing, malware evasion, and automated reconnaissance significantly enhances attack sophistication and reduces detection windows.
- More targeted, selective attacks combining financial extortion with operational disruption, particularly influenced by geopolitical dynamics, which may increasingly drive threat groups and hacktivist personas to align their operations with geopolitical objectives.
- Continued exploitation of vulnerabilities in interconnected IT-OT environments further highlights supply chain and remote access vulnerabilities as critical entry points.
- Persistent fragmentation of the ransomware landscape, with emerging and rebranded groups utilizing double or triple-extortion techniques that incorporate encryption, data theft, and destructive wiper capabilities.
To effectively manage these evolving risks, industrial organizations must adopt a strong, proactive cybersecurity posture. Prioritizing a zero-trust approach, implementing rigorous vulnerability management practices, enhancing detection capabilities with AI-driven tools, and ensuring segmented, resilient networks will be essential. Strengthening employee training to recognize and counter sophisticated social engineering attempts, maintaining secure offline backups, and regularly conducting incident response simulations will enhance organizational preparedness. Active collaboration through timely threat intelligence sharing and adherence to best-practice guidelines will further reinforce resilience against future ransomware threats.
By strategically preparing for increasingly selective, impactful ransomware incidents, organizations can mitigate operational disruption risks, safeguard critical assets, and maintain resilience in the face of an ever-evolving threat landscape.
References:
Pay2Key’s Resurgence – Morphisec
Qilin ransomware launched by Moonstone Sleet – Microsoft Threat Intelligence on X
SafePay ransomware: The fast-rising threat targeting MSPs – Acronis
Cleo File Transfer Vulnerabilities – SOCRadar
Operation ENDGAME strikes again: the ransomware kill chain broken at its source – Europol
Suspected DoppelPaymer Ransomware Group Member Arrested – SecurityWeek
CVE-2025-31324 Detail – NIST
ReliaQuest Uncovers New Critical Vulnerability in SAP NetWeaver – ReliaQuest
Ransomware Actors Exploit Unpatched SimpleHelp Remote Monitoring and Management to Compromise Utility Billing Software Provider – CISA
DragonForce actors target SimpleHelp vulnerabilities to attack MSP, customers – Sophos
Critical Fortinet flaws now exploited in Qilin ransomware attacks – Bleeping Computer
TRACKING RANSOMWARE : JUNE 2025 – Cyfirma
Anubis: A Closer Look at an Emerging Ransomware with Built-in Wiper – Trend Micro
BERT Ransomware Group Targets Asia and Europe on Multiple Platforms – Trend Micro
Threat actors misusing Quick Assist in social engineering attacks leading to ransomware – Microsoft
A familiar playbook with a twist: 3AM ransomware actors dropped virtual machine with vishing and Quick Assist – Sophos
Nova Scotia Power Cyber Incident – NSPower
Nucor Form 8-K – U.S. Securities and Exchange Commission
Masimo Form 8-K – U.S. Securities and Exchange Commission
UNFI Systems Update – UNFI
Ready to put your insights into action?
Take the next steps and contact our team today.

