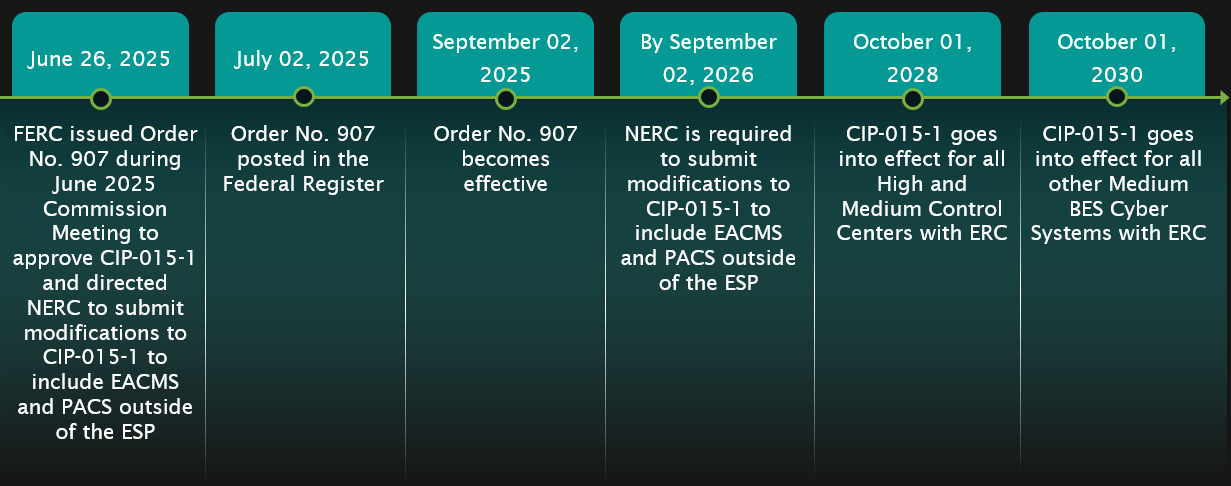
On June 26, 2025, the Federal Energy Regulatory Commission (FERC or the Commission) issued Order No. 907 1 formally approving North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Standard CIP-015-1, which will require Internal Network Security Monitoring (INSM) (east-west monitoring) for network traffic inside Electronic Security Perimeters (ESPs) across the North American electric sector.
FERC has also directed NERC to develop modifications to CIP-015-1 to increase the scope to include Electronic Access Control or Monitoring Systems (EACMS) and Physical Access Control Systems (PACS) outside of the ESP. NERC is required to develop and submit modifications within one year.
Registered Entities should begin aligning resources and internal plans to meet the CIP-015-1 requirements within the implementation timeline.
Join an upcoming webinar with Robert M. Lee, Co-Founder and CEO of Dragos and SANS ICS/OT Practice Lead, and Tim Conway, SANS ICS Curriculum Lead, where they will discuss how to get started with INSM and what effective INSM looks like.
What Is NERC CIP-015?
CIP-015 is a new NERC CIP standard that requires Responsible Entities to implement INSM of networks protected by the Responsible Entity’s ESPs of High Impact and Medium Impact Bulk Electric System (BES) Cyber Systems with External Routable Connectivity (ERC).
The goal of CIP-015 is to enhance visibility inside trust zones, where traditional preventive controls have limited reach. The standard reflects a shift from perimeter-only defenses to monitoring internal (east–west) traffic for signs of adversarial behavior.
At a high level, today’s NERC CIP-015-1 requirements include:
R1 – Collect, Detect, and Analyze Network Activity
- R1.1 – Implement, using a risk-based rationale, network data feeds to monitor network activity; including connections, devices, and network communications.
- R1.2 – Detect anomalous network activity using the network data feeds from R1.1.
- R1.3 – Evaluate anomalous network activity detected in R1.2 to determine if further action is required.
R2 – Retain INSM Data
Retain INSM data associated with anomalous network activity long enough to support the actions in R1.3.
R3 – Protect INSM Data
Protect all collected and retained INSM data from unauthorized modification or deletion.
Together, these requirements establish a framework for monitoring internal network activity, detecting anomalous behavior, and evaluating that behavior to determine if further action is needed.
Actions to Take Now
Framed in the SANS Buyer’s Guide to NERC CIP-015, the following prioritized steps are some of the most practical ways asset owners can begin preparing for CIP-015:
- Review current list of High Impact and Medium Impact (with ERC) facilities.
- Identify existing data collection capabilities within ESPs.
- Consider the feasibility of performing network activity data feed collection from existing network infrastructure.
- Identify where the analysis task of evaluating detected anomalous activity would be performed.
- Begin evaluating potential solutions that best fit in your environment.
- Prioritize projects across High and Medium Impact Control centers with ERC.
Compliance Evolution: What’s Likely to Change for CIP-015-2
Although FERC approved CIP-015-1, the Commission noted that it falls short of fully addressing the broader CIP-networked environment, as it limits coverage to within the ESP. As asset owners plan for CIP-015-1 implementation, they should also anticipate the expanded scope expected in version 2, which will include EACMS and PACS.
If EACMS and PACS outside the ESP aren’t monitored and are compromised, an adversary could use them to access other connected systems—like BES Cyber Systems inside the ESP—by posing as a trusted user or communication. Declining to extend INSM implementation to EACMS and PACS outside the ESP leaves a reliability gap because Responsible Entities will lack visibility into the high percentage of east-west traffic that occurs within the CIP-networked environment.2
FERC directed NERC to expand the scope of the CIP-networked environment in version 2 to go beyond just ESPs. FERC also provided clarification to help the industry better understand the intended meaning. The CIP-networked environment does not include an entity’s entire network. Rather, it includes systems within the ESP as well as one or more of the following: (1) network segments that are connected to EACMS and PACS outside of the ESP; (2) network segments between EACMS and PACS outside of the ESP; or (3) network segments that are internal to EACMS and PACS outside of the ESP.3
How Dragos Helps
The Dragos Platform was specifically designed to support INSM requirements. It offers advanced Network Security Monitoring (NSM) that delivers real-time monitoring, comprehensive detection of anomalous activity, and tools for analyzing internal network communications to inform response actions.
Unlike traditional perimeter-based solutions or general-purpose monitoring tools, the Dragos Platform is purpose-built for OT environments. It uses specialized OT-focused network data collection and analysis alongside four types of threat detection—including modeling-based detections, configuration detections, indicators of compromise, and behavioral detections. Integrated threat intelligence, structured playbooks, and case management enable both proactive and retrospective threat hunting. These capabilities support rapid, effective response to adversarial activity without operational disruption.
Whether you’re just starting to design your INSM strategy or scaling an existing implementation, Dragos supports utilities with both technology and expertise to help meet CIP-015 objectives securely and effectively.
What Early Adopters Have Learned: Dominion Energy Breaks It Down
Some organizations are already deep into this work. Dragos customer Dominion Energy is now monitoring across 450 substations in three states, with visibility into over 16,000 IP-enabled devices.
They built a dedicated OT SOC and prioritized INSM as a security-led initiative—with compliance as a natural outcome. Dragos worked closely with Dominion throughout this process, providing architectural guidance, sensor deployment support, and detection tuning to align with INSM goals. Dragos also supported the development of detection strategies tailored to Dominion’s OT protocols and helped the team operationalize their approach through training and incident response planning.
Dominion’s strategy was clear: pursue security outcomes first, well before compliance deadlines. As their case study highlights, they proactively identified the IT-OT security gap and pursued a solution that delivered real visibility and continuous monitoring across their OT infrastructure.
As Wes Futrell, Supervisor of Substation Technical Operations at Dominion Energy, said:
The key to success is thinking about deployment of internal network security monitoring as a project, not a product. Take a holistic approach with trusted vendors who understand your environment – don’t just buy a box and stick it in the station.”
That mindset—and partnership—positioned them well ahead of CIP-015.
Conclusion
CIP-015-1 introduces enforceable requirements for internal east-west traffic monitoring within ESPs, effective October 1, 2028. Meanwhile, CIP-015-2 is expected to expand INSM coverage to include systems like EACMS and PACS outside the ESP.
Collectively, these evolving requirements highlight the need for asset owners to address the CIP-015 requirements we know today and the expanded scope anticipated in CIP-015-2.
Building your INSM program isn’t just about compliance—it’s about operational resilience and visibility, where it matters most.
Hear from the Experts
1 Internal Network Security Monitoring for High & Medium Impact Bulk Electric Systems Cyber Systems, Order No. 907, 90 FR 28889, (July 2, 2025), 191 FERC ¶ 61,224 (2025).
2 See 191 FERC ¶ 61,224 at P 31.
3 See 191 FERC ¶ 61,224 at P 43.
Ready to put your insights into action?
Take the next steps and contact our team today.
