Our annual 2022 ICS/OT Vulnerability Briefing webinar featured insights from Dragos vulnerability researchers Logan Carpenter and Nick Cano. This webinar highlighted the growth of industrial control systems (ICS) advisories year over year, and the ongoing challenge of prioritizing and mitigating vulnerabilities that lack viable alternatives to patching. This blog summarizes the vulnerability trends and topics from Dragos’s 2022 ICS/OT Cybersecurity Year in Review report, as well as some of Dragos’s most significant malware and vulnerability research from the same year.
Trends in ICS/OT Vulnerabilities Reported in 2022
According to an independent analysis by SecurityWeek, Dragos reported the highest number of vulnerabilities affecting ICS and operational technology (OT) last year, a total of 2,170 individual CVEs in 2022, which represents a 27 percent increase compared to 2021. Dragos reports on ICS/OT vulnerabilities from numerous individual vendors and researchers globally, including advisories from CISA, Germany’s CERT@VDE, and Japan’s JP-CERT, and NIST. In addition, Dragos vulnerability researchers discover new vulnerabilities which are added to the count.
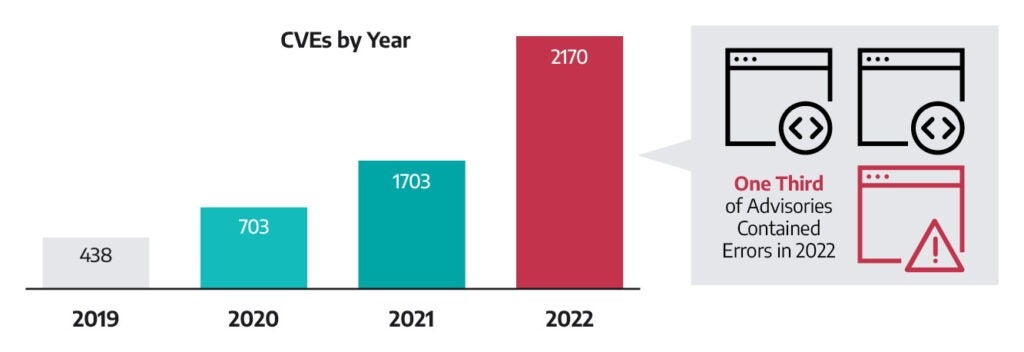
For all newly disclosed ICS/OT vulnerabilities, Dragos independently assesses, confirms, and often corrects CVSS scores based on the severity of the OT impact, ease of exploitation, and usage in the wild. Last year, a full 34 percent of the advisories that Dragos analyzed contained errors, and 14.9 percent of their CVEs had errors in the Common Vulnerability Scoring System (CVSS) scores associated with them. Of all the CVEs that Dragos analyzed in 2022, Dragos gave a higher severity score to 70 percent of CVEs than they had received at publication. Dragos gave a lower severity score to 29 percent of CVEs.
Avoid the Exploitation & Impact of ICS Vulnerabilities
Dragos assesses vulnerabilities based on how easy and how often they are exploited by adversaries and the impact of successful exploitation in ICS/OT environments. Of the vulnerabilities that Dragos looked at in 2022, 15 percent of the vulnerabilities were bordering the enterprise and 83 percent were located deep within the ICS network, meaning they apply to equipment on Levels 0 to 3 of the Purdue Model. This includes engineering workstations, PLCs, sensors, and industrial controllers. Exploiting vulnerabilities deep within the ICS network requires that adversaries have initial access, which requires additional steps but can lead to more direct physical impacts. Loss of control and loss of view are among the worst operations scenarios in an ICS/OT environment. In 2022, 50 percent of the advisories that Dragos analyzed could cause both a loss of view and loss of control in an OT system.
Practice Risk-Based Vulnerability Management
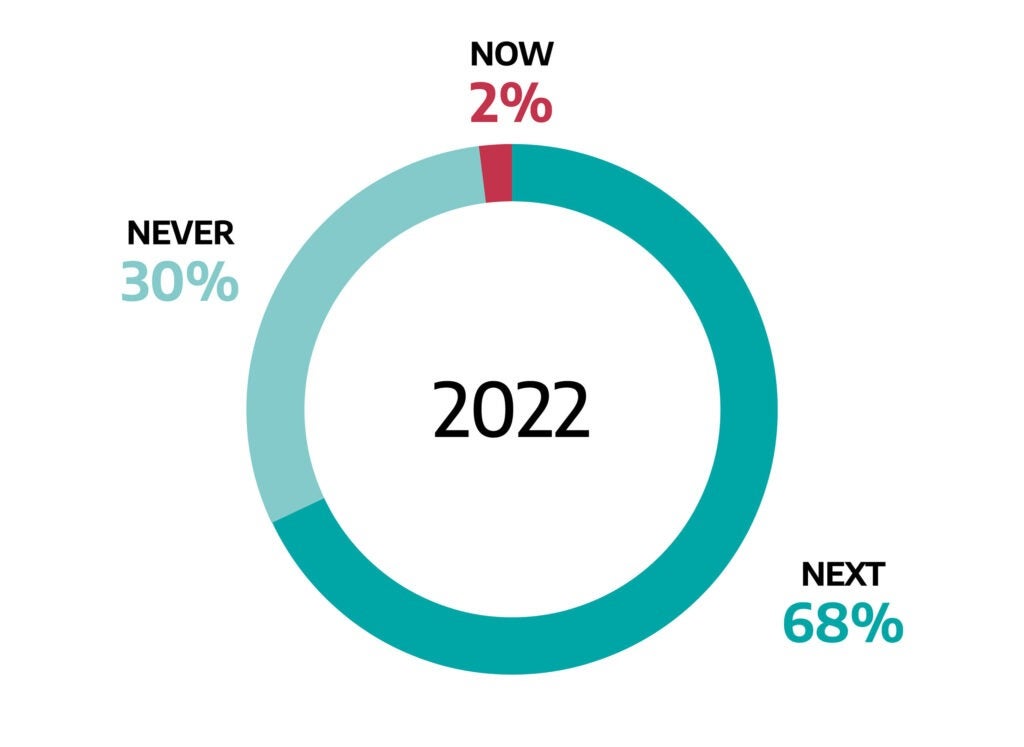
Dragos categorizes all ICS/OT vulnerabilities by Now, Next, and Never to help avoid wasting resources on unnecessary remediation and focus asset owners and defenders toward their most critical risks.
Only 2 percent of ICS/OT vulnerabilities in 2022 need to be addressed NOW.
- These are perimeter-facing, network exploitable vulnerabilities.
- They should be addressed as soon as practicable.
68 percent of vulnerabilities need to be addressed NEXT.
- These are possibly network exploitable but reside deeper within the network.
- They take more effort and knowledge to exploit.
- They take mitigated with network segmentation, by securing internet-accessible networks, especially when combined with MFA.
30 percent of vulnerabilities likely NEVER need to be addressed.
- Possible threat but rarely requires action.
- Monitor these for signs of exploitation.
Dragos recommends conducting a vulnerability assessment as the first step to identifying network and device vulnerabilities in specific ICS/OT environments, as well as helping to structure risk mitigation steps and cybersecurity program definitions.
To Patch or Not to Patch ICS/OT Vulnerabilities
Identifying and prioritizing vulnerabilities is just part of the battle, ICS/OT asset owners and defenders still need to know what to do. The problem is that of the vulnerabilities Dragos analyzed in 2022, despite 70 percent of advisories having a patch when announced, still 77 percent of vulnerabilities contained no practical mitigation from either the vendor or the CNA. The standard information technology (IT) approach to vulnerability mitigation is to patch fast and often, but in operational technology environments, patching can do more harm to operations than good. In fact, it often requires system and plant shutdowns. There are only some cases where it makes sense and patching is rarely an immediate option.
To make that easier in industrial environments, Dragos WorldView Threat Intelligence delivered analyst-driven mitigation advice for 53 percent of vulnerabilities that contained no mitigation from either the vendor or the CNA. This advice is critical for network defenders if they are unable to apply any available patches or if no patch was provided.
Focus: ICS/OT Malware Capability Developments
In 2022 Dragos analyzed new adversary capabilities developed, and in some cases deployed, with the potential to disrupt, degrade, or destroy the operations of electric grids, oil pipelines, water systems, and manufacturing plants, placing human populations at risk if critical services are not available.

PIPEDREAM: Sophisticated ICS/OT Attack Framework
In April of 2022, Dragos and a partner announced the discovery of PIPEDREAM — a cross-industry iICS attack framework developed by the threat group CHERNOVITE explicitly to attack industrial infrastructure. Dragos identified and analyzed PIPEDREAM’s capabilities through our daily business and in collaboration with various partners in early 2022. PIPEDREAM is the seventh known ICS-specific malware, and the fifth malware specifically developed to disrupt industrial processes. Given the right operational conditions, PIPEDREAM could be used for destructive effects, but it was found before it was employed.
Initially developed to compromise devices used in the electric industry, as well as oil and gas, PIPEDREAM represents a new evolution in malware development as the first cross-industry scalable ICS malware with disruptive and destructive capabilities. Dragos analyzed the five modules bundled in PIPEDREAM with the following capabilities:
 | Remotely interactive utility designed initially to discover, assess, manipulate and disable specific Schneider Electric PLCs and motion controllers. EVILSCHOLAR contains an extra CODESYS library which expands its impact beyond the devices and industries initially targeted. |
 | Remotely interactive utility designed to scan, identify, interact with, and manipulate targeted Omron PLCs. Omron targets are primarily the NJ/NX-series controllers and the required equipment for connecting to the network. |
 | MOUSEHOLE uses an OPC UA library to enumerate OPC UA servers and read/write node attribute data which then in turn controls the target devices. It can also brute force the server. |
 | One of two Windows components, DUSTTUNNEL is a remote operational implant to perform reconnaissance and command-and-control in IT networks. |
 | This module is a user-mode Windows executable that drops and exploits a vulnerable ASRock driver to load an unsigned, adversary compromised driver. |
DUSTTUNNEL and LAZYCARGO collectively demonstrate that CHERNOVITE is capable of an end-to-end attack and achieving Stage 1 of the ICS Cyber Kill Chain in IT environments. EVILSCHOLAR, BADOMEN, and MOUSEHOLE demonstrate CHERNOVITE’s capabilities to execute an ICS attack and impact in OT environments. Each module can be used independently or collectively, and it is flexible enough to repurpose again and again in different environments and different industries.
For more information, read our whitepaper, “PIPEDREAM: CHERNOVITE’s Emerging Malware Targeting Industrial Control Systems.”
INDUSTROYER2: Purpose-Built Substation Disruption Capabilities
Industroyer2 is the sixth known ICS-specific malware and is associated with the ELECTRUM threat group. A trimmed down variant of the CRASHOVERRIDE malware that was previously used in a 2016 incident, INDUSTROYER2 it is the first time that an ICS-specific malware has been reconfigured and then redeployed in an electric utility environment.
INDUSTROYER2 exploits the International Electrotechnical Commission (IEC) IEC-104 protocol to control and communicate with industrial equipment causing disruptive effects. Designed to switch physical breaker statuses from open to closed or vice versa, INDUSTROYER2 was set to execute via a scheduled task on a system to shut down a power grid substation in Ukraine. Though the attack was unsuccessful, the targeted substations and IOA information contained within the configuration information indicate that ELECTRUM likely had a detailed understanding of the victim’s environment before deploying INDUSTROYER2.
Trojanized Password Cracker Software for PLCs
Malware used to compromise industrial infrastructure does not need to be complicated or ground-breaking. Sometimes, it can even hide in plain sight. Last year, Dragos identified multiple social media accounts that are selling programmable logic controller (PLC) password cracking software that is trojanized with malware. One sample alone contained 44 exploits targeting various systems. The malware successfully obtains PLC passwords by sending a malicious serial request, however, unbeknownst to the user, it also installs a variant of Sality.
Trojanized software is a common delivery technique for malware and has been proven effective for gaining initial access to a network. Installing software from an unknown actor introduced significant and unnecessary risk into the OT environment. Sality is a peer-to-peer botnet for distributed computing tasks such as password cracking and cryptocurrency mining.
The adversary, in this case, has the capability to disrupt industrial processes – a Sality infection could risk remote access to an Engineering Workstation (EWS) by an unknown adversary, for example. However, Dragos assesses with moderate confidence that their motivation is financial and may not directly impact OT processes.
For more information, read our blog, “The Trojan Horse Malware & Password “Cracking” Ecosystem Targeting Industrial Operators.”
Forward Look: Strengthen Your Vulnerable Systems Against Exploitation
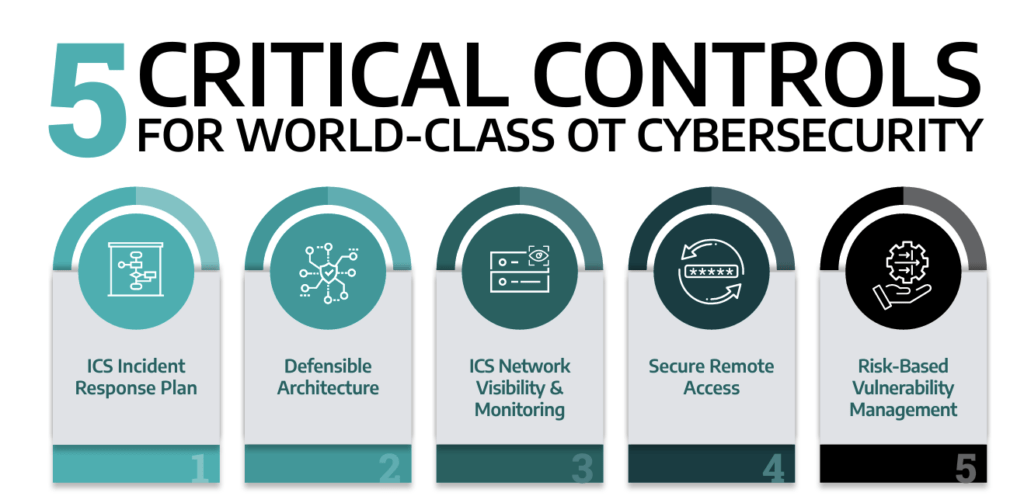
Dragos recommends 5 critical controls for OT cybersecurity identified by the SANS Institute for a baseline framework to help defend against malware threats and vulnerability exploitation deep within your ICS/OT environment.
Watch our on-demand ICS/OT Vulnerability Briefing for expert insights and perspectives on risk-based prioritization in industrial environments.

The 2022 Year in Review
Ready to put your insights into action?
Take the next steps and contact our team today.