The SANS ICS Summit is one of the original ICS cybersecurity events, and 2021 marked its 16th year. The team at SANS is best known for its training courses, with additional community events like the ICS Summit focused on in-depth presentations to talk through contemporary challenges and solutions that ICS defenders face. At this year’s SANS ICS Summit Dragos was asked to develop a “capture the flag” (CTF) event that highlights an industrial control system (ICS) cybersecurity scenario. CTFs are a great way to learn, practice, and develop new skills and knowledge, not only as a red-teamer but also as a blue-teamer. They’re often designed to make participants think outside the box; developing a deeper understanding of accessible/non-accessible ports, network protocols, network communications, and often leverage user or system misconfigurations.
We chose to develop the CTF leveraging our expertise of the XENOTIME activity group, which is easily the most dangerous publicly tracked threat activity by Dragos. XENOTIME is responsible for ICS-tailored malware deployed against at least one victim in the Middle East in 2017, identified as TRISIS. TRISIS is notable because it targets Schneider Electric’s Triconex safety instrumented system (SIS), enabling the replacement of logic in final control elements. TRISIS is the first malware known to target safety instrumented systems that could have led to a human safety or loss-of-life event.

Dragos identified a change in XENOTIME’s behavior in February 2019. Our continued intel and analysis of common tactics, techniques, and procedures (TTPs) indicated that XENOTIME began to probe the networks of electric utility organizations located in the United States and elsewhere, which mirrored the activity group’s tactics against oil and gas companies in the Middle East.
Dragos developed the CTF using some of the TTPs associated with XENOTIME to create an event that allowed players to better understand the thought process of malicious activity groups upon discovery of an intrusion of an ICS-specific environment.
Dragos Capture the Flag: Defending SOGARD
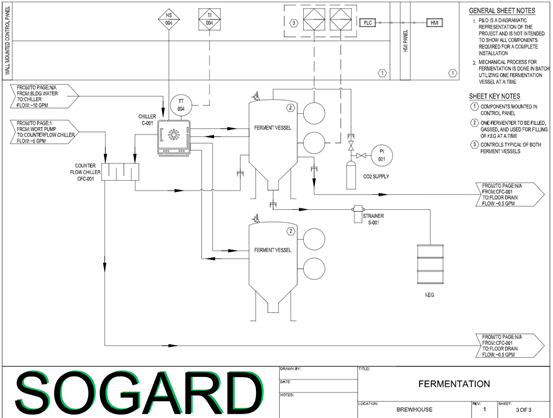
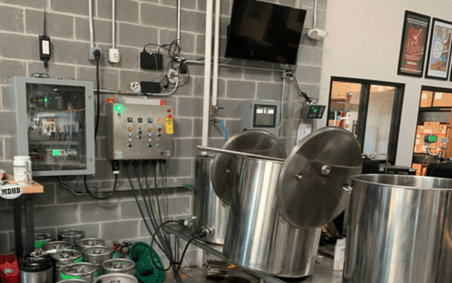
For the SANS ICS event, we leveraged the Dragos Brewery setup (SOGARD) located at our headquarters as the activity group target for the CTF. SOGARD is configured with an ICS range, so we could develop flags based on the actual processes in a brewery and the artifacts associated with them — including P&ID (Piping & Instrumentation Diagram) diagrams, Programmable Logic Controllers (PLCs), and engineering workstations (EWS). CTF participants will leverage common open-source tools to identify a variety of flags, all of which pertain to different aspects of the attack chain.
Scenario
Dragos realized an intrusion of its SOGARD brewery when it discovered its latest batch of the SOGARD 15% alcohol by volume (ABV) dark stout, “Dragon Fire”, came out as a 4% ABV ultra-light lager. Additionally, Dragos fears that their award-winning recipe for the SOGARD dark stout was exfiltrated during the intrusion and could be externally exposed.
The Dragos team has identified a new ICS-tailored malware that was deployed against the SOGARD brewery ICS range. The Dragos team identified the malware as BEERSIS as it is engineered to specifically target breweries.
Flag Creation
Once the team identified the techniques to reference, a target, and a scenario, it was time to address the creation of the flags. Each flag was created to provide a unique learning experience to the CTF participants, with each flag ranging from 1 point (easy) to 10 points (extremely hard).
The team considered the following when creating the flags:
- Any player of any experience level was able to participate, have fun, and maybe learn something whether they are currently working in the ICS space or not.
- The ability to use off-the-shelf protocol analyzers in Wireshark and open-source Lua protocol dissectors.
- Not the cool ones like Dragos’ spiffy CIP knowledge.
- Covered a wide spread of operating systems due to the variety often seen in ICS environments.
- Windows 7, Windows 10, Linux, Raspberry Pi, etc.
- Implementations with various communication protocols, Windows workstation artifacts, etc.
- Project files that directly relate to operating and maintaining a PLC.
- Modbus protocol traffic review to discover potential ARP-poisoning.
- Host-based asset discovery looking for rogue or unauthorized devices.
- Extracting a binary from a packet capture and reverse engineering it.
- All challenges must be solvable via open-source tools.
- Must provide real P&ID drawings for the active SOGARD brewery.
- Illustrates requirements for having multiple sources of information to solve a challenge.
- Educates Blue Teams on which common environmental misconfigurations activity groups could leverage to further their foothold and attack chain.
Closing Remarks
Dragos hopes that all the participants enjoyed playing in the 2021 SANS ICS Summit CTF event. While most of the challenges were designed to illustrate that activity groups like XENOTIME leverage simple misconfigurations, a handful of challenges were specifically designed to showcase the sophistication of such activity groups. Additionally, we wanted to add some forensic-based challenges while making some fun ICS puzzles for the community leveraging our Dragos brewery. Being able to put your hands on something and seeing how it works is the best way to learn and see how things work even if you are not directly involved in the ICS space.
Are you looking for more ICS-specific CTF events to increase your familiarity with the industrial workspace? Keep up-to-date with organizations like SANS ICS, S4 Events, and ICS-Village for new interactive content.
Ready to put your insights into action?
Take the next steps and contact our team today.

