Improving SOC Visibility into OT Using the Dragos App Integration with Splunk
Bridge the IT/OT divide by bringing OT/ICS cybersecurity data from the Dragos Platform into Splunk Enterprise Security to provide users with improved visibility and process efficiency resulting in more secure industrial operations.
Dragos OT Add-On for Splunk
Overview: The Dragos OT Add-on bridges the IT/OT divide by bringing OT cybersecurity data from the Dragos Platform into Splunk Enterprise Security. This integration brings a set of Dragos Platform capabilities into Splunk, enhancing visibility of OT environments by providing complete asset discovery, threat detection, and vulnerability management as well as enabling effective incident response.
This App provides users in-depth and context rich ICS/OT asset visibility so they can analyze multiple data sources within Splunk, including protocols, network traffic, asset characterizations, and anomalies to provide unmatched visibility of your ICS/OT environment.
How it Works: The Dragos OT Add-On can be installed and configured to connect to the Dragos Platform and ingest data into Splunk. You can then use the raw data to build queries and dashboards that provide value for your organization. This improved visibility, detection, and response capability gives security teams a blended IT/OT view allowing them to appropriately prioritize analysis and response activities.
How to Access: In order to take full advantage of Splunk’s OT capabilities, install both Splunk Enterprise Security and the Splunk OT Add-on. Once those apps are added to your environment you can then connect the Dragos Platform to Splunk Enterprise Security by adding and configuring the Dragos OT Add-On. Once configured, Dragos asset and alert data will flow into Splunk Enterprise Security. This provides integration with Splunk’s Asset Framework, advanced pre-built dashboards, and security alerting.
Improving OT Asset Visibility with Splunk
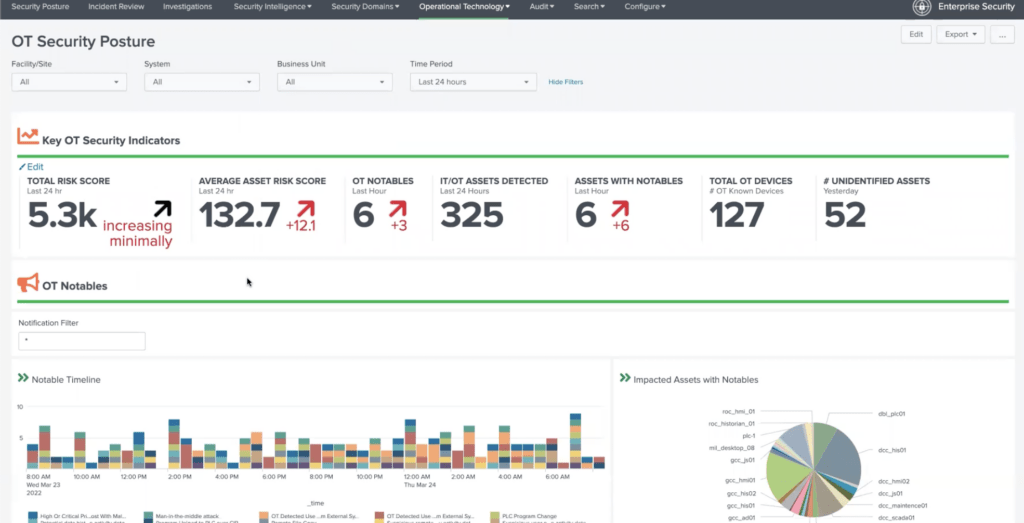
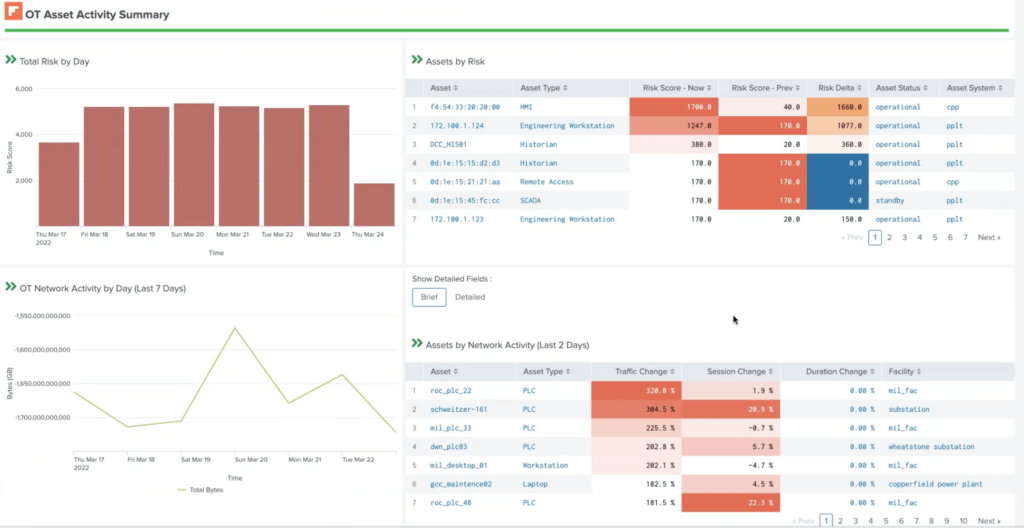
Once the Dragos Platform is installed into your OT network your SOC will have visibility into the industrial assets on the network (PLC’s, HMI’s, DCS, SCADA systems, etc.). The Dragos Platform’s asset inventory and visibility capabilities provide the industry’s most comprehensive and in-depth understanding of ICS environments, that includes comprehensive inventory of assets, devices, and details leading to faster triage of incidents through timeline analysis allowing Splunk users to group assets by zone to identify unexpected traffic.
Enhancing ICS Threat Detection with Splunk
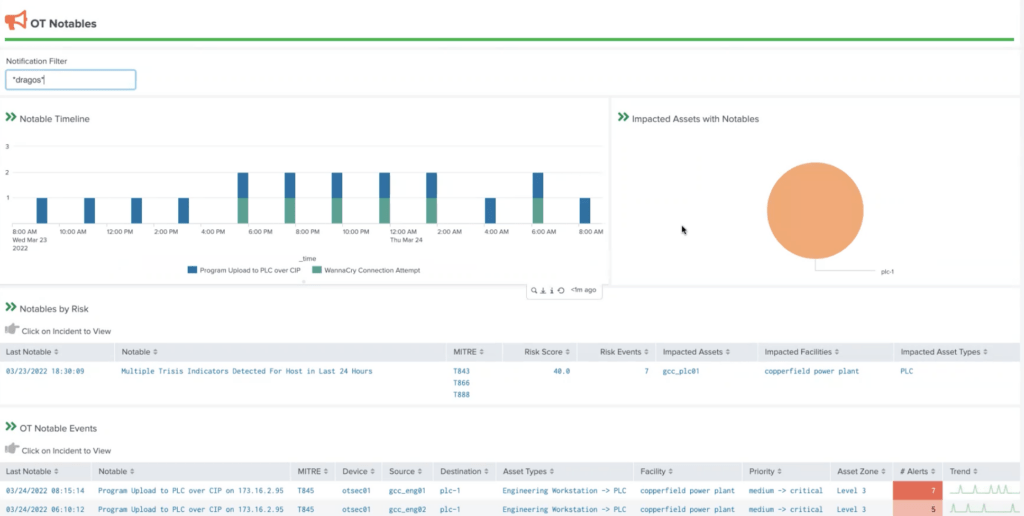
Once Splunk users have accessed OT asset inventory and visibility, the Dragos Platform provides proactive threat detection, threat response, and recovery capabilities. Notifications from the Dragos Platform are shared through the Splunk integration where they can be categorized by their associated detection type and severity allowing focused prioritization on what’s most important.
Enable Threat Intelligence with Splunk
Provide an easy and automated way of visualizing OT-focused threat intelligence Indicators of Compromise (IOCs) from the Dragos Platform directly in Splunk to automate and give the ability to detect across existing collected data. This enables defenders to easily detect known malicious activities in network traffic, domains, and applications.
Download Dragos OT Add-On for Splunk
Download the Dragos OT Add-On to improve visibility, detection, and response capabilities within Splunk.
Note: All of the above capabilities require an active deployment of the Dragos Platform. Threat Intelligence capabilities require an active Dragos Worldview Threat Intelligence subscription.
Dragos Apps for Splunk
| Capability | Dragos OT Add-On |
|---|---|
| Asset Inventory | X |
| Asset Visibility | X |
| Asset Zones | X |
| Asset Investigator | X |
| Visibility of Alerts | X |
| Alerts (4 Types) | X |
| Worldview IOC API | X |
| Visualization of IOCs | X |
| Vulnerability Management | X |
| Maps Dragos Data to Splunk Data Model | X |
| Requires | • The Dragos Platform • Splunk Enterprise Security |
Learn how to better protect your ICS environment with Dragos and Splunk.